Hello,
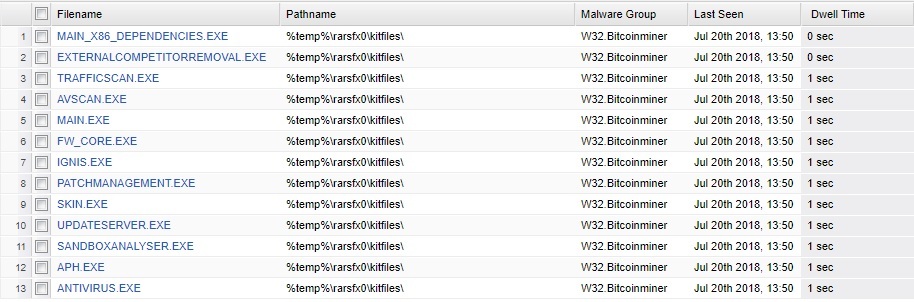
We have an infection currently spreading through our network. New endpoints are popping up on the SecureAnywhere console every few minutes as infected. Some are 'protected', others are 'need attention'. The infection is reported as W32.BitCoinMiner. The file list is shown below.
I need to determine
a. The point of entry - which computer introduced this and how. Was it via the web? local usb device? etc.
b. How the infection is able to spread. So far it has affected two AD sites, spanning two IP subnets. It has not spread to any servers yet.
Does anyone have any tips on how best to understand and investigate the two points above?
Many thanks
Michael.
Page 1 / 1
HI Michael.
Every Miner infection we have seen got installed trough "unclean" software packages so far, but Webroot killed em all. This sometimes happens on customer sites where the "local it guy" wants to install some crappy software on all machines from suspicious sources.
I would start with creating a infection report on the GSM. The first "infected" client will be your point of interest. Who is this user, does this user have rights to install stuff? Check the webfilter reports for this user. Check Spamfilter for suspicious stuff which got delivered or maybe released from the quarantine.
Ask the user (if you are able to track the user) if he has opened "strange" emails. Thats sometimes way easier then look trough all the logs!
And i forgot: If you have something like Autotask AEM you can also make reports on the Client Machine with "changes" - if you find something like "program x got installed" which matches datetime of infection you are getting some useful information.
Oh know i see your Screenshot - did someone roll out a Remote Management Software? These Files look very similiar to Bitdefender / Solarwindsmsp....
Check your webfilter for entrys like: " http://download.bitdefender.com/SMB/Hydra/release/*"
Every Miner infection we have seen got installed trough "unclean" software packages so far, but Webroot killed em all. This sometimes happens on customer sites where the "local it guy" wants to install some crappy software on all machines from suspicious sources.
I would start with creating a infection report on the GSM. The first "infected" client will be your point of interest. Who is this user, does this user have rights to install stuff? Check the webfilter reports for this user. Check Spamfilter for suspicious stuff which got delivered or maybe released from the quarantine.
Ask the user (if you are able to track the user) if he has opened "strange" emails. Thats sometimes way easier then look trough all the logs!
And i forgot: If you have something like Autotask AEM you can also make reports on the Client Machine with "changes" - if you find something like "program x got installed" which matches datetime of infection you are getting some useful information.
Oh know i see your Screenshot - did someone roll out a Remote Management Software? These Files look very similiar to Bitdefender / Solarwindsmsp....
Check your webfilter for entrys like: " http://download.bitdefender.com/SMB/Hydra/release/*"
Hi and Thanks.
When looking at 'reports' in the SecureAnywhere console, I don't see an infection report. Can you be more specific in where to find this?
I have identified the first infected endpoint, based on the date and time in 'last threat' column. However, again, I don't see a webfilter report available. Nor spamfilter.
Perhaps you are referring to a different product??
When looking at 'reports' in the SecureAnywhere console, I don't see an infection report. Can you be more specific in where to find this?
I have identified the first infected endpoint, based on the date and time in 'last threat' column. However, again, I don't see a webfilter report available. Nor spamfilter.
Perhaps you are referring to a different product??
HI Michael.
To get all machines with found infections:
GO to Customer Site-> Endpoint Protection->Reports->Typ: "Found Infections"->Send.
My suggestion was to check your other security products like (firewall, spamfilter etc.).
I'm afraid in GSM you will not be able to find the real source of infection. I dont think there is a report or menu like "user x download software y from site xyz".
And sorry, maybe some spelling is wrong, we use german console so the english names are maybe not 100% accurate 🙂
To get all machines with found infections:
GO to Customer Site-> Endpoint Protection->Reports->Typ: "Found Infections"->Send.
My suggestion was to check your other security products like (firewall, spamfilter etc.).
I'm afraid in GSM you will not be able to find the real source of infection. I dont think there is a report or menu like "user x download software y from site xyz".
And sorry, maybe some spelling is wrong, we use german console so the english names are maybe not 100% accurate 🙂
Thanks all for the comments.
After further investigation, I can reveal this was a false-positive "alarm". Our MSP had decided to deploy Bitdefender to all endpoints on Friday afternoon, despite not notifying or warning of this. Most of the endpoints quarantined the deployment attempt and falsly categorised as bitcoin mining (see screenshot above - all those exe's belong to the Bitdefender installation package).
The reason why our servers never got "touched" was because the deployment script for bitdefender on servers was changed to uninstall competing AV solutions first, hence why none of them reported infection. The same reason why Meraki never flagged any infected files coming through the firewall. This also explained why the first infected machine appeared so clean and innocent - there had been no unauthorised software installs or dodgy web browsing.
I then called the MSP to confirm they had pushed Bitdefender out - which they did. Needless to say I have expressed my *&"£$* unhappiness at this.
After further investigation, I can reveal this was a false-positive "alarm". Our MSP had decided to deploy Bitdefender to all endpoints on Friday afternoon, despite not notifying or warning of this. Most of the endpoints quarantined the deployment attempt and falsly categorised as bitcoin mining (see screenshot above - all those exe's belong to the Bitdefender installation package).
The reason why our servers never got "touched" was because the deployment script for bitdefender on servers was changed to uninstall competing AV solutions first, hence why none of them reported infection. The same reason why Meraki never flagged any infected files coming through the firewall. This also explained why the first infected machine appeared so clean and innocent - there had been no unauthorised software installs or dodgy web browsing.
I then called the MSP to confirm they had pushed Bitdefender out - which they did. Needless to say I have expressed my *&"£$* unhappiness at this.
Hey @ ,
Saw your comment on SpiceWorks as well and I'm thankful that this didn't do any more harm to you.
Be sure to come back here if anything should come up in the future or if you want to meet some other great Webroot enthusiasts!
All the best,
Drew
Saw your comment on SpiceWorks as well and I'm thankful that this didn't do any more harm to you.
Be sure to come back here if anything should come up in the future or if you want to meet some other great Webroot enthusiasts!
All the best,
Drew
Yes, it is the way, how a virus or any kind of malware attack the computer. So be careful about the Internet surfing so that you can not visit any mal website and install an antivirus that will block such suspicious websites to be open on the computer. Visit kaspersky customer support to get all the possible ways a virus can infect the system and take precautions.
That link doesn't take you to any helpful content@ wrote:
Visit kaspersky customer support to get all the possible ways a virus can infect the system and take precautions.
these type of infections spread through networks.before connecting the network we must sure about the security. your information is really very helpful. keep sharing this type of ideas.
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.