One of the more worrying findings of the 2020 Webroot Threat Report was a 640% year-over-year rise in the number of active phishing sites on the web. While these still make up a minor portion of all malicious sites, cybercriminals are clearly finding them profitable enough to be worth investing time and labor on.
Phishing attacks are also diversifying considerably from what people often think of as the typical, email-based attack. To help our Community to be better identify the growing number of forms these attacks take, we’re beginning a series of posts describing them. We’ll begin with a typical phishing attack before elaborating on ten more subtypes including spear phishing, search engine phishing, business email compromise and more.
But first, the good ol’ phishing we’ve come to know and loathe.
Download the 11 Types of Phishing eBook
Standard Phishing: Casting a Wide Net
At its most basic, standard phishing is the attempt to steal confidential information by pretending to be an authorized person or organization.
FYI: Most sources credit the first description of a phishing attack to a paper by the International HP Users Group, Interex in 1987.
An Example of Standard Phishing
This tactic has, in the past, been more about quantity versus quality. The audience was broad and emails were riddled with noticeable errors.
As phishing has developed, it’s become more sophisticated and harder to spot.
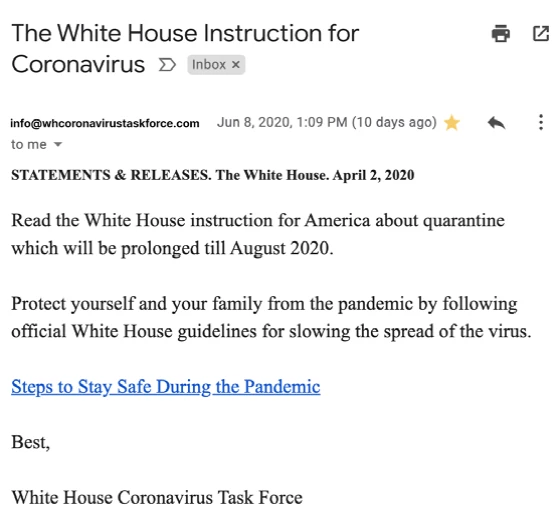
Tip: Do you know how to tell if an email’s legit? Here are five ways to spot a phishing email
