I have answers to some of these :)
1. Not sure, will have to get someone more technical to jump in.
2. On the endpoint, if you click on the gear next to PC Security, then go to Block/Allow tab, anything in the Monitor column is being watched and journalled. If it is determined to be malicious then that will trigger the rollback. In the console you can look at a report on Undetermined Software and that will show you what is unknown and being monitored.
3. Unknown processes will be monitored until a determination is made, either by our threat team or by a manual override.
4. Our firewall uses the Windows Firewall and makes changes to it's settings. You can disable that if you want to use other Firewall software
5. We have a separate more complete web filtering solution. WSA should block malicious websites, but if you want to control where people go from a policy standpoint (like no gambling sites) then check out
WSS
6. Check with support on that one - my understanding is it should show in the console. They'll also be able to let you know what that log file entry means from #1
7. Our philosophy is to catch malware at the time of execution, rather than in transit. If you need a solution to filter your email or media then you'll want to look at adding other software to do that
General questions:
1. There is some good documentation here:
http://live.webrootanywhere.com/content/750/Webroot-SecureAnywhere-Endpoint-Protection that you can get to from the console, by clicking on Help. We also have some KB articles here on our community:
https://community.webroot.com/t5/Webroot-Education/tkb-p/ent5%40tkb and you can always ask here if there's something specific that you can't find documentation on and we can point you in the right direction.
2. We have articles here on the community and on our blog about some threats, and we also generally refer people here if you want to look up a specific threat:
https://www.virustotal.com/en/
Got some more info from the folks here:
1. For some of the log entries we don't provide documentation, partly because it is proprietary and partly because we don't want to clue in malware writers. If you do need help with anything in the logs due to an issue best bet is to contact support.
4. If you are using a proxy then you'll want to install Webroot with the proper proxy info using a command line switch
6. EICAR isn't a good test to run on our software as it is tuned to signature based detection. We suggest using our Mock virus for testing purposes if you must test (we don't recommend virus testing for consumers, but this is for the business product so this is only for you IT folks that know what you are doing) . This can be downloaded from:
<url removed>
Another update on #2 - to see the monitored processes on an endpoint you can also look at the wrlog.log file, which will give you a more complete view than the console report. Best bet when there are unknowns being monitored is to contact support to get a quick determination that will update our database and then move it into the correct category for you (and everyone else using Webroot).
Hi Nic,
- I do understand that. I just went through the logfile, noticed those numbers and got curious 🙂
- I'll look closer at that; I noticed something odd but will do some further testing.
- Ok.
- So with Windows Firewall disabled also the WSA firewall doesn't work? If so WSA should show an alert or at least mark the firewall disabled.
- Is there a way to test the web filtering of WSA? I didn't notice that web filtering is enabled and also there's no browser extension installed.
- I did a manual scan of the EICAR file without executing it and it was detected; but the web console didn't show anything. I'll try it again and if report it to support if neccessary. I do understand your concerns regarding testing WSA with malware; on the other hand one should now how WSA behaves before it detects real threats. I've downloaded your "virus", you can remove the link if you want.
- We'll look for a solution for our mail server; currently it's included it our Sophos subscription. I wonder how other customers think about this topic.
Thanks for the link to your documentation; I havn't found it on your website.
4. WSA makes use of the Windows inbound firewall and augments it with its own outbound firewall. The installation should turn on the Windows Firewll if it is off, and adjust the settings to WSA's liking - let me know if you're having any issues with it.
5. For the web filtering, look in the console to see if the policy has it turned on. It should augment search results with checkmarks indicating the reliability of sites, and prevent you from visiting bad ones.
6. For a real threat it should show in the console. I think we've added "detection" for the EICAR file, but I'm not sure if that extends to the console reporting. If you really want to test with something live you could download and install something from CNET and see if it catches the PUA/PUPs that try to get installed - that should be minimal risk since it isn't like you are testing with cryptolocker.
7. Is your mail in-house or outsourced? If the latter they usually do their own scanning. If the former then there are lots of standalone services that you can use to filter your mail for both spam and viruses.
The documentation link is from the console, so just click on the drop-down in the upper right and click help anytime you need to get to it.
4. I just noticed that on my test-PC the Windows firewall was enabled; after disabling it I received the following warning:
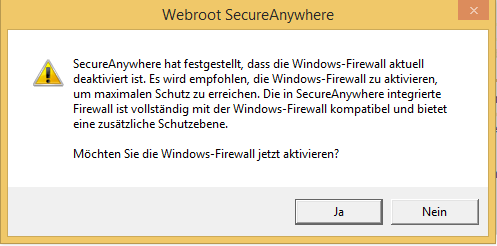
(in English: SecuryAnywhere noticed that Windows-Firewall is disabled. [...] Would you like to activate Windows-Firewall now?)
Probably it didn't do the same on our domain clients because we've deactivated WF via GPO.
5. I don't have those checkmarks although it's enabled in the policy. Also Shawn wrote here that WSA for business doesn't have web filtering or at least the extension: https:///t5/Webroot-SecureAnywhere-Antivirus/Web-Shield-and-its-function-with-Browser-Extension/m-p/118102#M7039
I also noticed that there are some settings missing in the firewall configuration:
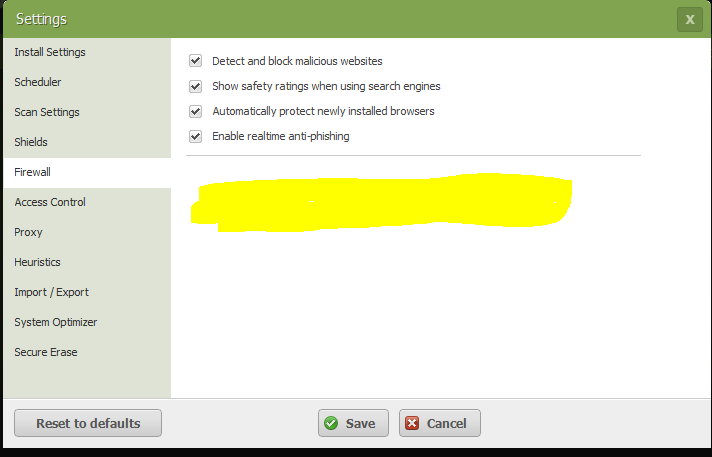
So WSA business isn't the same as WSA for consumers?
6. I would do(or I'm doing) those tests on a non productive client outside of the live network. I'll report back if it's working or not.
7. We've got our mail in-house and had Sophos Puremessage handling Spam/AV. I have already looked at other solutions but they're very pricey. Most solutions cost the same per mailbox as we're paying for the clients, which is like doubling the costs; and we do have more mailboxes than clients.
Yep, I was mistaken on #5, sorry about that! Yeah there are some differences between consumer & business, in terms of the feature set, although the base AV is the same engine. On the flip side the business console has more features than the consumer one. Please let me know if you have any other questions!
Ok that's it for the moment; thanks again for your help.
I'll try to look at everything and get some deeper knowledge till our trial expires. Personally I think I have already made the decision to go with Webroot :)
EDIT: Would love to see other opionios on #7; also if someone has a recommandation for a good Anti-Spam/AV solution...
Sure thing, happy to help, and glad you are liking it so far. I'm not up to speed on the latest around email filtering solutions unfortunately. I've been out of the sysadmin game too long 🙂
Let's see what the Spiceheads do recommend ;)
Just did some tests with the "Application Protection" and also added custom apps to be protected, but I didn't find a setting for that in the Webconsole. There's only the option to define either "good" or "bad".
Regnor,
To protect those custom applications, I found, I think, a way to do so on a per machine or multiple machine basis.
Try this:
Log into the Console
Click Endpoint Protection
Click Group Management
On the left pane, click the Group that the machine(s) is located in
On the right upper pane, check the machine(s) you need to send the Protect an Application command to.
Click the Agent Commands button
On the drop down, select Identity Shield
Select Protect an Application
Enter the MD5 of the application file to be protected.
You're right; I looked everywhere but not under agent commands...perhaps it was to late yesterday 😉


