Imagine a thief walks into your home and rummages through your personal belongings. But instead of stealing them, he locks all your valuables into a safe and forces you to pay a ransom for the key to unlock the safe. What choice do you have?
Substitute your digital space for your home and encryption for the safe and you have what’s known as ransomware. Ransomware is a type of malware. After the initial infection, a note appears demanding payment, which is usually in the form of untraceable currency such as Bitcoin.
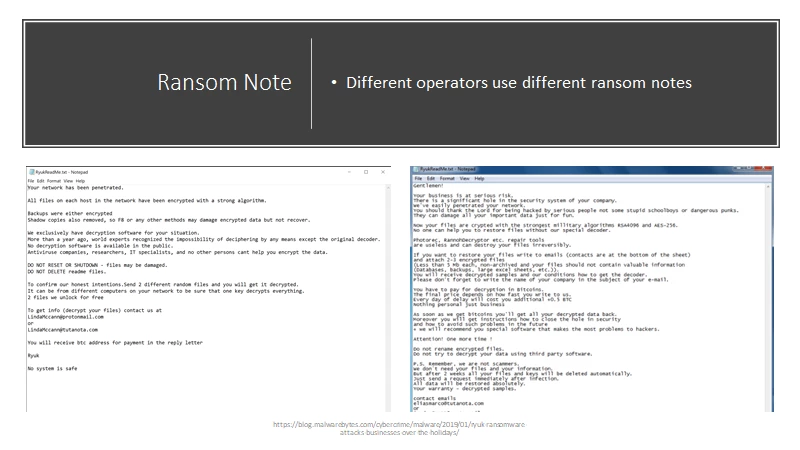
Once your files are encrypted, you can’t access them until you pay the ransom. There have already been hundreds of millions of victims of ransomware, and the number keeps growing.
The roots of Ransomware can be traced back to 1989. The trojan, known as PS Cyborg, was spread through diskettes given to attendees of a World Health Organization International AIDS conference. Victims of PS Cyborg were to mail $189 to a PO Box in Panama to restore access to their data.
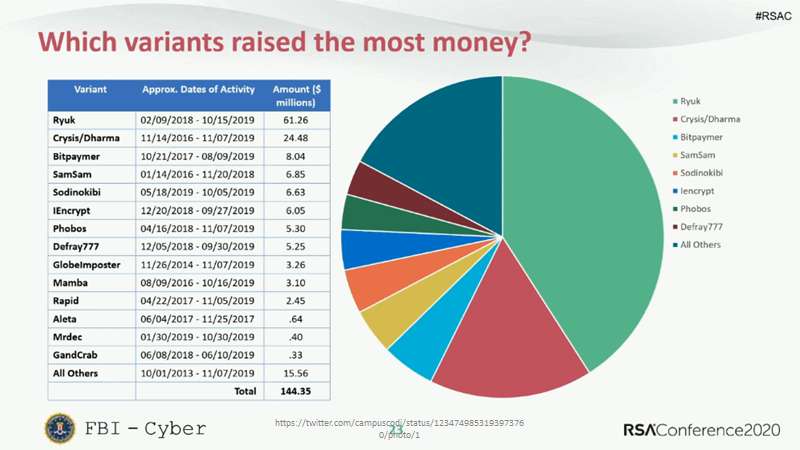
Historically, ransomware targeted individual personal computer users. Today, the big money is in attacking businesses. Most of these infections go unreported because companies don’t want to expose themselves to further attacks or reputational damage.
Criminals know the value of business data and the cost of downtime. Because they service multiple SMB customers simultaneously, Managed Services Providers (MSPs) are now an especially attractive target. A successful attack on an MSP magnifies the impact of attacks and the value of the ransom.
The New Squeeze
Now that you have an understanding of the inner-workings of ransomware and how they convince companies to pay up, it’s time to discuss a recent change in the tactics of ransomware developers.
The traditional method of extracting cash from businesses is as follows:
- Drop malware payload on a collection of machines or servers
- Identify and encrypt all/the most important files
- Demand a ransom in Bitcoin and expect them to pay in order to avoid bad press and lost data
The NEW method that ransomware developers have begun to use adds an additional step at the end:
- Threaten to auction off the data if the ransom is not paid
This incorporates a secondary reason for ransomware victims to pay the proposed ransom: If they do not pay, it will become publicly known that they have breached data privacy policies such as GDPR. There are very large fines associated with a breach in GDPR, not to mention a huge amount of damage to their brand/reputation.
Think about it: this new tactic is utilizing some very subtle psychological principles to make sure that they get their money no matter what.
“Pay us or pay GDPR fines while we still get to auction off your data for payment. “
Who is orchestrating large-scale ransomware attacks?
To understand the main players in this game, we need to understand the two main “tasks” that exist within the world of ransomware:
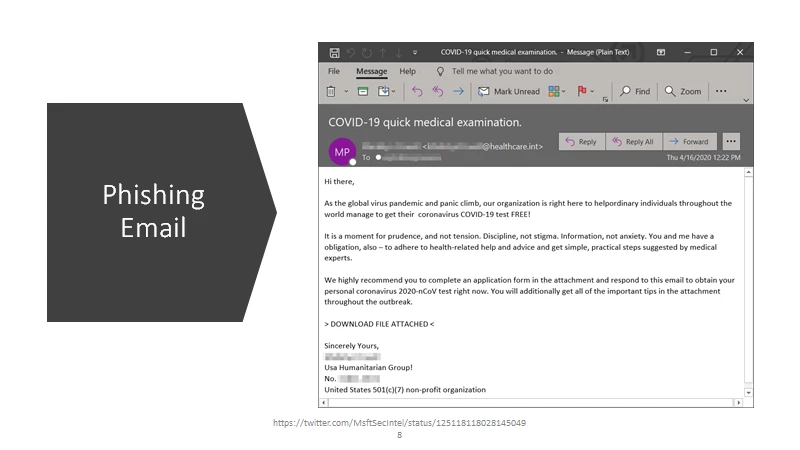
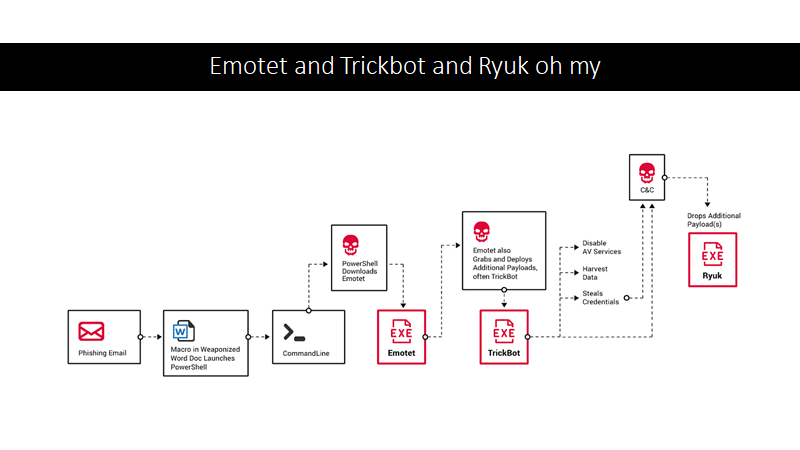
- First stage of infection: how the operator gets initial access to a system.
- This stage is generally carried out through phishing campaigns such as Emotet
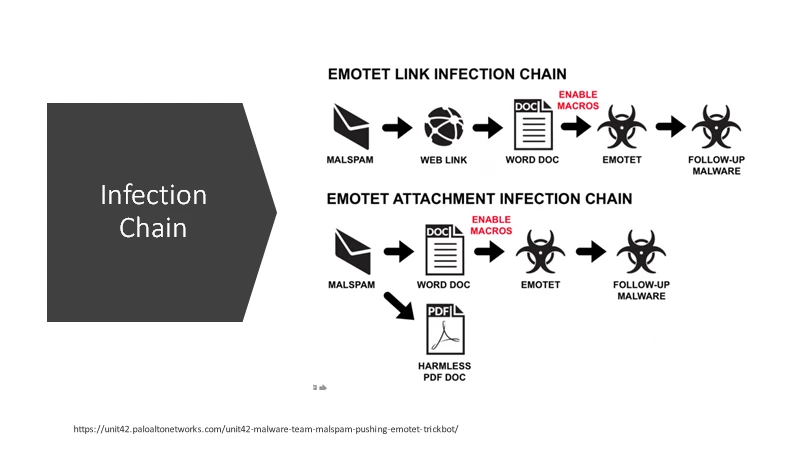
- Second Stage of infection: Dropping a malware payload
- This is the malware used to scan and encrypt the servers that it has infected
These two tasks are often carried out by two different teams that work together. Here are a few examples of those teams:
- Ryuk/TrickBot
- Bitpaymer/Drydex
- Sodinokibi/GranCrab/rEvil (singular team, Ransomware-as-a-service)
- Doppelpaymer
- Emotet (Often used by most malware operators to spread infections)
It is difficult to track the geographical origins of these teams, but it is fairly well known that the Sodinokibi/GranCrab/rEvil team is based out of Russia.
How do they auction off stolen data?
Generally this is done via forums or standalone websites using an “Onion” link on the TOR network. Sometimes they release data for free if it isn’t worth much or if it’s a small company.
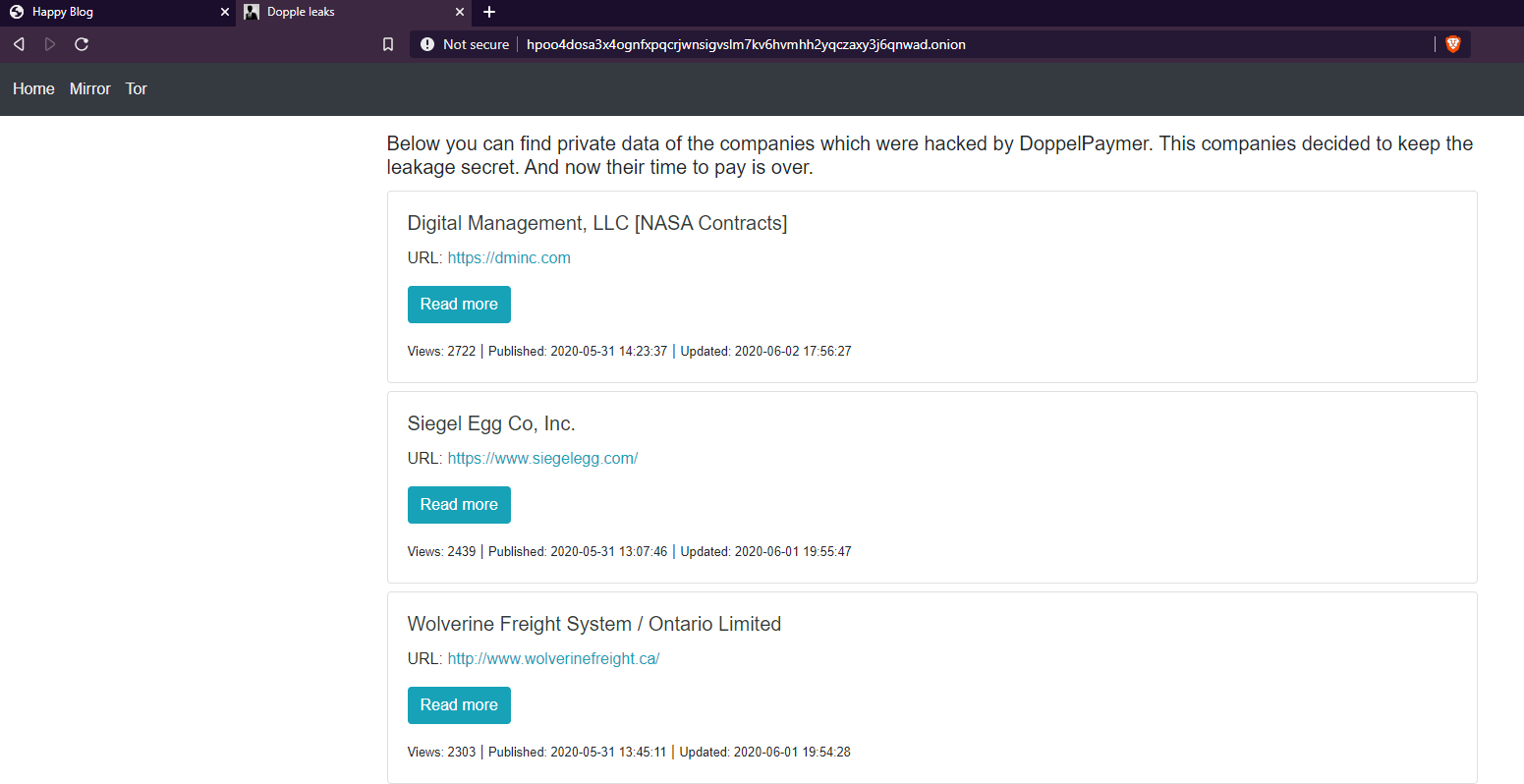
sample of data given for free
When they get access to high-profile data, they set a starting bid with a minimum bid increment. These auctions function similar to an eBay bid, with one major difference: you have to send a minimum deposit to begin bidding. This is to prevent law enforcement or tire-kickers from bidding high and then not paying.
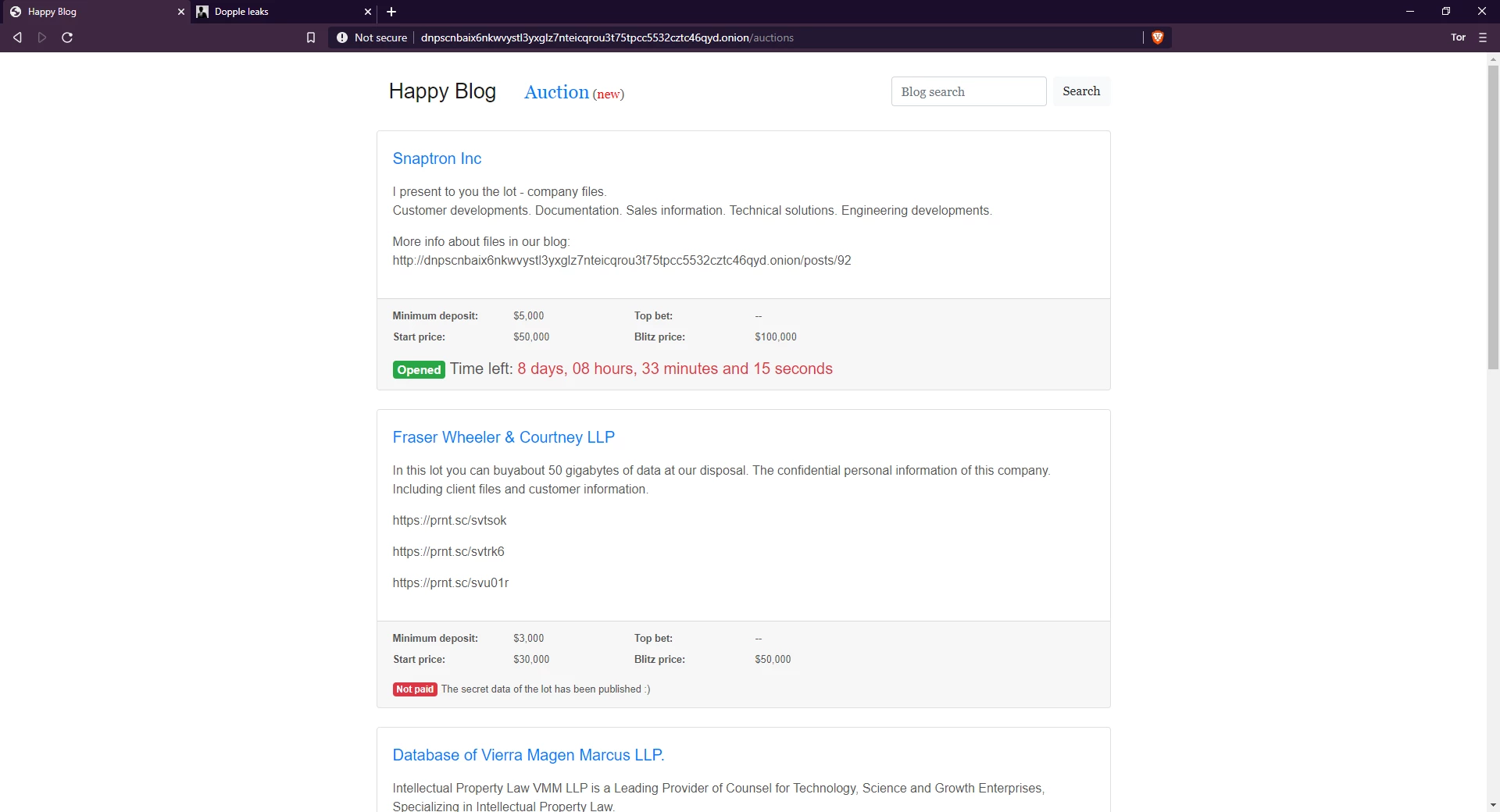
bid examples
These auctions could be a very valuable purchase for many different parties - primarily competitors and identity thieves. The addition of data-auctions is a genius method of inducing more psychological stress on their victims, thereby increasing the likelihood of receiving payment. Whether we like it or not, Malware operators continue to stay one step ahead of companies that have holes in their cyber resilience plan.
What does everyone think about this change in tactics within the world of malware? Do you believe that companies have any way out of paying the ransom? Let me know in the comments below!
