If you're finding these helpful, let us know in the comments below. We want to hear from you!
Ransomware Magic Solutions Not So Magic
Great read on how businesses offering to “decrypt data” really were just great hagglers to ransomware criminals.“As ransomware attacks crippled businesses and law enforcement agencies, two U.S. data recovery firms claimed to offer an ethical way out. Instead, they typically paid the ransom and charged victims extra.”
Over 10 Million Australians Breached
10.5 million Australians (or about 40% of the population) were breached in a single incident this year. This is according to the Office of the Australian Data Information Commissioner(or OAIC)'s quarterly report. The mega-breach wasn’t named due to protocol but some big suspects including the Marriot breach were floated as culprits. These was also a huge catalogue of other attack stats outlined in its report and none of them look too rosy for Aussie privacy.GozNym Banking Trojan Network Taken Down
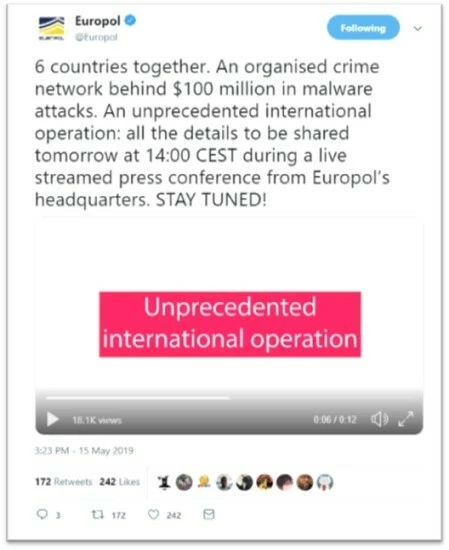
It seems no-one is above click-bait these days. 2 days ago Europol put out a the kind of teaser you’d associate with Game of Thrones and not the European Union’s Law Enforcement Agency.Stay Tuned! Euro-teaser on Twitter
As promised though the news was big. Hot on the heels of two Darkweb marketplace busts this month, Europol have announced more seizures. GozNym is a cybercriminal network that was built around infecting machines with banking trojans and managed to steal about $100 million dollars. As we mentioned last week these takedowns and cases can take time to process. The network’s heyday was in 2015 but justice is finally catching up to its organizers. As of now 10 (mostly European and Russian) individuals have been issued US indictments.
Huawei in the Bad Books
Huawei are a huge firm. Their end-of-year report for 2018 put profits at over $100 billion. It hasn’t been all plain sailing recently though. In March Microsoft found back-doors on Huawei laptops and the company has been involved in a fight for it’s reputation as intelligence agencies in the US and UK in particular accused the company of acting as a Chinese state agent.More bad news for the company this week as the US president announced an incoming ban on American telecommunications firms from installing foreign-made equipment that could pose a threat to national security.
As my rough looking table here shows, the information you have and trade can be stolen at many different levels if a government or group compromises them.
The US and a lot of other countries have been guilty of similar supply-side tactics in the past and maybe the new US focus of protectionism has something to do with the announcement as well as the credible accusations of Chinese spying.
Political Interference on Facebook
- Facebook just took down 265 pages run by an Israeli company, Archimedes Group. The group draws a lot of parallels to Cambridge Analytica but focussed mostly on spreading propaganda in the middle east and Africa
- Fact checker site Snopes have finished a large investigation into “Radical Evangelicals Spread[ing] Anti-Islamic Vitriol on Facebook”.