Hi everyone! Question for you -- are email and email attachments protected by Webroot?
Page 1 / 1
Hello acellis,
Welcome to the Webroot Community,
Emails aren't scanned by Webroot, but as soon as you try to run a malicious attachment WSA would block the execution and protect your PC. Also if you would click on a link in an email the URL will be scanned against the cloud database.
You have to keep in mind that WSA works a bit different than other antivirus solutions; instead of scanning everything all the time and wasting hardware resources, Webroot tries to intelligently protect your PC against threats.
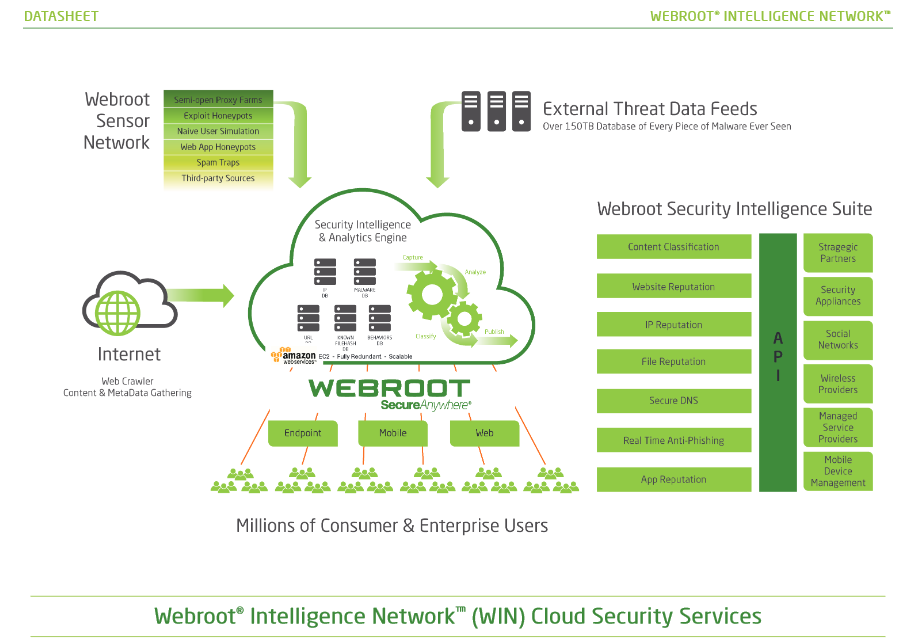
The Webroot WIN Cloud does all the work not your PC: http://www.brightcloud.com/platform/webroot-intelligence-network.php
Here is the PC User Guide
http://live.webrootanywhere.com/content/1332/Webroot-SecureAnywhere-for-PC-Overview
Hope this helps?
Welcome to the Webroot Community,
Emails aren't scanned by Webroot, but as soon as you try to run a malicious attachment WSA would block the execution and protect your PC. Also if you would click on a link in an email the URL will be scanned against the cloud database.
You have to keep in mind that WSA works a bit different than other antivirus solutions; instead of scanning everything all the time and wasting hardware resources, Webroot tries to intelligently protect your PC against threats.
The Webroot WIN Cloud does all the work not your PC: http://www.brightcloud.com/platform/webroot-intelligence-network.php
Here is the PC User Guide
http://live.webrootanywhere.com/content/1332/Webroot-SecureAnywhere-for-PC-Overview
Hope this helps?
It's 2018 so I'm guessing this hasn't changed?
Understanding how Webroot works is what got me to question how it works with email, since that has been the number one attack vector at customers. The customers' emails are scrubbed at the mail server, but they still get through. Users still get tricked all to often, especially young, new employees.
Webroot's anti-ransomware is certainly novel because it can mitigate the damage from zero-day ransomware threats. However, I'm not wild about the idea of having malware emails and files lying dormant on a computer and having it become a source of infected files through email or network sharing.
Let me know if I'm missing something here, but it appears that the malware lies dormant and undetected unless the machine where it is installed attempts to execute it, and links in emails are not checked until you attempt to follow the link?
Thanks!
Understanding how Webroot works is what got me to question how it works with email, since that has been the number one attack vector at customers. The customers' emails are scrubbed at the mail server, but they still get through. Users still get tricked all to often, especially young, new employees.
Webroot's anti-ransomware is certainly novel because it can mitigate the damage from zero-day ransomware threats. However, I'm not wild about the idea of having malware emails and files lying dormant on a computer and having it become a source of infected files through email or network sharing.
Let me know if I'm missing something here, but it appears that the malware lies dormant and undetected unless the machine where it is installed attempts to execute it, and links in emails are not checked until you attempt to follow the link?
Thanks!
Hi IT_Architect
Welcome to the Community Forums.
I could reply/explain but I think you need the 'professional' response to this...@ , would you provide the OP with the benefit of the 'official' answer on this, please?
Regards, Baldrick
Welcome to the Community Forums.
I could reply/explain but I think you need the 'professional' response to this...
Regards, Baldrick
Thanks! I'll wait for that
We do not have an email protection product, but if an email gets through your email protectction, Webroot will still protect the endpoint from email-based attacks. We do not currently detect non-executable attachments, but the actual malicious executable payloads will be blocked when they are downloaded and/or executed. The detection of non-executable files is something that is being worked on. URLs are checked when the URLs are visited.@ wrote:
It's 2018 so I'm guessing this hasn't changed?
Understanding how Webroot works is what got me to question how it works with email, since that has been the number one attack vector at customers. The customers' emails are scrubbed at the mail server, but they still get through. Users still get tricked all to often, especially young, new employees.
Webroot's anti-ransomware is certainly novel because it can mitigate the damage from zero-day ransomware threats. However, I'm not wild about the idea of having malware emails and files lying dormant on a computer and having it become a source of infected files through email or network sharing.
Let me know if I'm missing something here, but it appears that the malware lies dormant and undetected unless the machine where it is installed attempts to execute it, and links in emails are not checked until you attempt to follow the link?
Thanks!
-Dan
>but the actual malicious executable payloads will be blocked when they are downloaded and/or executed<
Does that mean that they would be stripped from POP3 messages when they are downloaded into Outlook?
Does that mean that they would be stripped from POP3 messages when they are downloaded into Outlook?
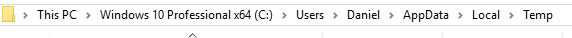
When something tries to download WSA's Realtime Shield will see where it tries to download to and stop it at that point and most times they download to the AppdataLocalTemp Folder.
HTH,
Daniel
https://www.youtube.com/watch?v=v3gjcOH9kec
https://www.youtube.com/watch?v=qy5o2wIwUDk
HTH,
Daniel
https://www.youtube.com/watch?v=v3gjcOH9kec
https://www.youtube.com/watch?v=qy5o2wIwUDk
Got it! I'm just trying to draw circles around what it does and doesn't do. So it sounds like anything could get on your hard drive via network, ftp, etc., but until you actually touch it, it will remain on disk undetected until its daily scheduled scan, and email when you click on an attachment or any time you attempt to follow a link.
You could have a bad .exe but it doesn't do anything unless you click on it an run the file so again it will detect on download or on execution so either way your protected by WSA's Realtime Shield. Muti-Vector Protection! 😉
I have what I need to know. Thanks all!
Great and if you have any further questions feel free to ask. Myself I have been using WSA since the beginning in early 2011 for the first release of the 2012 version and I have never been infected and will continue to use WSA.@ wrote:
I have what I need to know. Thanks all!
Cheers,
Daniel 😉
The executable payloads are not contained within the emails, they are downloaded from an external site using a script, macro, or other exploits contained within the attachments. Once the executable is actually downloaded, it would be detected/blocked.@ wrote:
>but the actual malicious executable payloads will be blocked when they are downloaded and/or executed<
Does that mean that they would be stripped from POP3 messages when they are downloaded into Outlook?
>The executable payloads are not contained within the emails, they are downloaded from an external site using a script, macro, or other exploits contained within the attachments. Once the executable is actually downloaded, it would be detected/blocked.<
They COULD link to a file from an attachment but attachments of any kind are part of the email and usually encoded in MIME Base 64. I guess I am to assume that when the executable from an attachment is reconstructed and attempts to execute, it would be caught.
This question was also asked of Microsoft:.
Question: Does Windows Defender scan email?
Answer: No. There is no need for this to be done. What is important are attachments and links in email. When you attempt to open or save an attachment, or open a link, Windows Defender’s real-time protection inspects those items.
Thus, while not indicating that I'm convinced leaving infected files and emails laying about where they can be forwarded, Webroot is not alone in their approach.
They COULD link to a file from an attachment but attachments of any kind are part of the email and usually encoded in MIME Base 64. I guess I am to assume that when the executable from an attachment is reconstructed and attempts to execute, it would be caught.
This question was also asked of Microsoft:.
Question: Does Windows Defender scan email?
Answer: No. There is no need for this to be done. What is important are attachments and links in email. When you attempt to open or save an attachment, or open a link, Windows Defender’s real-time protection inspects those items.
Thus, while not indicating that I'm convinced leaving infected files and emails laying about where they can be forwarded, Webroot is not alone in their approach.
Yes, it is true that a possible scenario of Webroot's approach is that infected files could theoretically be forwarded by a Webroot-protected user through email to a recipient or to recipients. This is a scenario that I have already contemplated as an arguable inbuilt weakness of Webroot's technology.@ wrote:
...leaving infected files and emails laying about where they can be forwarded...
But I suppose the argument Webroot would come back with is that the protection of that third party is not their primary remit, but they are providing as powerful and at the same time as lightweight a protection of their users' computers as possible.
>Yes, it is true that a possible scenario of Webroot's approach is that infected files could theoretically be forwarded by a Webroot-protected user through email to a recipient or to recipients. This is a scenario that I have already contemplated as an arguable inbuilt weakness of Webroot's technology.<
Because Webroot has so many plusses I am evaluating software to mitigate this.
Thanks all!
Because Webroot has so many plusses I am evaluating software to mitigate this.
Thanks all!
One of the superb pluses is its featherweight footprint on the device. Might not additional email-attachments-monitoring security software risk compromising this?
>Might not additional email-attachments-monitoring security software risk compromising this?<
To some degree until or if Webroot comes up with their own. It would seem that adding it would allow them to use the same engine and very few system resources, and I would think it would not be heavy on their in-house resources and development resources. They have said they are looking at it, but reality is most likely it will be decided whether there is enough benefit for them financially to add it.
To some degree until or if Webroot comes up with their own. It would seem that adding it would allow them to use the same engine and very few system resources, and I would think it would not be heavy on their in-house resources and development resources. They have said they are looking at it, but reality is most likely it will be decided whether there is enough benefit for them financially to add it.
The other thing to bear in mind is that, by adding another AV, you partially sacrifice the rollback function. This is because the way Webroot is designed to be compatible with other AVs is that, in the event both AVs detect an infection at the same time, Webroot will always step back and allow the other AV to do the disinfection. But by doing this, you lose the Webroot function whereby any changes that were made to your machine by that infection, which have been journaled by Webroot, are rolled back. This apparently canot be done when another AV disinfects your machine.
I expect it will end up proxying+scanning+spam classifying, not using another AV program.
PS: I already proxy+spam classify now.
PS: I already proxy+spam classify now.
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.