Hello everyone,
I am experiencing a strange issue which I have seen more than once lately during our trial.
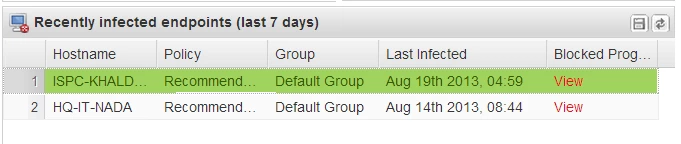
For example, on the status p, under recently infected, I see an endpoint that was infected today at 4:59AM with conflicker virus. However when I cl ick on group management and choose that same endpoint , it shows that it scanned at 4:59AM and the status is clean.
Also, the infection shown in the status is not shown in the reports UNLESS I specifically choose today.
Any idea how to resolve?
*note from admin - I reposted an edited version of your image so as not to include ip addresses*
Page 1 / 1
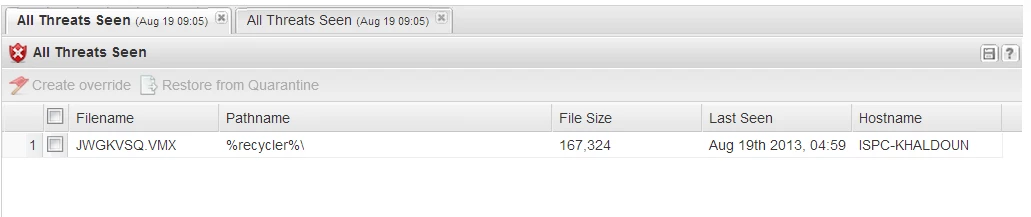
It looks like the threat in the "All Threats Seen" screenshot was picked up with a shield or heuristics rather than a scan. That's why the "Scan History" screenshot doesn't include the threat in it, because it wasn't identified during a scan. The logging doesn't go down to the second in the console version of the scan log, but I suspect the sequence of events probably looks something like "4:59a: dropped conficker on the computer," "4:59b: Webroot shield caught it," "4:59c: Webroot ran a scan that came up clean." Without looking at support logs myself, I can't confirm my analysis, but that would explain it. If you open a support case, Webroot Support can verify.
Threats being blocked might be kind of important to show in the console...
😞
😞
Hi JimM,
I just wanted to create a new message when I found this one.
Today I had a customer case: the PC was infercted with a zero day threat. Good news, just during my support session with the customer, Webroot cloud was updated and finally the threat was removed successfully - meaning whe I started supporting them and ran a scan on the threat file WSA said it was clean but about 10 mins later (and after asking the client to check for updates via its popup menu) the new manual scan removed the threat. So far, this is good news.
(FYI, the treat was: oiicmlfpjj.dll + an EXE and a DAT file with MD5: D36ACF364A545989E89C5413948CB577)
So why am I writing here now?
Because then I went to the WSA console and wanted to see the scan results.
I see this on the console:
I was very suprised that all scans (even those manual scans I ran myself and did find a threat) show CLEAN results. This is obviously not true I thought and then I went to the PC and opened the WRlog.log file to see what it says.
Let's see all the evens in the local log file from today and I let you try to match the times of scans with the times shown on the console - I could not find a single logged scan time being the same in the local log and on the console:
(for your convinience, I marked the scans as [scheduled] or [manual] or [POST CLEANUP] to my best understanding)
Fri 2013-08-23 08:23:27.0281 >>> Service started [v8.0.2.167] -- the user started the PC at this time today morning
Fri 2013-08-23 08:24:18.0046 User process connected successfully from PID 1020, Session 0
Fri 2013-08-23 09:25:46.0767 Connecting to 72 - 72
Fri 2013-08-23 09:25:49.0329 Begin passive write scan (1 file(s))
Fri 2013-08-23 09:25:49.0954 End passive write scan (1 file(s))
Fri 2013-08-23 10:46:09.0379 Begin passive write scan (1 file(s)) -- the infection happened at this time (btw, can we tell from where did this file come?)
ttingscsekevlocal settings empoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 9 (9928)
Fri 2013-08-23 10:45:56.0896 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 3 (9928)
Fri 2013-08-23 10:45:56.0896 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 4 (9928)
Fri 2013-08-23 10:45:56.0896 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 5 (9928)
Fri 2013-08-23 10:45:56.0912 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 8 (9928)
Fri 2013-08-23 10:46:05.0364 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 3 (9928)
Fri 2013-08-23 10:46:05.0364 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 4 (9928)
Fri 2013-08-23 10:46:05.0364 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 5 (9928)
Fri 2013-08-23 10:46:05.0379 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 8 (9928)
Fri 2013-08-23 10:46:09.0379 Begin passive write scan (1 file(s))
Fri 2013-08-23 10:46:10.0676 End passive write scan (1 file(s))
Fri 2013-08-23 10:57:06.0265 [SCHEDULED?] Scan Started: [ID: 283 - Flags: 551/0]
Fri 2013-08-23 10:59:30.0597 Connected to C3
Fri 2013-08-23 10:59:32.0488 Scan Results: Files Scanned: 28245, Duration: 2m 26s, Malicious Files: 0
Fri 2013-08-23 10:59:32.0519 Scan Finished: [ID: 283 - Seq: 75631917]
Fri 2013-08-23 11:13:02.0409 Begin passive write scan (1 file(s))
Fri 2013-08-23 11:13:03.0346 End passive write scan (1 file(s))
Fri 2013-08-23 11:13:20.0409 Begin passive write scan (5 file(s))
Fri 2013-08-23 11:13:21.0659 End passive write scan (5 file(s))
Fri 2013-08-23 11:17:56.0887 [manual] Scan Started: C:Documents and SettingsAll UsersApplication Dataa33aa3ns| [ID: 284 - Flags: 256/4]
Fri 2013-08-23 11:17:58.0856 Scan Results: Files Scanned: 7, Duration: 1s, Malicious Files: 0
Fri 2013-08-23 11:17:58.0903 Scan Finished: [ID: 284 - Seq: 75633025]
Fri 2013-08-23 11:21:10.0688 [manual] Scan Started: C:Documents and SettingsAll UsersApplication Dataa33aa3ns| [ID: 285 - Flags: 256/4]
Fri 2013-08-23 11:21:11.0391 Scan Results: Files Scanned: 7, Duration: 1s, Malicious Files: 0
Fri 2013-08-23 11:21:11.0406 Scan Finished: [ID: 285 - Seq: 285]
Fri 2013-08-23 11:26:41.0448 Begin passive write scan (1 file(s))
Fri 2013-08-23 11:26:42.0698 End passive write scan (1 file(s))
Fri 2013-08-23 11:28:56.0453 Begin passive write scan (6 file(s))
Fri 2013-08-23 11:28:57.0390 End passive write scan (6 file(s))
Fri 2013-08-23 11:44:47.0771 [manual] Scan Started: C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll| [ID: 286 - Flags: 256/4]
Fri 2013-08-23 11:44:48.0114 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 1 (9928)
Fri 2013-08-23 11:44:48.0146 Infection detected: c:documents and settingscsekevlocal settings empoiicmlfpjj.dll [MD5: D36ACF364A545989E89C5413948CB577] [3/100A0801] [Trojan.Dropper.Gen]
Fri 2013-08-23 11:44:48.0708 Scan Results: Files Scanned: 1, Duration: 1s, Malicious Files: 1
Fri 2013-08-23 11:44:48.0755 Scan Finished: [ID: 286 - Seq: 75634635]
Fri 2013-08-23 11:45:10.0068 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 1 (9928)
Fri 2013-08-23 11:45:10.0068 Determination flags modified: c:documents and settingsall usersapplication dataa33aa3nsa33aa3ns.exe - MD5: D36ACF364A545989E89C5413948CB577, Size: 606208 bytes, Flags: 00000020
Fri 2013-08-23 11:45:12.0444 Performing cleanup entry: 1
Fri 2013-08-23 11:45:42.0085 User process connected successfully from PID 1020, Session 0
Fri 2013-08-23 11:47:10.0229 [manual] Scan Started: C:Documents and SettingsAll UsersApplication Dataa33aa3ns| [ID: 287 - Flags: 256/20]
Fri 2013-08-23 11:47:11.0151 Infection detected: c:documents and settingsall usersapplication dataa33aa3nsa33aa3ns.exe [MD5: D36ACF364A545989E89C5413948CB577] [3/100A0821] [Trojan.Dropper.Gen]
Fri 2013-08-23 11:47:11.0870 Scan Results: Files Scanned: 8, Duration: 1s, Malicious Files: 1
Fri 2013-08-23 11:47:12.0073 Scan Finished: [ID: 287 - Seq: 75634778]
Fri 2013-08-23 11:47:14.0464 Determination flags modified: c:documents and settingsall usersapplication dataa33aa3nsa33aa3ns.exe - MD5: D36ACF364A545989E89C5413948CB577, Size: 606208 bytes, Flags: 00000020
Fri 2013-08-23 11:47:15.0901 Performing cleanup entry: 2
Fri 2013-08-23 11:47:16.0620 [manual] Scan Started: C:Documents and SettingsAll UsersApplication Dataa33aa3ns| [ID: 288 - Flags: 256/148]
Fri 2013-08-23 11:47:17.0276 Scan Results: Files Scanned: 7, Duration: 1s, Malicious Files: 0
Fri 2013-08-23 11:47:17.0667 Scan Finished: [ID: 288 - Seq: 288]
Fri 2013-08-23 11:47:33.0136 [POST CLEANUP] Scan Started: [ID: 289 - Flags: 551/16]
Fri 2013-08-23 11:50:07.0283 Scan Results: Files Scanned: 37897, Duration: 2m 34s, Malicious Files: 0
Fri 2013-08-23 11:50:07.0345 Scan Finished: [ID: 289 - Seq: 75634911]
Fri 2013-08-23 11:50:30.0503 [manual]Scan Started: C:Documents and SettingscsekevAsztala33aa3ns.zip| [ID: 290 - Flags: 256/4]
Fri 2013-08-23 11:50:31.0503 Infection detected: c:documents and settingscsekevasztala33aa3ns.zip/a33aa3ns/a33aa3ns.exe [MD5: D36ACF364A545989E89C5413948CB577] [3/100A0821] [Trojan.Dropper.Gen]
Fri 2013-08-23 11:50:32.0096 Scan Results: Files Scanned: 1, Duration: 1s, Malicious Files: 1
Fri 2013-08-23 11:50:32.0128 Scan Finished: [ID: 290 - Seq: 75634978]
Fri 2013-08-23 11:50:52.0425 Determination flags modified: c:documents and settingscsekevasztala33aa3ns.zip/a33aa3ns/a33aa3ns.exe - MD5: D36ACF364A545989E89C5413948CB577, Size: 606208 bytes, Flags: 00000020
Fri 2013-08-23 11:50:53.0253 Performing cleanup entry: 3
Fri 2013-08-23 11:50:53.0690 [manual]Scan Started: C:Documents and SettingscsekevAsztala33aa3ns.zip| [ID: 291 - Flags: 256/132]
Fri 2013-08-23 11:50:54.0331 Scan Results: Files Scanned: 1, Duration: 1s, Malicious Files: 0
Fri 2013-08-23 11:50:54.0347 Scan Finished: [ID: 291 - Seq: 291]
Fri 2013-08-23 11:52:54.0761 Begin passive write scan (1 file(s))
Fri 2013-08-23 11:52:55.0386 End passive write scan (1 file(s))
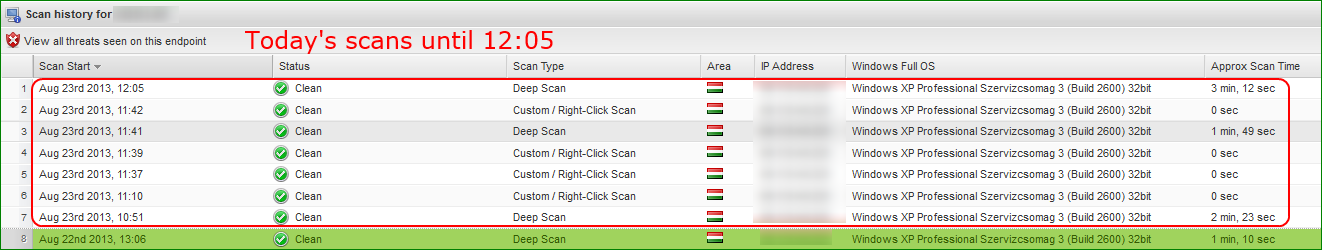
So far you can count a total of 9 scans in the local log file:
8 x [manual] scans : 3 of them found infection and removed the threat
1x [POST CLEANUP] scan
On the console, you can find 7 scans only all together for today until 12:05.
So 2 scans are even not logged to the console!!!
- Why?
- Which one is which then?
Furthermore, the 3 scans that found a threat (IF they are the same scans shown on the console at all???) show incorrect CLEAN status!!!
- Why?
I would prefer seeing the real event logs in the console for all scans happened on the client and of course, if a scan found a threat, I cannot afford it being shown as CLEAN scan result on the console.
Another interesting question is why we cannot find a removal of a file in either the console nor the local log file at all?
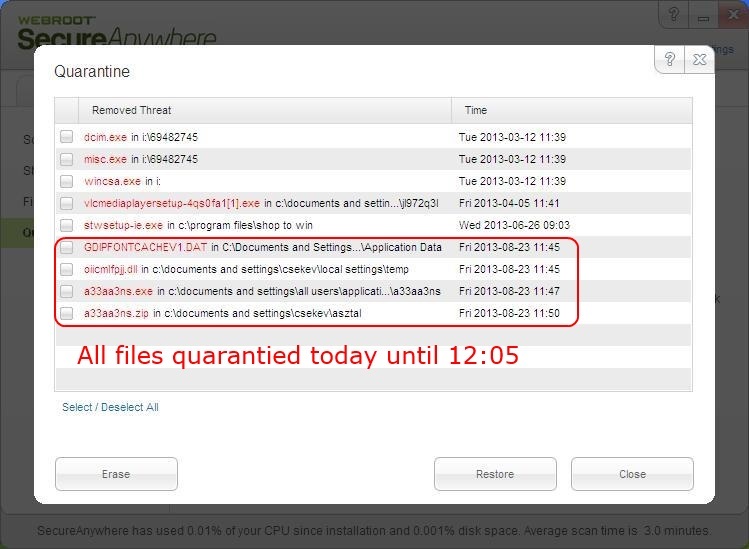
You know, rigth after checking for updates with the client and then running a scan (see logged at 11:44:47.0771) on the SettingscsekevLocal SettingsTempoiicmlfpjj.dll file itself from context menu WSA quarantined that file PLUS another one file called: GDIPF.......V1.DAT
See it in the contents of the local quarantine:
(btw, interesting the last file, a33a33ns.zip was not really quarantined, but only an a33a33.nsexe file from it !!! The same exe was zipped because we were curious to see if WSA can find it in ZIP file as well.)
Why was quarantining the DAT file not logged at all either locally or to the console?
Where can I find the MD5 of that DAT file now?
So far, based on the aboce, WSA loggong is not only inconsistent regarding the relation of local and console logs but also it is inconsistent with real life events (as the DAT file removed is not logged at all)!
Please fix these serious bugs of scan logging asap!
New idea 1: also, you may want to consider marking the scans both in the local log file as [scheduled] or [manual] or [CONTEXT MENU] or [POST CLEANUP] to see clearly what scan was run.
New idea 2: consider showing the contents of the local quarantine on the console per client (so selecting the client and with a new action menu item let us see the quarantine contents of that endpoint and have a chance to create a good/bad override by clicking on the quarantined file).
New idea 3: condider showing the MD5 of the quaratined file in the quarantine view of the WSA client and maybe even create a contect menu that allows you to copy the MD5 of the file to the clipboard - just as you can copy the filename today.
Thank you for your examination and consideration!
I just wanted to create a new message when I found this one.
Today I had a customer case: the PC was infercted with a zero day threat. Good news, just during my support session with the customer, Webroot cloud was updated and finally the threat was removed successfully - meaning whe I started supporting them and ran a scan on the threat file WSA said it was clean but about 10 mins later (and after asking the client to check for updates via its popup menu) the new manual scan removed the threat. So far, this is good news.
(FYI, the treat was: oiicmlfpjj.dll + an EXE and a DAT file with MD5: D36ACF364A545989E89C5413948CB577)
So why am I writing here now?
Because then I went to the WSA console and wanted to see the scan results.
I see this on the console:
I was very suprised that all scans (even those manual scans I ran myself and did find a threat) show CLEAN results. This is obviously not true I thought and then I went to the PC and opened the WRlog.log file to see what it says.
Let's see all the evens in the local log file from today and I let you try to match the times of scans with the times shown on the console - I could not find a single logged scan time being the same in the local log and on the console:
(for your convinience, I marked the scans as [scheduled] or [manual] or [POST CLEANUP] to my best understanding)
Fri 2013-08-23 08:23:27.0281 >>> Service started [v8.0.2.167] -- the user started the PC at this time today morning
Fri 2013-08-23 08:24:18.0046 User process connected successfully from PID 1020, Session 0
Fri 2013-08-23 09:25:46.0767 Connecting to 72 - 72
Fri 2013-08-23 09:25:49.0329 Begin passive write scan (1 file(s))
Fri 2013-08-23 09:25:49.0954 End passive write scan (1 file(s))
Fri 2013-08-23 10:46:09.0379 Begin passive write scan (1 file(s)) -- the infection happened at this time (btw, can we tell from where did this file come?)
ttingscsekevlocal settings empoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 9 (9928)
Fri 2013-08-23 10:45:56.0896 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 3 (9928)
Fri 2013-08-23 10:45:56.0896 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 4 (9928)
Fri 2013-08-23 10:45:56.0896 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 5 (9928)
Fri 2013-08-23 10:45:56.0912 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 8 (9928)
Fri 2013-08-23 10:46:05.0364 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 3 (9928)
Fri 2013-08-23 10:46:05.0364 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 4 (9928)
Fri 2013-08-23 10:46:05.0364 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 5 (9928)
Fri 2013-08-23 10:46:05.0379 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 8 (9928)
Fri 2013-08-23 10:46:09.0379 Begin passive write scan (1 file(s))
Fri 2013-08-23 10:46:10.0676 End passive write scan (1 file(s))
Fri 2013-08-23 10:57:06.0265 [SCHEDULED?] Scan Started: [ID: 283 - Flags: 551/0]
Fri 2013-08-23 10:59:30.0597 Connected to C3
Fri 2013-08-23 10:59:32.0488 Scan Results: Files Scanned: 28245, Duration: 2m 26s, Malicious Files: 0
Fri 2013-08-23 10:59:32.0519 Scan Finished: [ID: 283 - Seq: 75631917]
Fri 2013-08-23 11:13:02.0409 Begin passive write scan (1 file(s))
Fri 2013-08-23 11:13:03.0346 End passive write scan (1 file(s))
Fri 2013-08-23 11:13:20.0409 Begin passive write scan (5 file(s))
Fri 2013-08-23 11:13:21.0659 End passive write scan (5 file(s))
Fri 2013-08-23 11:17:56.0887 [manual] Scan Started: C:Documents and SettingsAll UsersApplication Dataa33aa3ns| [ID: 284 - Flags: 256/4]
Fri 2013-08-23 11:17:58.0856 Scan Results: Files Scanned: 7, Duration: 1s, Malicious Files: 0
Fri 2013-08-23 11:17:58.0903 Scan Finished: [ID: 284 - Seq: 75633025]
Fri 2013-08-23 11:21:10.0688 [manual] Scan Started: C:Documents and SettingsAll UsersApplication Dataa33aa3ns| [ID: 285 - Flags: 256/4]
Fri 2013-08-23 11:21:11.0391 Scan Results: Files Scanned: 7, Duration: 1s, Malicious Files: 0
Fri 2013-08-23 11:21:11.0406 Scan Finished: [ID: 285 - Seq: 285]
Fri 2013-08-23 11:26:41.0448 Begin passive write scan (1 file(s))
Fri 2013-08-23 11:26:42.0698 End passive write scan (1 file(s))
Fri 2013-08-23 11:28:56.0453 Begin passive write scan (6 file(s))
Fri 2013-08-23 11:28:57.0390 End passive write scan (6 file(s))
Fri 2013-08-23 11:44:47.0771 [manual] Scan Started: C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll| [ID: 286 - Flags: 256/4]
Fri 2013-08-23 11:44:48.0114 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 1 (9928)
Fri 2013-08-23 11:44:48.0146 Infection detected: c:documents and settingscsekevlocal settings empoiicmlfpjj.dll [MD5: D36ACF364A545989E89C5413948CB577] [3/100A0801] [Trojan.Dropper.Gen]
Fri 2013-08-23 11:44:48.0708 Scan Results: Files Scanned: 1, Duration: 1s, Malicious Files: 1
Fri 2013-08-23 11:44:48.0755 Scan Finished: [ID: 286 - Seq: 75634635]
Fri 2013-08-23 11:45:10.0068 Monitoring process C:Documents and SettingscsekevLocal SettingsTempoiicmlfpjj.dll [D36ACF364A545989E89C5413948CB577]. Type: 1 (9928)
Fri 2013-08-23 11:45:10.0068 Determination flags modified: c:documents and settingsall usersapplication dataa33aa3nsa33aa3ns.exe - MD5: D36ACF364A545989E89C5413948CB577, Size: 606208 bytes, Flags: 00000020
Fri 2013-08-23 11:45:12.0444 Performing cleanup entry: 1
Fri 2013-08-23 11:45:42.0085 User process connected successfully from PID 1020, Session 0
Fri 2013-08-23 11:47:10.0229 [manual] Scan Started: C:Documents and SettingsAll UsersApplication Dataa33aa3ns| [ID: 287 - Flags: 256/20]
Fri 2013-08-23 11:47:11.0151 Infection detected: c:documents and settingsall usersapplication dataa33aa3nsa33aa3ns.exe [MD5: D36ACF364A545989E89C5413948CB577] [3/100A0821] [Trojan.Dropper.Gen]
Fri 2013-08-23 11:47:11.0870 Scan Results: Files Scanned: 8, Duration: 1s, Malicious Files: 1
Fri 2013-08-23 11:47:12.0073 Scan Finished: [ID: 287 - Seq: 75634778]
Fri 2013-08-23 11:47:14.0464 Determination flags modified: c:documents and settingsall usersapplication dataa33aa3nsa33aa3ns.exe - MD5: D36ACF364A545989E89C5413948CB577, Size: 606208 bytes, Flags: 00000020
Fri 2013-08-23 11:47:15.0901 Performing cleanup entry: 2
Fri 2013-08-23 11:47:16.0620 [manual] Scan Started: C:Documents and SettingsAll UsersApplication Dataa33aa3ns| [ID: 288 - Flags: 256/148]
Fri 2013-08-23 11:47:17.0276 Scan Results: Files Scanned: 7, Duration: 1s, Malicious Files: 0
Fri 2013-08-23 11:47:17.0667 Scan Finished: [ID: 288 - Seq: 288]
Fri 2013-08-23 11:47:33.0136 [POST CLEANUP] Scan Started: [ID: 289 - Flags: 551/16]
Fri 2013-08-23 11:50:07.0283 Scan Results: Files Scanned: 37897, Duration: 2m 34s, Malicious Files: 0
Fri 2013-08-23 11:50:07.0345 Scan Finished: [ID: 289 - Seq: 75634911]
Fri 2013-08-23 11:50:30.0503 [manual]Scan Started: C:Documents and SettingscsekevAsztala33aa3ns.zip| [ID: 290 - Flags: 256/4]
Fri 2013-08-23 11:50:31.0503 Infection detected: c:documents and settingscsekevasztala33aa3ns.zip/a33aa3ns/a33aa3ns.exe [MD5: D36ACF364A545989E89C5413948CB577] [3/100A0821] [Trojan.Dropper.Gen]
Fri 2013-08-23 11:50:32.0096 Scan Results: Files Scanned: 1, Duration: 1s, Malicious Files: 1
Fri 2013-08-23 11:50:32.0128 Scan Finished: [ID: 290 - Seq: 75634978]
Fri 2013-08-23 11:50:52.0425 Determination flags modified: c:documents and settingscsekevasztala33aa3ns.zip/a33aa3ns/a33aa3ns.exe - MD5: D36ACF364A545989E89C5413948CB577, Size: 606208 bytes, Flags: 00000020
Fri 2013-08-23 11:50:53.0253 Performing cleanup entry: 3
Fri 2013-08-23 11:50:53.0690 [manual]Scan Started: C:Documents and SettingscsekevAsztala33aa3ns.zip| [ID: 291 - Flags: 256/132]
Fri 2013-08-23 11:50:54.0331 Scan Results: Files Scanned: 1, Duration: 1s, Malicious Files: 0
Fri 2013-08-23 11:50:54.0347 Scan Finished: [ID: 291 - Seq: 291]
Fri 2013-08-23 11:52:54.0761 Begin passive write scan (1 file(s))
Fri 2013-08-23 11:52:55.0386 End passive write scan (1 file(s))
So far you can count a total of 9 scans in the local log file:
8 x [manual] scans : 3 of them found infection and removed the threat
1x [POST CLEANUP] scan
On the console, you can find 7 scans only all together for today until 12:05.
So 2 scans are even not logged to the console!!!
- Why?
- Which one is which then?
Furthermore, the 3 scans that found a threat (IF they are the same scans shown on the console at all???) show incorrect CLEAN status!!!
- Why?
I would prefer seeing the real event logs in the console for all scans happened on the client and of course, if a scan found a threat, I cannot afford it being shown as CLEAN scan result on the console.
Another interesting question is why we cannot find a removal of a file in either the console nor the local log file at all?
You know, rigth after checking for updates with the client and then running a scan (see logged at 11:44:47.0771) on the SettingscsekevLocal SettingsTempoiicmlfpjj.dll file itself from context menu WSA quarantined that file PLUS another one file called: GDIPF.......V1.DAT
See it in the contents of the local quarantine:
(btw, interesting the last file, a33a33ns.zip was not really quarantined, but only an a33a33.nsexe file from it !!! The same exe was zipped because we were curious to see if WSA can find it in ZIP file as well.)
Why was quarantining the DAT file not logged at all either locally or to the console?
Where can I find the MD5 of that DAT file now?
So far, based on the aboce, WSA loggong is not only inconsistent regarding the relation of local and console logs but also it is inconsistent with real life events (as the DAT file removed is not logged at all)!
Please fix these serious bugs of scan logging asap!
New idea 1: also, you may want to consider marking the scans both in the local log file as [scheduled] or [manual] or [CONTEXT MENU] or [POST CLEANUP] to see clearly what scan was run.
New idea 2: consider showing the contents of the local quarantine on the console per client (so selecting the client and with a new action menu item let us see the quarantine contents of that endpoint and have a chance to create a good/bad override by clicking on the quarantined file).
New idea 3: condider showing the MD5 of the quaratined file in the quarantine view of the WSA client and maybe even create a contect menu that allows you to copy the MD5 of the file to the clipboard - just as you can copy the filename today.
Thank you for your examination and consideration!
Thank you Gyozo for the detailed report. I will file a defect. Thanks :)
Did two more scans eventually show up in the console on this endpoint, or are two scans missing completely? I count 9 scans in the logs but only 7 within that timeframe in the console. What is the polling interval set at?
Did two more scans eventually show up in the console on this endpoint, or are two scans missing completely? I count 9 scans in the logs but only 7 within that timeframe in the console. What is the polling interval set at?
Great work https:///t5/user/viewprofilepage/user-id/3836. Seriously, thanks for bringing this up.
I consider this a critical issue to investigate since I have seen similiar reporting failures in the past.
Next one I see I'll bring up to Webroot support to bolster this.
I consider this a critical issue to investigate since I have seen similiar reporting failures in the past.
Next one I see I'll bring up to Webroot support to bolster this.
Hi JimM,
Thanks for your open eyes! :D
2 scans are comletely missing from the console during this period. FYI, I did wait for the poll-in of the client to make sure I see all scans.
Actually, I just found an option in the console called:
"Save non-executable file details to scan logs"
This defaults to "Off". I suggest you change the default to On as this migth have been the reason why quarantining the DAT file was not logged on the local text log. I believe every action must be logged especially if that is a threat found and quaratined. Of course, every threat related event also must be logged to the console.
I do agree that even blocked threats must be logged. Are they?
Thanks for your open eyes! :D
2 scans are comletely missing from the console during this period. FYI, I did wait for the poll-in of the client to make sure I see all scans.
Actually, I just found an option in the console called:
"Save non-executable file details to scan logs"
This defaults to "Off". I suggest you change the default to On as this migth have been the reason why quarantining the DAT file was not logged on the local text log. I believe every action must be logged especially if that is a threat found and quaratined. Of course, every threat related event also must be logged to the console.
I do agree that even blocked threats must be logged. Are they?
As it stands, only threats detected during a scan are reported up to the console. However, I agree with the consensus in this topic that they should be, just for reference. I'll bring this up with product management and ask them to take a look at this topic. The more useful info we can provide, the better.
We are trying to reproduce this behavior, and so far we haven't been able to do that. We're going to involve our QA department and have them run some tests. Is this behavior something you see frequently? Specifically, we are interested in scans missing from the console that have verifiably run, according to the local scan log.
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.