In the latest chapter of the ongoing LockBit saga, international law enforcement agencies have struck back once again, seizing the group's infrastructure and identifying the key figure behind the infamous ransomware operation. This second takedown, building on previous efforts, further demonstrates the determination of global partners to disrupt the cybercriminal network's activities.
See the previous events on this epic feud between LockBit and Law Enfocement
The New Takedown: Exposing the Leader

- Identity Revealed: Dmitry Yuryevich Khoroshev Unmasked
- Following a thorough investigation, authorities have unsealed an indictment revealing the mastermind behind LockBit: Dmitry Yuryevich Khoroshev, known by aliases like "LockBitSupp" and "putinkrab." This Russian national has been charged with multiple counts of fraud, extortion, and intentional damage to protected computers.
- Renewed Sanctions and Rewards
- The U.S. Department of the Treasury has imposed sanctions on Khoroshev, freezing all U.S.-controlled assets and prohibiting U.S. persons from conducting any transactions with him. A reward of up to $10 million has been offered for information leading to his capture. The U.K. and Australia have also announced coordinated sanctions to cut off Khoroshev's access to international financial systems.
- LockBit's Reach:
- Under Khoroshev's leadership, LockBit carried out over 2,500 attacks across 120 countries, causing billions of dollars in damages and extorting at least $100 million in ransom payments.
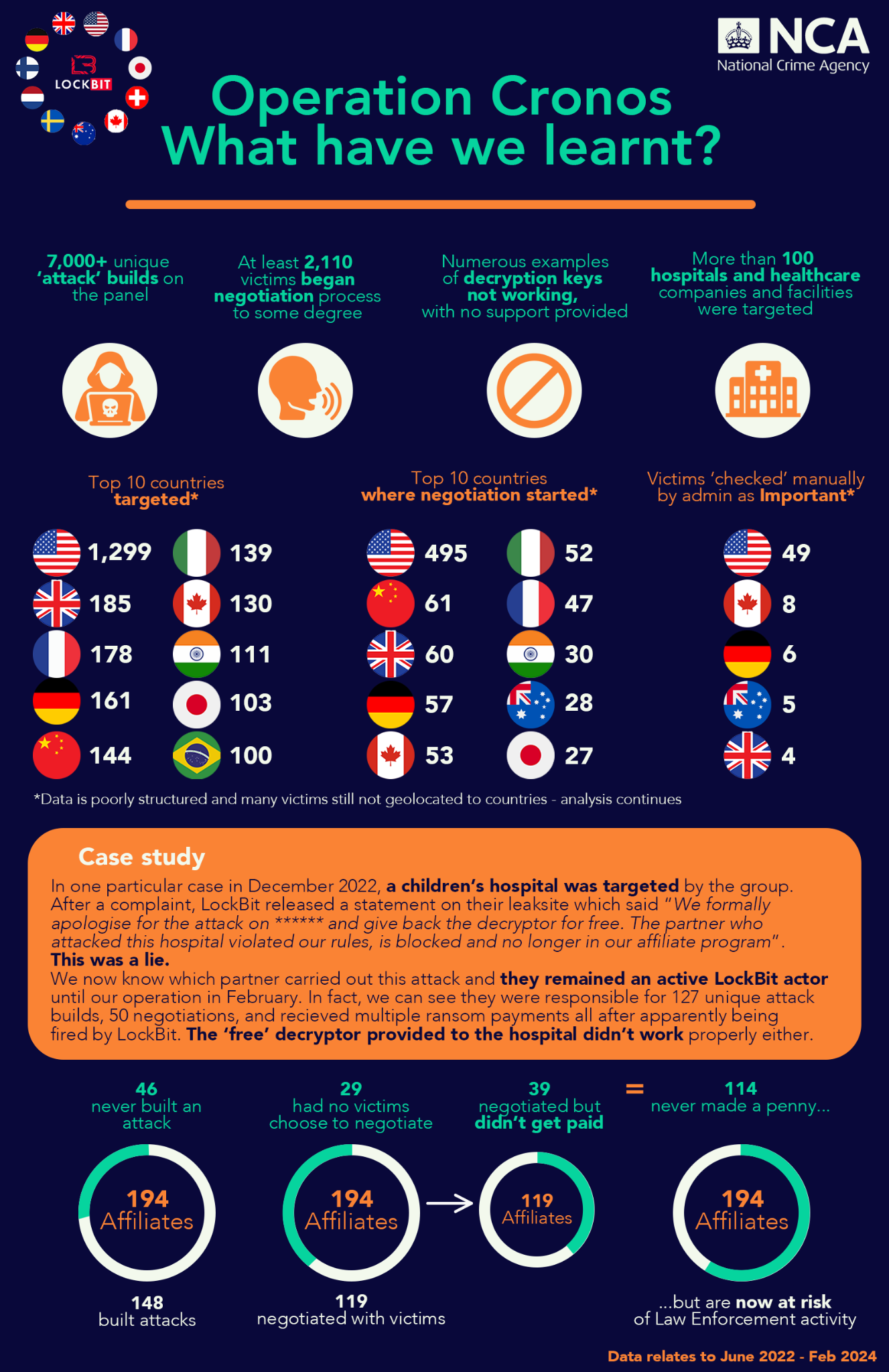
Key Learnings from Operation Cronos:
-
Attack Volume:
- Over 7,000 unique "attack" builds were found on the panel, showcasing the extensive infrastructure and resources used by LockBit.
- More than 2,110 victims initiated some form of negotiation with the group.
-
Targets and Geography:
- The U.S. led the list of top 10 targeted countries, followed by Italy, France, Germany, and India.
- Healthcare organizations, including over 100 hospitals, were heavily targeted.
-
Affiliate Network:
- 194 affiliates were identified, with 148 responsible for building attack plans.
- While 119 negotiated with victims, only 39 affiliates received ransom payments.
- Some affiliates were marked as important by LockBit administrators, often leading to manual reviews.
-
Case Study:
- In December 2022, a children's hospital was attacked, but LockBit's decryption key didn't function properly despite promises.
- The affiliate responsible remained active despite being publicly removed from the program.
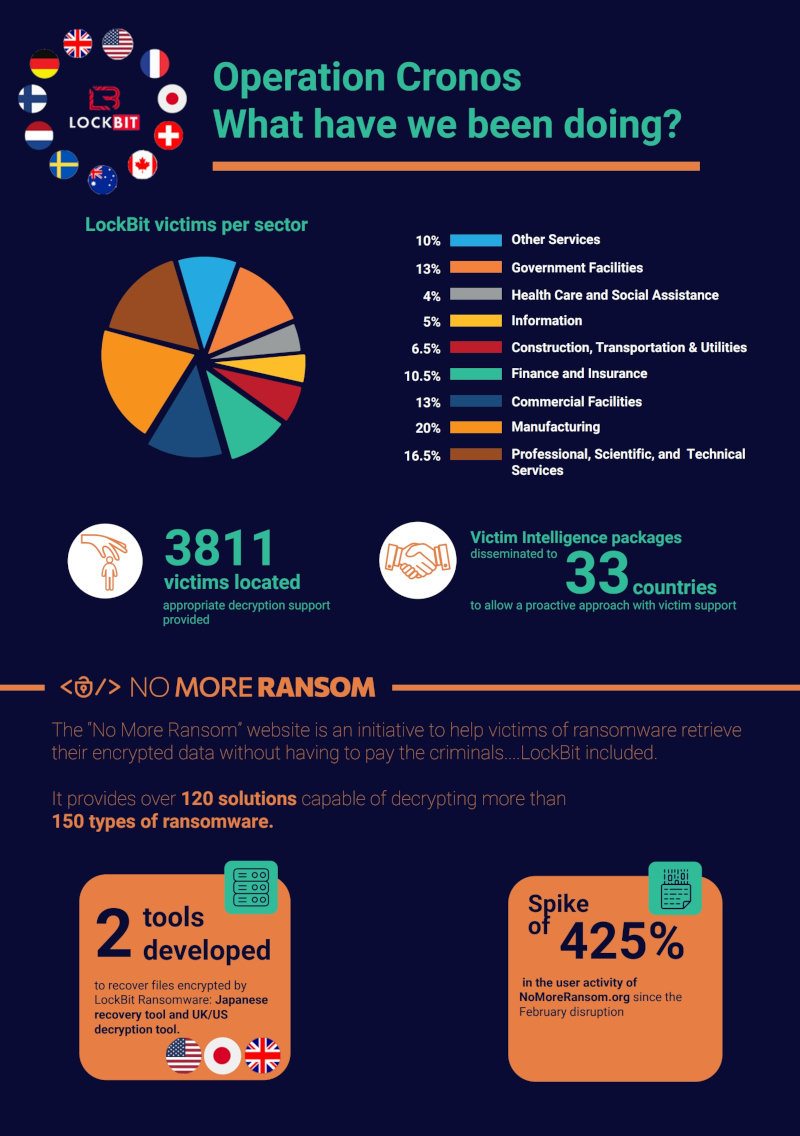
Operation Cronos: What have we been doing?
-
Affiliate Exposure:
Law enforcement is identifying and dealing with LockBit affiliates. By fully compromising LockBit's platform, they have extracted large amounts of data that will support coordinated actions against these affiliates.
-
Victim Data:
Over 3,800 victims have been located and provided with decryption support, helping organizations recover from LockBit attacks.
-
Affected Sectors:
The victims spanned various sectors, including:
- Manufacturing (20%)
- Professional, Scientific, and Technical Services (16.5%)
- Commercial Facilities (13%)
- Health Care and Social Assistance (13%)
- Other sectors like Government, Finance, Information, and Construction.
-
No More Ransom Initiative:
- This initiative offers over 120 solutions capable of decrypting 150+ types of ransomware.
- Tools developed in Japan, the UK, and the U.S. help recover files encrypted by LockBit.
- A significant increase (425%) in user activity at NoMoreRansom.org was noted after the February disruption.
-
Global Intelligence Collaboration:
- Victim intelligence packages were shared across 33 countries, enabling a proactive approach to support victims and enhance resilience.
Operation Cronos: Further Successes
-
Infrastructure Seized
Building on the previous operation, law enforcement seized additional LockBit servers and the group's leak site. They also exposed a comprehensive list of affiliate IDs and usernames, potentially leading to further arrests and disruptions.
-
Victim Support
Victim intelligence packages have been shared with 33 countries to proactively assist in recovery efforts. The "No More Ransom" initiative has seen a 425% spike in activity since the disruption, helping victims avoid ransom payments and recover their data.
-
International Collaboration
The collaboration between the FBI, NCA, Europol, and other agencies has proven instrumental in identifying Khoroshev and disrupting the network. This level of global teamwork shows the power of unified efforts in safeguarding the digital world.
Remaining Resilient
While this takedown marks a significant victory, the LockBit group has proven its adaptability before. The ransomware ecosystem is evolving, with LockBit already planning a more decentralized infrastructure to circumvent future disruptions. Nevertheless, these recent successes reinforce the importance of rapid reporting, international collaboration, and a proactive cybersecurity strategy.
We fully expect a comeback, statement, and new measures to be incorporated from Dmitry Yuryevich Khoroshev (LockBit Support). There are still new victims being hit even now with this strain of ransomware so there has not been a definitive shutdown of the LockBit affiliate program. We are all eager to see if this unmasking will lead to capture, but we are not holding our breath.
Stay tuned for more updates as this story unfolds. The fight against LockBit and other ransomware groups is far from over, but law enforcement's relentless pursuit shows that no cybercriminal network can evade justice forever.







