Social Engineering is the art of manipulating people into giving up their confidential information. This information could include passwords, bank info, birthdate, or anything else that could be used for identity theft.
Cybercriminals use this tactic because it is generally easier to hack your trust than it is to hack your computer. Even if you believe yourself to be a skeptical, critical thinking individual, you can still fall prey to a social engineering attack.
Therein lies the real danger behind social engineering:
Most people think they are immune to becoming a victim, and most are similarly vulnerable as targets. This is because 97% of malware operators target users through Social Engineering rather than technical flaws.
It’s worth noting that social engineering is a broad term covering a range of methods and tools. All seek to achieve an end-result of acquiring valuable data and/or access to a computer system. Let’s dive into some of these methods and how you can protect against them.
Email from a friend or family member
Imagine a criminal gets access to your mother’s email password. By doing so they’re able take advantage of anyone in her contact list. Perhaps that password is used across all her social media accounts.
You can begin to see the power and influence this cybercriminal immediately gains over any unsuspecting person with a trusted relationship with the original victim. A smart criminal would begin piecing together who is related to who, who her friends are, who her manager is, etc. By reading through past messages, the perpetrator can build a cohesive map of valuable targets.
From there, they can put a malware payload behind a link or file and create convincing messages to get you or any of your mother’s contacts to click on the malicious email. If the secondary targets don’t have an adequate antivirus solution, they’re likely to become join the web of data stealing the attacker is organizing.
On and on, the story continues…
Compelling story (AKA pretexting)
Even when a family or friend is not involved, the architects of social engineering attacks excel at using human psychology to trick victims into clicking. Some examples of a compelling story used to get a potential victim’s attention include:
- Urgently asking for help - The keyword here is “urgent.” By making you think quickly they’re making you think less. They can take advantage of our inherent desire to to help others by using bait stories such as “Your friend X is in danger and they need your help immediately – please send me some money right away so they can get treatment!”
- Standard phishing tactics - Many of us are likely familiar with standard phishing techniques, the most common of which is to spoof a website or email to appear to come from an official source. This email may mock a “please reset your password” email with Facebook logo, banner, and address like facebookinfo-noreply@gmail.com. After clicking the link and entering info, the victim’s Facebook account security is compromised, unless two-factor authentication (2FA) is enabled.
- “You’re a winner” notifications - Whether a lottery prize or a free trip to Cancun, this tactic catches many off guard. It’s known as “greed phishing” and takes advantage our dispositions for gambling or weakness for the word “free.”
Maybe it’s worth clicking and finding out more? What could go wrong without entering personal information? In fact, that click could initiate a spiral of requests, eventually to a confirmation of identity. By agreeing to one thing, the likelihood of a target agreeing to following requests increases dramatically. This effective psychological strategy is known as the foot-in-the-door technique.
A fake blackmail scenario
Let’s say a shady email arrives from an unknown sender titled “Your browser history” with a Chrome screenshot listing pornographic or otherwise embarrassing browser history. If a cybercriminal gets a potential victim’s heartrate to spike, they’re likely to keep reading. They follow up with a request: “Send $500 in bitcoin to this address unless you want me to share your dirty secrets with the family”
Most recipients of this e-mail are likely to spot this as a fake and delete the email immediately. However, the email has likely been sent to a gigantic list of leaked e-mails. If only a single recipient is jumpy enough to take the bait, the effort can worth the cybercriminal’s time. With an automated script and a cheap list of leaked email addresses, they walk away with a $1k payday in cryptocurrency. Volume is a key part of phishing’s success.
Real-world examples of social engineering
By now, most Webroot Community members will have heard of the recent Twitter hack. This was a case where a group of hackers managed to gain access to internal Twitter systems through social engineering tactics. With access to back-end tools, they took advantage of 130 high-profile accounts to orchestrate a bitcoin scam. The hacked accounts tweeted similar messages:
“I am giving back to my community due to Covid-19!
All Bitcoin sent to my address will be sent back doubled. If you send $1,000, I will send back $2,000!
Only doing this for the next 30 minutes! Enjoy.”
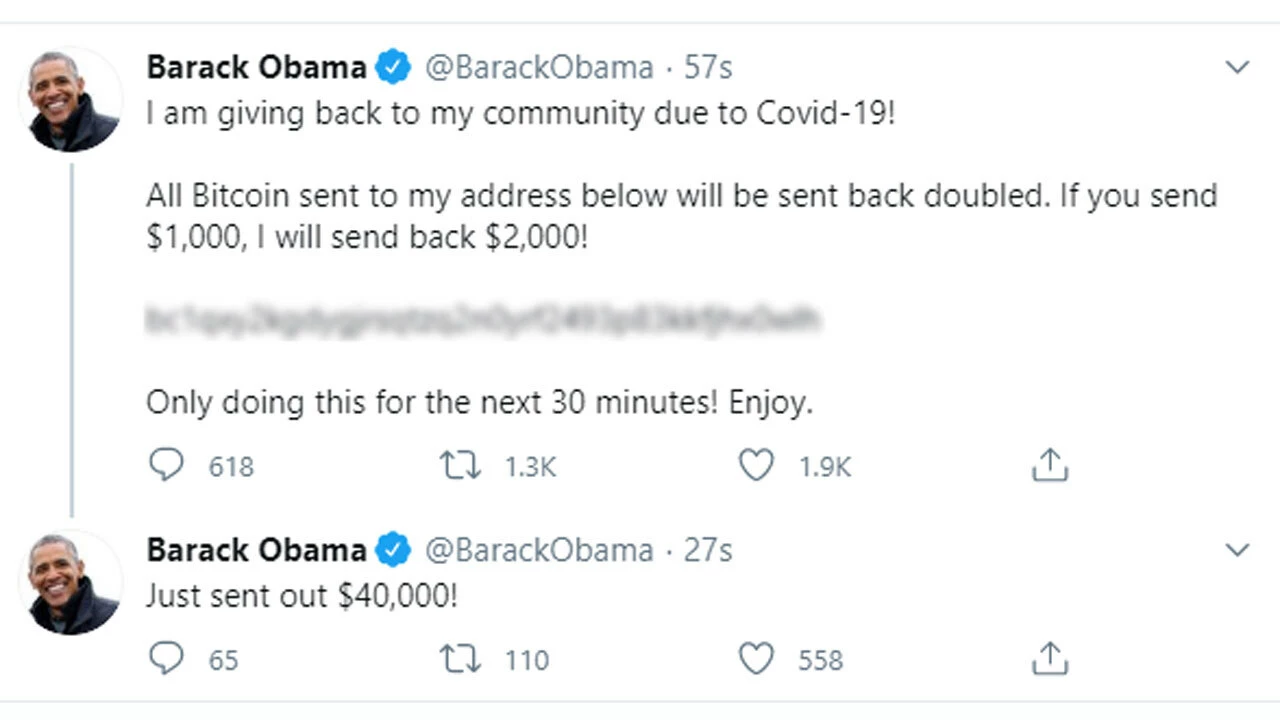
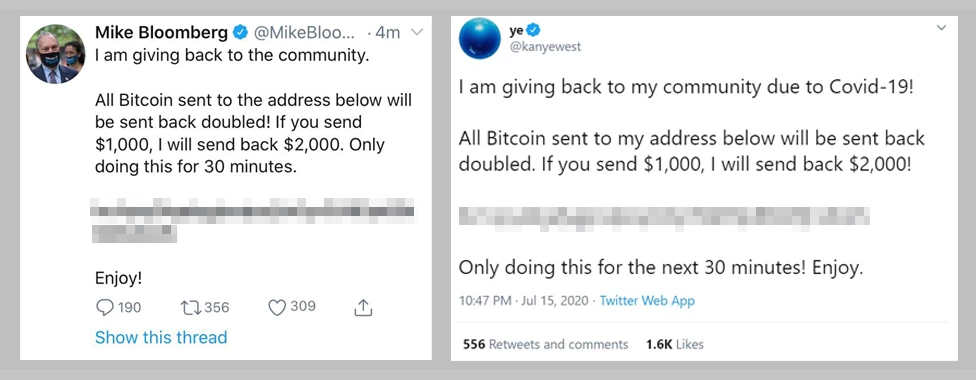
The perpetrators walked away with over $100k in bitcoin as a result of this scam. We know this because the Bitcoin blockchain uses a public ledger which allows anyone to view how much a wallet contains and all of the transactions conducted within it.
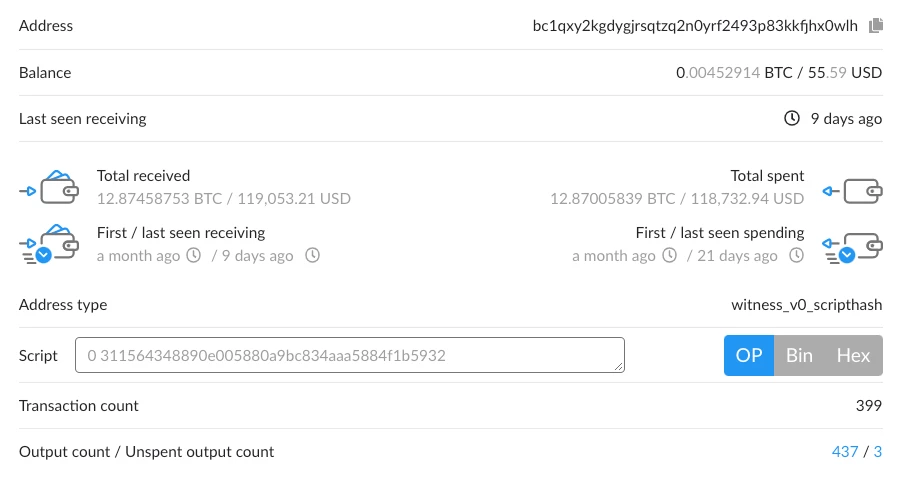
The amount of work the group conducted to identify, research and take advantage of Twitter employees with access to “god-mode” tools was significant. According to ArsTechnica, they “started by scraping LinkedIn data in search of Twitter employees who were likely to have access to the account tools.” From there they captured those employees’ phone numbers and contact info then contacting them impersonating Twitter personnel, directing them to a phishing page mimicking an internal Twitter VPN.
This gave the attackers momentary credentials for the real Twitter VPN, from which they were able to bypass the 2FA security precautions. At this point, they had gained access to the back-end tools needed to access and send messaged from any Twitter account. The hackers have since been identified and arrested by the FBI.
If supposedly savvy, high-level Twitter employees can become victims of social engineering, it should give us all pause. The employees were likely trained in social engineering prevention and had protections in place including 2FA. However, the current remote work situation adds another level of difficulty when it comes to identity verification. Now more than ever, it is important to take steps to protect your digital credentials when identity is at stake.
An example from a Luminary
One member of our advocate program, The Luminaries, agreed to share an interesting case detailing his experience with social engineering. A high-level support agent at a U.K.-based MSP, he was informed some years ago about a suspected phishing attempt against a client. The client, a large U.K. utilities company, has much to lose were this phishing attempt to succeed.
This attack began with an email to a senior employee that read as follows:
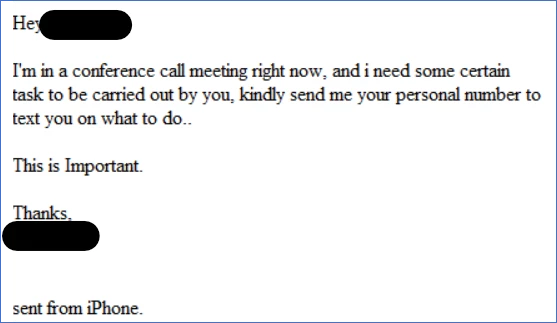
There are some tell-tale signs of manipulation here. There is a sense of urgency and a vague and immediate request for more info. It’s a classic use of the foot-in-the-door technique to solicit contact info and urgency to prevent the receiver from thinking too much about the request.
The email recipient sent the response:

Luckily, the intended victim did not act too hastily, but did confirm their personal phone is the same as listed on their email signature.
What happened from here? The recipient of the phishing email began receiving text messages from an unknown phone number, likely with a spoofed area code to appear more legitimate.
That text message read:
“Hi x, good day this is y, I need you to complete a task real quick let me know as soon as you get my text.”
At this point the MSP was alerted to the suspicious messages. They identified all employees involved and quickly confirmed the sender was not who they claimed. From there, all communications stopped between the employee and the would-be attacker. The utilities company took this incident as an opportunity to tighten its security infrastructure implement 2FA policies. They also re-trained employees on security and anti-phishing policies, ultimately preventing what could have been a costly infiltration of their network.
Social Engineering Prevention
By now, it should be clear that no company or person is immune to social engineering. With contact easily found via social media, email mail signatures, and data leaks, it is important to remain vigilant in online interactions. It’s much easier to hack a person’s psychology than their technology
That’s why security awareness programs are so valuable today. Users must be trained regularly to avoid falling for social engineering attempts. Even tech-savvy individuals can be manipulated by a shady email if allowed to let their guard down.
Cyber resilience only extends to the least safe user in a company.
Stay prepared. Stay vigilant. And stay safe out there.


