Welcome to Data Privacy Week! This is an annual campaign with the purpose of spreading awareness about online privacy and educating citizens on how to manage their personal information and keep it secure. Today we will discuss the importance of using cold storage password managers as well as the impact of the General Data Protection Regulation (GDPR) on data privacy. Get ready to learn about personal data security, creating and storing strong passwords as well as the negative side-effects of rising GDPR fines.
Password Manager Data Breaches
At the end of 2022, Norton LifeLock suffered a data breach. Symantec reports that their systems were not directly compromised - it seems as though the attackers used a technique called credential stuffing to try out user credentials for the service in bulk. It is likely that the attacker bought a large amount of stolen user credentials on the Dark Web. By attempting logins with that massive list of credentials, the attacker was successful in compromising accounts that had reused usernames and passwords on other platforms which were previously breached.
In the year 2023, news stories concerning data breaches have seemingly become a weekly event. The big difference with this breach is that it concerns a password management service. For the past few years, cybersecurity experts (including us) have been suggesting the usage of cloud-based password managers. But now that big players in the password management services experienced a high-impact data breach, there is a crisis of faith that needs to be addressed. Are password managers still a secure method of maintaining digital security? The answer to that question is still yes...but with footnotes.
Cloud-based password managers hold the keys to all of your passwords on a server that is connected to the internet. This is an inherent security risk because threat actors will always look for new ways to infiltrate servers and steal data. If stolen data is encrypted, they can still attempt to brute master passwords - the difficulty of which depends on the length and randomization of the password. If the master password of a stolen password manager vault is 10 characters and uses common dictionary words, it could plausibly be cracked within a day or two. If the master password is 24 characters and highly randomized, it is unlikely to ever be brute forced.
So are cloud-based password managers still a highly effective tool? Yes, but their resilience against data breaches sharply decreases when users create lazy master passwords. So, we still recommend them but as per usual, it is important that users employ strong security practices such as the creation of long pass phrases. There are also two strong alternatives to cloud-based solutions that deserve an honorable mention: cold-storage password managers and hardware security keys. Both of these security tools utilize offline methods of verification or storage. The lack of an internet connection makes them immune to data breaches or a personal computer being hacked.
I have personally been using an offline password manager for years and it has worked very well for my purposes. I use a password management database called KeePassXc. I keep copies of the database file on multiple flash drives in multiple locations. The database is protected by a complex 24+ character master pass phrase to protect myself from a theft scenario. It’s a bit of an old-school method of password management but at least I know that it’s immune to data breaches.
GDPR - is it helping data privacy?
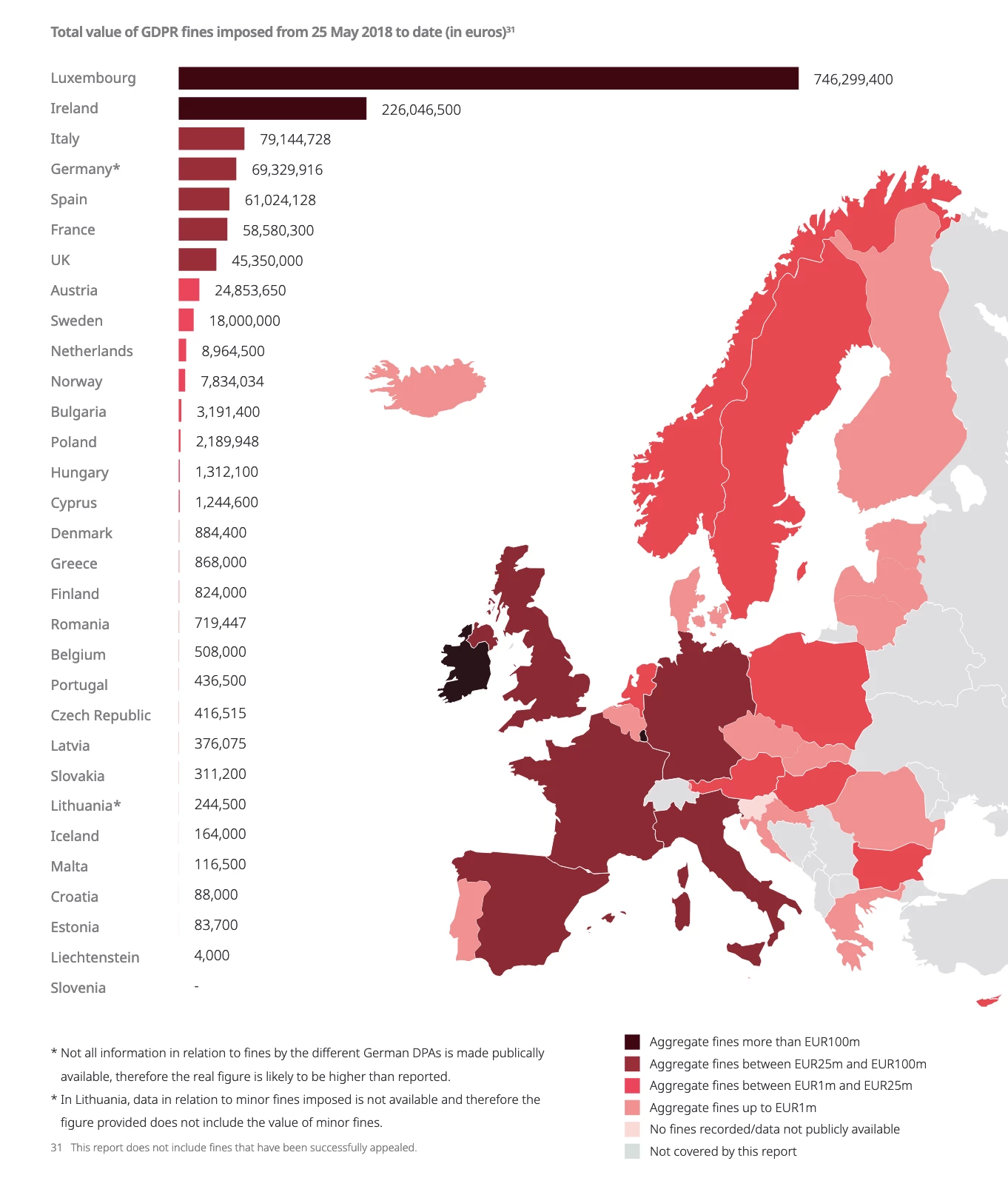
The General Data Protection Regulation (GDPR) is a regulation in EU law on data protection and privacy for all individuals within the European Union (EU) and the European Economic Area (EEA). The regulation imposes significant fines on organizations that fail to protect personal data, and this can be a significant financial burden for businesses. To date GDPR has fined almost $3 Billion and has 7x the amount of fines just last year.
https://digitalguardian.com/blog/number-gdpr-fines-rose-7x-2021
The largest fines incurred to date are to no ones surprise Amazon, Facebook and Google

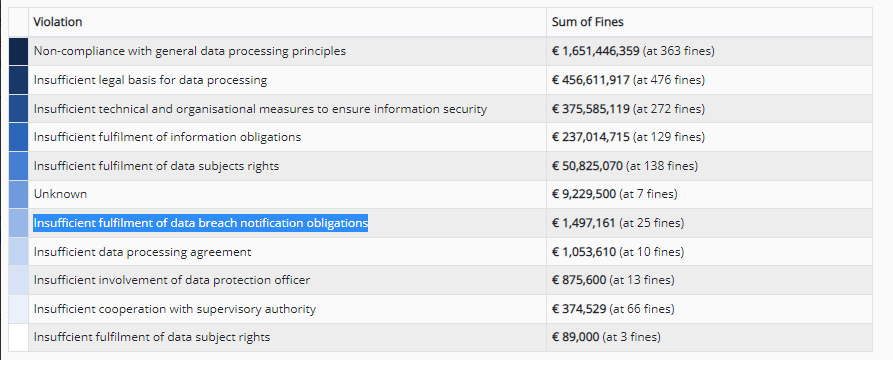
Drilling down on the type of violation and the amounts paid for each we’ll find that overwhelming majority of the fines are for data storage/processing principles and insufficient legal basis for that storage/processing. The bulk of these fines are similar and looking at some of the infraction specifics - “making it difficult for internet users to refuse online trackers” and “penalty for failing to get consent from users before storing advertising cookies.” While these fines seem astronomical, they are just a drop in the bucket for the big powerhouse tech brands and they will continue to violate these laws as long as it results in value that exceeds the possible fines that would be incurred when caught.
In the case of ransomware attacks, victims may choose to pay the ransom demanded by the attackers rather than risk incurring the potentially larger fines imposed by GDPR for failing to protect personal data. This is because paying the ransom can be seen as a faster and less costly solution, especially if the organization does not have an effective incident response plan in place - which is so common. So it’s very clear that the overwhelming majority of the fines imposed by GDPR are NOT from ransomware or breach incidents and those are less than 0.0006% of the total. The damage to brand, reputation, stock price, crisis communication to customers and partners, all take a heavy toll on the decision to pay a ransom. It has become more attractive to pay the ransom and sweep the entire incident under the rug in order to avoid GDPR fines. GDPR seems to have no real impact on the cyber resiliency of an organization (as intended) and pushes them towards taking the easy way out.
However, it is important to note that paying the ransom only perpetuates the problem of ransomware and may encourage attackers to continue these types of attacks. It is important for organizations to have robust data protection measures in place to prevent and respond to ransomware attacks. Additionally, it is vital for businesses to create an effective incident response plan to minimize the potential impact of such an attack.
In Summary
Data Privacy Week is a useful time for all of us to reflect on our digital security hygiene. As data breaches continue to plague users worldwide, it is important to evaluate your cyber security practices. The uncomfortable truth of the past decade is that digital data is highly valuable and very difficult to secure. Threat actors will continue to steal massive amounts of data and businesses/individuals will continue to suffer the consequences.
Furthermore, GDPR has largely failed in its stated mission of strengthening the digital privacy rights of European citizens. The increasing fines that punish businesses for being a victim of ransomeware and incentivizes them to pay ransoms rather than make their data breach public - this is the counterintuitive result of a policy that was supposedly aimed at protecting personal data privacy.
Data privacy worldwide is unfortunately not in a healthy state. The upside is that you as an individual have the ability to strengthen your security practices in order to mitigate any damage that results from something like a data breach. Creating strong and unique pass phrases and utilizing cold-storage password managers are an efficient way to minimize the fallout of a data breach.
Are you planning any upgrades to your digital security?
Was anything in this article surprising?
Let us know your thoughts in the comments below!