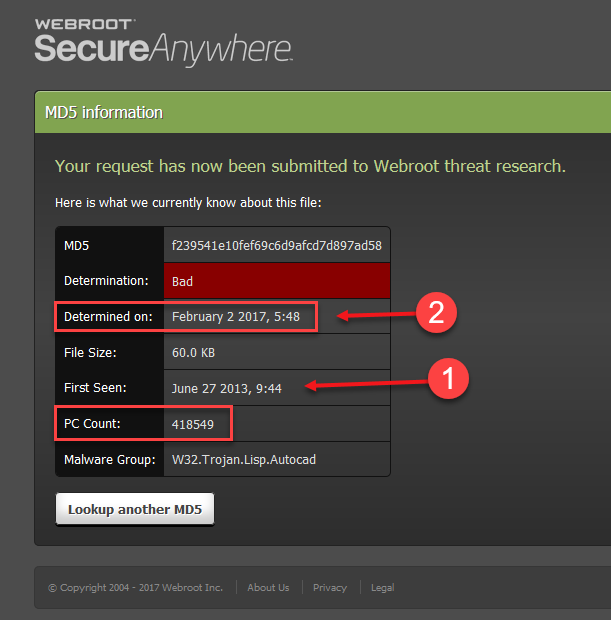
My alerts and any details I have been able to find in the console all refer to paths with variables that are not resolvable.
Is it possible to get the full actual path of malware rather than it showing with variables like %appdata%???
The problem is I do not know which user so I cannot determine the path and more importantly who.
This is an example of the issue. Who's appdata?
Threat List:
APPLICATION-C2A064D9174E0B78AFDA[1].JS, W32.Trojan.Lisp.Autocad, %appdata%microsoftwindowsinetcachelowie4lldmwe4, http://snup.webrootcloudav.com/SkyStoreFileUploader/upload.aspx?MD5=F239541E10FEF69C6D9AFCD7D897AD58 F239541E10FEF69C6D9AFCD7D897AD58,
Page 1 / 1
I will ping one of Webroot's Threat Researchers @ so he can help you on this detection. He should be online in a hour or 2.
Thanks,
Daniel ;)
Thanks,
Daniel ;)
Thanks Daniel,
I do not need more info on the malware itself, I need to know the location of where it was on the users system and which user acquired it.
I do not need more info on the malware itself, I need to know the location of where it was on the users system and which user acquired it.
Appdata is a Hidden area! I believe if you clear your Browsers cache it will be gone!
%appdata%microsoftwindowsinetcachelowie4lldmwe4,
%appdata%microsoftwindowsinetcachelowie4lldmwe4,
No, these variables are showing up in the alert emails I get from WebRoot and in the WebRoot console.
Here is another example. Who's desktop? This was on a remote desktop server with 100 users. Who's desktop?
Threat List:
SQLI DUMPER.EXE, W32.Riskware.Sqlidumper, %desktop%sqli 8.2, http://snup.webrootcloudav.com/SkyStoreFileUploader/upload.aspx?MD5=6491B686C6C1DD7775C661107BA60A0C 6491B686C6C1DD7775C661107BA60A0C,
Here is another example. Who's desktop? This was on a remote desktop server with 100 users. Who's desktop?
Threat List:
SQLI DUMPER.EXE, W32.Riskware.Sqlidumper, %desktop%sqli 8.2, http://snup.webrootcloudav.com/SkyStoreFileUploader/upload.aspx?MD5=6491B686C6C1DD7775C661107BA60A0C 6491B686C6C1DD7775C661107BA60A0C,
Are you using the Business version? If so I will have someone move this over to that section: https://community.webroot.com/t5/Business/ct-p/ent0 also for the best info Please Submit a Business Support Ticket and they will help you!
Thanks,
Daniel 😉
Thanks,
Daniel 😉
MSP version actually. Did not figure they worked that much differently.
Yes the MSP Online Console is very different than the Consumers Console so it's best to chat with a Business rep and they will help you get it sorted. @ @
Thanks.
@ wrote:
My alerts and any details I have been able to find in the console all refer to paths with variables that are not resolvable.
Is it possible to get the full actual path of malware rather than it showing with variables like %appdata%???
The problem is I do not know which user so I cannot determine the path and more importantly who.
This is an example of the issue. Who's appdata?
Threat List:
APPLICATION-C2A064D9174E0B78AFDA[1].JS, W32.Trojan.Lisp.Autocad, %appdata%microsoftwindowsinetcachelowie4lldmwe4, http://snup.webrootcloudav.com/SkyStoreFileUploader/upload.aspx?MD5=F239541E10FEF69C6D9AFCD7D897AD58 F239541E10FEF69C6D9AFCD7D897AD58,
Hello,
The path displayed in the console is a normalized path variable. The full path will be in the log files on endpoint that the detection occured on.
Thanks,
-Dan
It would be nice to not have to go log into the remote endpoint to get this info. I see no reason to "normalize" or from my point obsure the path.
There is already a Feature Request to show the full path in the console. You may want to comment in that thread.@ wrote:
It would be nice to not have to go log into the remote endpoint to get this info. I see no reason to "normalize" or from my point obsure the path.
-Dan
Thanks, I have added my Kudos. This is the first issue I have had with WR that has bothered me. That is a pretty good track record.
The referenced feature request was flagged as completed. Does anyone know if it actually was completed?
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.