Hi Kiran,
When are Site Only Admins going to have the ability to manage DNS settings in the GSM? This is becoming a real hassle for our team.
Thanks,
Alex
Understand your concern Alex. We are looking at simplifying and modifying the Access control side of things.. I would like to hear about your specific requests, ie: As a Site Admin, what are all the DNS and SAT features are you interested in having WRITE ability on.
Thanks
-Kiran
Hi Kiran,
Thanks for the quick reply. Right now our biggest concern is that we cannot grant any access for site admins. In Co-IT environments we can't grant our customers the ability to control their own site for DNS. Not having control over their own environment is making their experience with Webroot very frustrating.
Regards,
Alex
I have only just started to roll this product out and I have not had good results so far. I have just had to roll it back from a site with 117 endpoints as it was changing the computers DNS to 127.0.0.1 and as such killing all internet connectivity. Given this is a 100% Citrix site that meant it killed productivity for the whole office. I read the forums and it was my interpretation that this particular issue was caused by the NIC not initialising before the DNS service started and that this was resolved months ago, I guess not.
I have a couple of other smaller sites that have not complained of this issue at all so for me it is a mixed bag. I am certainly putting my rollout of this on hold as I am not confident in the product as it stands. I have 158 sites in my GSM so I need to be confident in the product so I don't create a widespread negative impact.
AndrewHonestly our experience hasn't been great. We're an MSP and we're using this with the hope of having a managed DNS offering for our clients as we haven't used one up until now.
Since deploying we're having struggles with it. We have problems where techs go onsite to clients and can't get at the internet. Disbling Webroot DNS always solves the issue.
Another example is today, I updated my Windows 10 to the latest 1903 feature update and after rebooting, my machine would not connect to the internet or our domain. I have do disable Webroot DNS to get this to work again.
We're not having problems all the time but it's frequent enough that we're getting frustrated with the product.
We believe there may be times where we're in tightly secured areas and the custom ports Webroot requires are not open. In those situations, it reverts back to our previously set DNS which was from our internal network and won't work when at a different site. That seems to be a bad design. To me it should revert to Dynamic DNS and then prompt the user with a warning that they're not protected. I'm worried if we start deploying this to client machiness we're going to be getting a lot of clients complaining with issues.
Good to hear others are still facing similar issues with the DNS client. The site I manage sees this from time to time as-well across some of our machines. I also see this: The NIC reports no internet connectivity at times (yellow exclamation in taskbar :: 'No internet access' status) but yet there is actually Internet. (Can ping 1.1.1.1, ping google.ca, etc aswell as navigate to Internet based sites from the machine).
If I disable the agent or restart DNS by re-applying "Automatic DNS configuration" it seems to fix the issue (but not permanently).
Another issue to add:
End user will report that their PC is extremely slow. When the Task Manager is opened you can intermittently see WebRoot and the Windows Network Service killing the HD. It pins the usage at 100%.
Since it's a combination of the Network Service + WebRoot it has me thinking it must somehow be related to the WebRoot DNS implementation somehow.
If I modify my default policies to allow a manual shutdown of the WebRoot application and then tell them to refresh their configuration -- they report that shutting down WebRoot instantly solves the issue. (I've seen it myself too)
During these periods of slowness WebRoot is not scanning nor is the PC under any particular load.
Chiming in to add a solution for the issues in my last two posts. The following group policy change has *so far* (knocks on wood) solved all of my issues with the DNS client on the pilot PC's I've tested with.
It appears the issues all boiled back to a problem with the PC's not behaving correctly when the DNS settings are configured for the local loop back interface. From what I understand, this GP change enables/better facilitates handling DNS over the local loopback address. (127.0.0.1)
Note: You will need administrative rights.
Hit the Windows key on your keyboard, begin typing "Group Policy".
Select the following result:
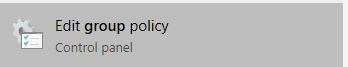
Navigate through the GP tree as follows:
Computer Configuration
- Administrator Templates
-- Network
--- Network Connectivity Status Indicator
Change it from Not Configured (or Disabled) to
Enabled.
Ensure the "Use global DNS" checkbox is also
selected.
Apply and OK.
Reboot PC to ensure changes take effect.
We have one site that has rolled out DNS protection to 10% of their endpoints as a trial. 6 of the endpoints will not adopt the assigned DNS policy, have reduced protection as a result, and are showing a generic/non-branded block page instead of the client's custom block page.
Not a great first look for us.
We are an MSP serving exclusively dental offices.
It's mostly been fine, but we get conflicting advice from Webroot support about adding *.domain.local and domain.local to the bypass list or not.
We also found a few instances where Webroot DNS was stopping programs from running that the dental office relied on. When I asked support what exactly was being blocked, no one could tell me, they just showed me how the app worked fine with DNS off. We uninstalled the DNS agent from endpoints for those customers.
We had a few instances as well with BrightCloud marking sites unsafe or blocking them incorrectly. While BrightCloud support was quick to respond, it still took too long in the clients mind since it was blocking them from doing their jobs. Creating an exception for the site locally did not seem to work in removing the warning or block.
-Mike
Less expensive DNS filtering with better reporting and firsthand ability to whitelist (instead of submitting a request to a third party) is readily available from other vendors. Other solutions offer the ability for users to submit whitelist requests directly to you (the IT provider and DNS filtering reseller), and you can whitelist and have it in effect in 1 to 2 minutes. I currently pay $5 for up to 1 million DNS requests regardless of the number of clients. If I were using WebRoot’s solution at $1.60 per device, over twice as much with my current DNS client base.
I have only just started to roll this product out and I have not had good results so far. I have just had to roll it back from a site with 117 endpoints as it was changing the computers DNS to 127.0.0.1 and as such killing all internet connectivity. Given this is a 100% Citrix site that meant it killed productivity for the whole office. I read the forums and it was my interpretation that this particular issue was caused by the NIC not initialising before the DNS service started and that this was resolved months ago, I guess not.
I have a couple of other smaller sites that have not complained of this issue at all so for me it is a mixed bag. I am certainly putting my rollout of this on hold as I am not confident in the product as it stands. I have 158 sites in my GSM so I need to be confident in the product so I don't create a widespread negative impact.
AndrewHonestly our experience hasn't been great. We're an MSP and we're using this with the hope of having a managed DNS offering for our clients as we haven't used one up until now.
Since deploying we're having struggles with it. We have problems where techs go onsite to clients and can't get at the internet. Disbling Webroot DNS always solves the issue.
Another example is today, I updated my Windows 10 to the latest 1903 feature update and after rebooting, my machine would not connect to the internet or our domain. I have do disable Webroot DNS to get this to work again.
We're not having problems all the time but it's frequent enough that we're getting frustrated with the product.
We believe there may be times where we're in tightly secured areas and the custom ports Webroot requires are not open. In those situations, it reverts back to our previously set DNS which was from our internal network and won't work when at a different site. That seems to be a bad design. To me it should revert to Dynamic DNS and then prompt the user with a warning that they're not protected. I'm worried if we start deploying this to client machiness we're going to be getting a lot of clients complaining with issues.
Good to hear others are still facing similar issues with the DNS client. The site I manage sees this from time to time as-well across some of our machines. I also see this: The NIC reports no internet connectivity at times (yellow exclamation in taskbar :: 'No internet access' status) but yet there is actually Internet. (Can ping 1.1.1.1, ping google.ca, etc aswell as navigate to Internet based sites from the machine).
If I disable the agent or restart DNS by re-applying "Automatic DNS configuration" it seems to fix the issue (but not permanently).
Wow, these issues are still occurring? They’ve been plaguing WebRoot DNS since the beginning, and quickly drove me to another vendor. There are rock solid solutions available for less money. WebRoot would be wise to stay out of the DNS game and focus on what they know. DNS filtering has not worked out well for them.
Kiran,
We use your secure DNS and it has worked pretty well for me so far. I am just using the basic medium protection with a few exceptions. We have not implemented anything advanced yet. With that said I have found what I believe could be a major flaw in process. When your product is down or suffers from degraded performance, you customers should be actively alerted of this issue. Its nice that you have a status monitor available but an email or sms message to your customer would prevent cost incurred by lost productivity and employee frustrations. I would love to see that implemented. I believe that would prevent hours of end users reporting issues to internal IT departments that eventually get passed up to network and system engineers to investigate that may take another couple of hours.
Just a suggestion that I would love to see to improve your product.
Justin
Hey @kkumar
I’d like to see a few things.
- MAC OS X native support
- real-time alerts when people visit a site or blocked category
- DHCP support
- The ability to have the DNS Block Page settings and format completely separate from the users of the Web filter from the AV only.
Cheers
John Hart
Hello,
We have a client who is using Webroot DNS protection. For the most part it is working well but they have been experiencing some issues. I am hoping someone can help me understand what is occurring here and hopefully find a fix.
“ I tried to hit a few gambling and nudity sites today to continue to make sure the service is working.
When I try to hit a site direct via the browser address bar, the warning page pops up; all good.
If I google the same web page and try to launch from google results page, it goes into a “waiting for response” mode and does nothing. All links on the entire page then become unusable and I have to close the browser.
If I hit the same sites on my personal device they open fine. Seems like the service doesn’t work the way intended when launching from a google search. Thoughts?”
Any help would be appreciated. Thanks,
- SayHelloMike
Hello @SayHelloMike
Thank you for the note. It really shouldn’t matter whether you go directly or from google as destination is the same. I think this is something super quick we can look at and take care of it .. would you please contact support - they can definitely assist you and make sure you are set.
Thanks
-Kiran
Hi Kiran
Using the Webroot DNS with success for the most part. I have two computers (same build as the others in the business) which when they have the Webroot DNS installed they cannot contact their email either via Outlook or the web portal route. Webroot support have had a look several times now, taken logs and packet tracing etc but offer no clue as to why the Webroot DNS stops email from functioning. The support team have suggested that a beta Webroot DNS may work better. This was suggested several months ago now and seems like the suggestion was to put off actually looking at and solving the problem that the software causes on these computers. I am starting to look at alternatives to Webroot.
Hello @WanderingAround - I think I know what is going on here. Please hold off before you go an alternate route and give us an opportunity.
So, do you notice an icon that says “Internet is not available” on the machine where you can’t access O365, etc? In reality you do have Internet but its actually MSFT thats unable to reach its DNS verification domain. If I could please send me your email privately, etc I will personally connect you with Support and get this resolved swiftly.
Appreciate the reach out.
Thanks
-Kiran
Hi Kiran, I’ll email you with more detail if you like. The Internet icon is OK and has internet connection just fine. It is not O365. Web pages work just fine. Only when adding Webroot DNS protection does all access to email stop. Removing Webroot DNS fixes the issue and email can continue. As I have said your Webroot support team have already looked into this issue several times now and have come up with no solutions or suggestions as to why the Webroot DNS software is behaving this way and causing trouble.
We were excited to use this product as an additional layer of protection for roaming users who would not connect via VPN (which would put them behind our firewall and web filtering). Instead, they were connecting with the broadband card in their laptop. But it appears that the product cannot modify the DNS settings in the (Verizon) adapter. Will that be overcome in the future?
I am having a lot of issues with the DNS agent since the latest Windows 10 update. The DnsProxyAgent service keeps stopping, and when raoming users leave the corporate network they now have no internet access (no DNS resolution) which also breaks our RMM agent and TeamViewer from “calling home”, so we can’t even remote to the machines to fix them. We have to call the customer user and walk them through starting the service from a command prompt. This is not practical from a support standpoint, and we are now evaluating Cisco Umbrella MSP as a possible replacement.
Dave,
I could use your help. I like Webroot, but the DNS protection has not work successfully for me. We are an MSP and was looking to add the DNS Protection as an offering. First site with 80+ nodes and constantly have to stop Webroot DNS protection and enable auto dhcp. DNS blocks VPN traffic to network drives that should be excluded by the network name. Then the computer will be blocked from all DNS request. HELP!!!! Customer has started asking for removal of software.
Hi @pbsxombie ,
I just reached out to support who informed me that it’s best to open a ticket with them as they will most likely need to remote in to see what’s going on.
You can reach them here.
Its an OK product but still has some shortcomings VS product like cisco umbrella.
- Site-level control of Blocked categories. We would prefer to use as few standardized policies at the top level as possible to avoid managment nightmare. I would prefer site-level management of blocked categories.
- support for sites without static UP (DHCP) Cisco had a simple solution and developed their own No-IP style agent that would update their servers with the site's current dynamic public IP.
- Reporting and report automation. If we are going to use this as an MSP tool. It sure would be nice to have some reporting capability and to be able to automate those reports via email. Some business owners would like to know where their staff is spending time on the internet. Cisco had great reporting.
- THE DNS servers provided by Webroot seem unreliable at best and just don't work well with some routers/gateways. This seems to be a constant issue with Sonciwalls and Unifi Gateway products. When you put in Webroot DNS servers for your region it tends to cause issues. Ciscos on the other hand tended o make your DNS response times faster than using the Local ISP DNS>
Apparently, the latest updates to Webroot have been a complete disaster. They blocked by VPN connection to UCLA, my employer, and my Thunderbird access to my email. I had to disable Webroot to use these things. I guess Webroot would have to stay disabled for the time being. I will not be renewing my subscription, either.
@marvizon are you a Consumer or a Business user? This thread is for Business users that use Webroot’s DNS service.
Thanks,
Oh, I am so, so sorry that Webroot’s messy website led me to the wrong place when I was trying to find some information for why Webroot completely messed up my Thunderbird email and my VPN to UCLA. Still, from what I read here, these problems are quite widespread.



