-----
Shadow Hammer
Chances are you know the company ASUS, the brand name has been ubiquitous with laptops for many years. They have been the victims of an incredible supply-chain attack which has affected over a million machines according to a report from Kaspersky. The outbreak has shown Webroot’s responsiveness to this malware in a very positive light.What are supply-chain/supply-side attacks?
There are a lot of different components involved in running a modern computer system. To keep things running at any kind of decent speed, you have trust the hardware, software and other code involved to carry out sensitive operations. At the end of 2017 CCleaner was famously hacked and the update they were about to ship out to their customers was tweaked by hackers to include malicious code. CCleaner was a wildly popular utility at the time and 2.3 million users ran this compromised update before it was discovered.In the same year a popular Ukrainian tax software company was also similarly breached to maximize the spread of NotPetya. NotPetya was spread by a state actor with the sole purpose of destruction and it brought operations in the country and elsewhere to a standstill.
Supply-side attacks don’t have to involve updates and can take on lots of different forms. Attacks on MSPs and RMMs (both trusted components of a modern business) are on the rise and recent attacks on gaming companies (to ultimately get to gamers) prove that these kind of attacks aren’t limited to the corporate sphere.
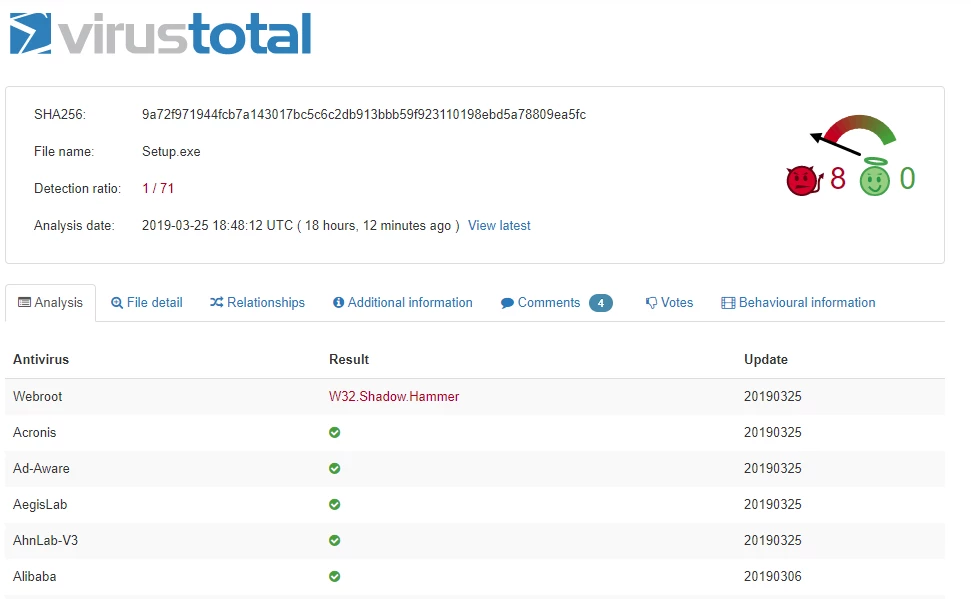
Yesterday Webroot was the only vendor on Virustotal to detect the sample (md5 55a7aa5f0e52ba4d78c145811c830107)
Even in the high tech world of these kinds of attacks, the recent attack on ASUS and its' users stands out for its sophistication and audacity.
ASUS were the first victims of the attackers. Next, their upcoming ASUS Live Utility Update was altered to include a malicious version of the utility with a custom trojan called Shadow Hammer. As with other similar supply chain attacks (such as the CCleaner hack) this was an operation affecting many people with the ultimate purpose of compromising a few:
Am I a victim?
As reported by The Register, there are ways for you to check. If you are, then get onto your AV and make sure you download the latest (and correct) ASUS update from the manufacturer.Also be sure to mark your calendars for April 8th as a full report will be made available about this incident.