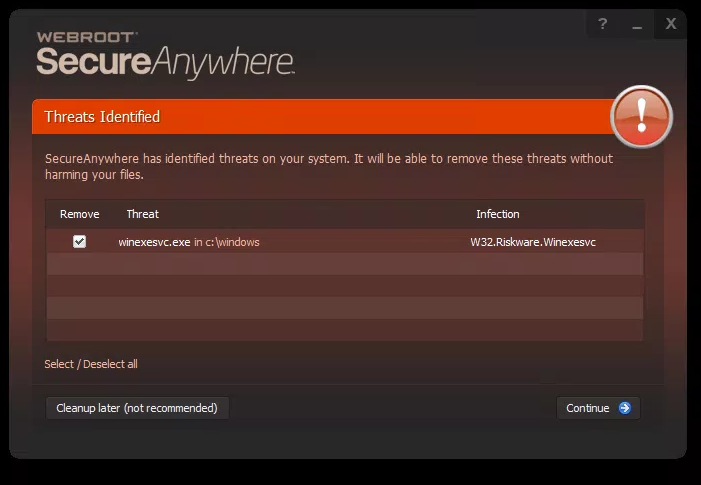
Hi,
I'm seeing quite a few alerts detecting winexesvc.exe as w32.hack.tool.winexe this morning.
Is this a false positive - popped up on an otherwise not active PC after overnight's Windows updates?
Anyone else seeing this?
Edwin
Page 1 / 1
I came here with the same question. Post Windows Update, lots of winexesvc.exe threats detected.
it seems to have stopped now - anybody from techsupport care to comment?
Is a rollback/restore needed?
Is a rollback/restore needed?
Hi,
I'm also getting a lot of these detections on protected endpoints. The files are being quarantined but I would like to know the main cause or if any preventive measures can be set in place to lower the alerts.
I also saw on the web where these could be generated from a Linux server pushing files to a windows machine... what are your thoughts?
These alerts started for me around yesterday morning and they've escalated up to this time. This threat is not Windows OS specific as I've had alerts from both Windows 7 and Windows server OS.
I'm also getting a lot of these detections on protected endpoints. The files are being quarantined but I would like to know the main cause or if any preventive measures can be set in place to lower the alerts.
I also saw on the web where these could be generated from a Linux server pushing files to a windows machine... what are your thoughts?
These alerts started for me around yesterday morning and they've escalated up to this time. This threat is not Windows OS specific as I've had alerts from both Windows 7 and Windows server OS.
Please submit a ticket to our Support Team so they can review the logs to make a proper determination.
done.
Hi there,
Same is happening here. We have found out that our Unitrends Backup Appliance is using winexesvc.exe to push updates out to computers it is backing up. Just a heads up to other people wondering how the application got there.
Same is happening here. We have found out that our Unitrends Backup Appliance is using winexesvc.exe to push updates out to computers it is backing up. Just a heads up to other people wondering how the application got there.
Hello 10d,
This file "winexesvc.exe" is related to the Windows Subsystem for Linux feature and allows remote commands to be sent to all systems in a network. Because of the enormous potential to be used maliciously, Webroot has classified this file malicious as it is potentially un-safe. If this program is needed in your environment, you may create an override and restore it from Webroot's quarantine via the Webroot Console.
For steps to override this file, please visit the link below.
http://live.webrootanywhere.com/content/1384/Creating-Whitelist-Overrides
Please let us know if we can explain anything in further detail.
Regards,
Jesse L.
Webroot Advanced Malware Removal Team
This file "winexesvc.exe" is related to the Windows Subsystem for Linux feature and allows remote commands to be sent to all systems in a network. Because of the enormous potential to be used maliciously, Webroot has classified this file malicious as it is potentially un-safe. If this program is needed in your environment, you may create an override and restore it from Webroot's quarantine via the Webroot Console.
For steps to override this file, please visit the link below.
http://live.webrootanywhere.com/content/1384/Creating-Whitelist-Overrides
Please let us know if we can explain anything in further detail.
Regards,
Jesse L.
Webroot Advanced Malware Removal Team
Thanks Jesse for the background.
I s this happening because Windows 10 is extending the Linux subsystem feature with newer versions?
I s this happening because Windows 10 is extending the Linux subsystem feature with newer versions?
Webroot blocked WINEXESVC.EXE on one of my Exchange2010 servers that uses Datto backup. Consequently the backups were not running. I have since restored from quarantine and added and policy override.
Thanks for letting us know what worked for you, @ ! Very much appreciated.
This is still a problem!!! Brand new Unitrends DRaaS as of 09-13-2019 and WR has just shutdown the backup agent... granted I didn't preconfig and create an exception for this; but I don't think this should be on the default list.. Can this not be digitally signed by Unitrends to prevent this from happening? I could write a volume novel with everything I don't understand; but this one escapes me...
The appliance is attempting to push to a Win 2012-R2 Server...
NAME="RecoveryOS"
VERSION="7 (Core)"
ID="centos"
ID_LIKE="rhel fedora"
VERSION_ID="7"
PRETTY_NAME="RecoveryOS 7 (Core)"
ANSI_COLOR="0;31"
CPE_NAME="cpe:/o:centos:centos:7"
HOME_URL="https://www.centos.org/"
BUG_REPORT_URL="https://bugs.centos.org/"
CENTOS_MANTISBT_PROJECT="CentOS-7"
CENTOS_MANTISBT_PROJECT_VERSION="7"
REDHAT_SUPPORT_PRODUCT="centos"
REDHAT_SUPPORT_PRODUCT_VERSION="7"
The appliance is attempting to push to a Win 2012-R2 Server...
NAME="RecoveryOS"
VERSION="7 (Core)"
ID="centos"
ID_LIKE="rhel fedora"
VERSION_ID="7"
PRETTY_NAME="RecoveryOS 7 (Core)"
ANSI_COLOR="0;31"
CPE_NAME="cpe:/o:centos:centos:7"
HOME_URL="https://www.centos.org/"
BUG_REPORT_URL="https://bugs.centos.org/"
CENTOS_MANTISBT_PROJECT="CentOS-7"
CENTOS_MANTISBT_PROJECT_VERSION="7"
REDHAT_SUPPORT_PRODUCT="centos"
REDHAT_SUPPORT_PRODUCT_VERSION="7"
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.