Stream the Webinar on demand HERE
In a dramatic sequence of events, the LockBit ransomware group, known for its #1 spot in ransomware, has showcased a remarkable capacity for resilience and adaptability, despite significant law enforcement actions aimed at dismantling its operations. Recent developments reveal LockBit's prowess, the challenges of combating cybercrime, and the evolving landscape of cybersecurity threats.
See our previous post on the takedown of LockBit
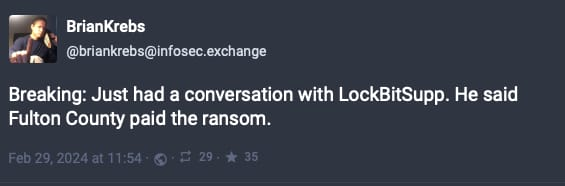
The FBI's takedown of LockBit came at a critical moment as the group was preparing to release sensitive data stolen from Fulton County, Georgia's government computer systems. This data, allegedly including documents tied to high-profile legal matters, including president Donald Trump and potentially jeopardizing numerous trials. This action underscores the grave risks associated with ransomware attacks and their impact to politics. Despite LockBit's initial setback, the group's vow to regroup and its threats to release the stolen data highlight the persistent challenge of ransomware.
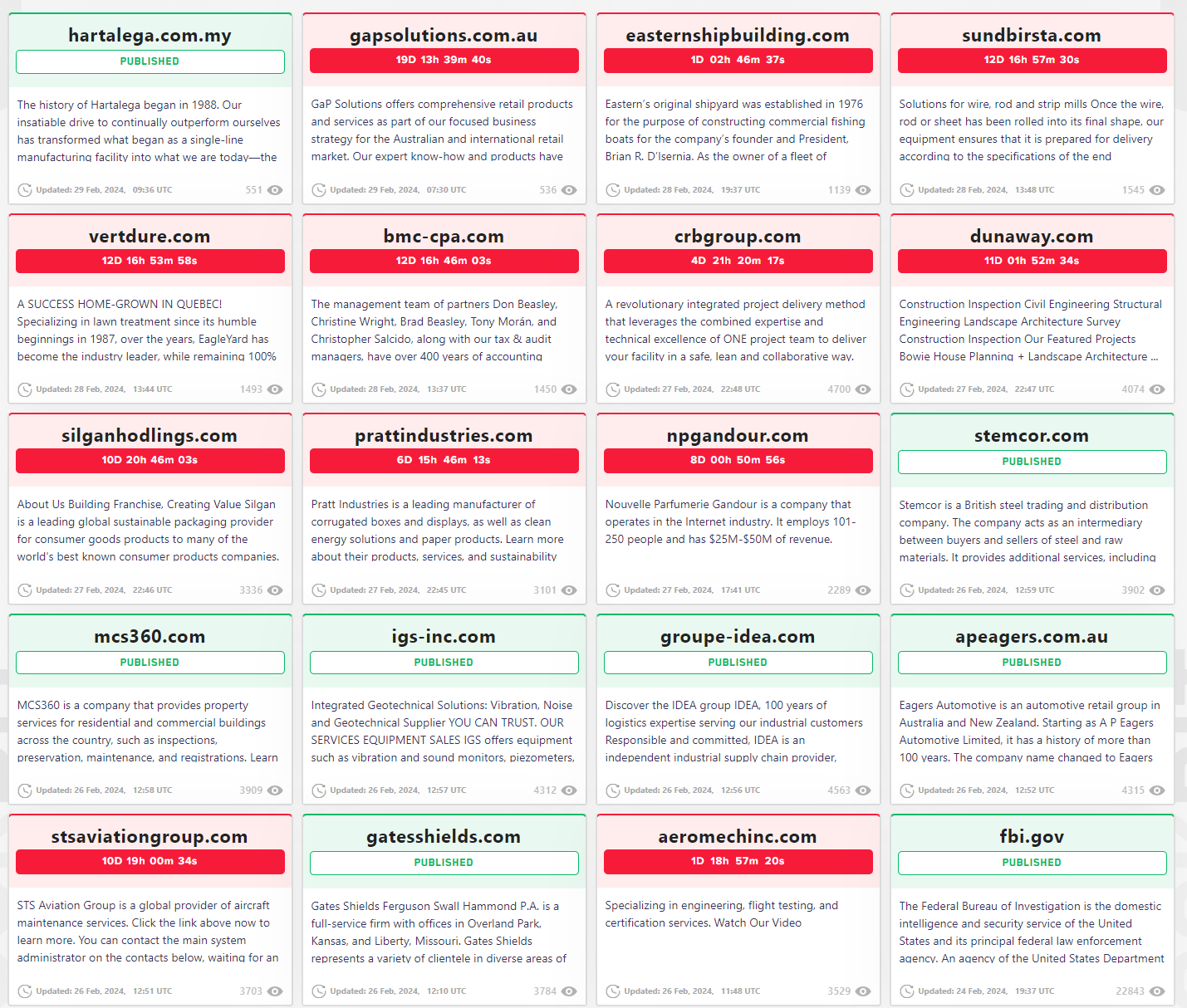
Dubbed "Operation Cronos," the law enforcement action against LockBit involved seizing servers, arresting members, seizing cryptocurrency accounts, and releasing decryption tools for victims. This operation, while significant, has not marked the end of LockBit's activities as many had presumed. The group's leader, LockBitSupp, has declared the resumption of their operations on the dark web, demonstrating the group's ability to bounce back and continue its criminal endeavors. They already have a new leak site out.
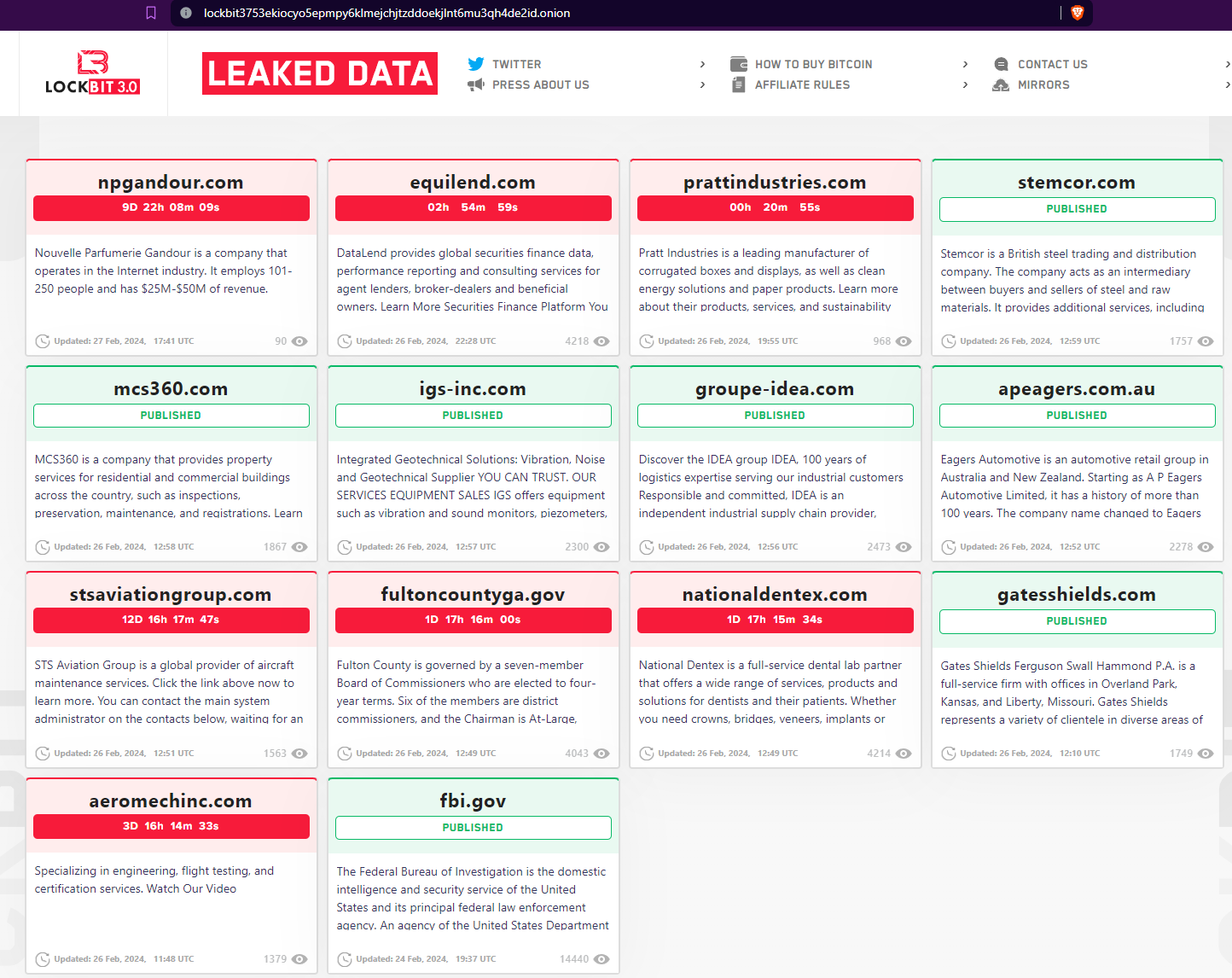
LockBit's quick recovery and the launch of a new data leak site underscore the group's adaptability and deals a blow to the “success” of law enforcement efforts to shut down their operations. This is all too common in the cybersecurity arena and half expected by many in the industry. By relocating its operations and listing new victims, LockBit has signaled its defiance and intention to persist as a top player in the ransomware cartel. This resilience points to the broader challenge of permanently dismantling sophisticated cybercriminal networks, which often possess the resources and technical acumen to rebuild and adapt following law enforcement interventions.
The FBI.gov article contains a lengthy text file with LockBit’s version of the story - Here is is summarized
On February 19, 2024, LockBit experienced a security breach on two servers due to an outdated PHP version (8.1.2), potentially exploited via CVE-2023-3824. Initial signs of the breach were detected when site errors occurred, leading to an eventual realization that server information had been erased. The breach was attributed to negligence in updating PHP, amidst a lifestyle described as complacent due to financial success. The breach prompted an upgrade to PHP 8.3.3 on new servers and a realization of the widespread risk posed by the vulnerability, suggesting that others, including competitors and forums, might have been similarly compromised. LockBit suspects the FBI orchestrated the attack to prevent the leak of sensitive documents from Fulton County's government systems, which could impact upcoming U.S. elections.
The incident led to a reassessment of cybersecurity practices, emphasizing the need for comprehensive security updates, password changes, and server audits. They also state that in order not to get caught “all you need to do is quality cryptocurrency laundering.” They also claim that the FBI inaccurately stated they possessed source material and all decryption keys, when in fact only 2.5% of the decryptors are usable, as the remainder are protected.
LockBit plans to decentralize and enhance the security of their infrastructure to prevent future breaches. LockBit criticizes the FBI's motives and methods, viewing the attack as politically motivated and aimed at protecting sensitive information. They express skepticism about the arrests made in connection with the breach, suggesting that those apprehended were not core members of their operation. Despite the setback, LockBit vows to continue their activities, motivated by competition and the challenge of evading law enforcement.
The saga of LockBit's takedown and subsequent resurgence raises critical questions about the efficacy of current law enforcement strategies to combat ransomware and the need for a multifaceted approach that includes stronger cybersecurity defenses, international cooperation, and innovative solutions to disrupt cybercriminal supply chains. The group's new found commitment to decentralize its operations further complicates efforts to neutralize such threats. This cat and mouse game between cybercriminals and law enforcement is a story as old as time and we expect it to continue.
Stay tuned for more updates as there will be further developments in this unfolding drama; the story is far from over.