We recently experienced that webroot blocked a good file as a threath, even if it was placed in a folder where we have a path override. Tested with Eicar that the override works, so why did it block the file.
Anyone else experienced this? Any solution?
Page 1 / 1
Welcome to Webroot. This happens all the time. No solution. At several of our clients, at least once a month we need to reinstall certain applications that WR keeps insisting is a threat. Despite our efforts to prevent this. We eventually moved these clients to another program.
Sometimes WR randomly eats stuff. That is why it is good, if you can't use your computer you won't get an infection.
Sometimes WR randomly eats stuff. That is why it is good, if you can't use your computer you won't get an infection.
Thanks for bringing it to our attention, @ !
Please reach out to our Support Team so they can take a closer look at what's going on.
Open a Support Ticket
Business Technical Support: Call 1-866-254-8400 M-F 7:00 AM – 6:00 PM MT
Please reach out to our Support Team so they can take a closer look at what's going on.
Open a Support Ticket
Business Technical Support: Call 1-866-254-8400 M-F 7:00 AM – 6:00 PM MT
Hi,
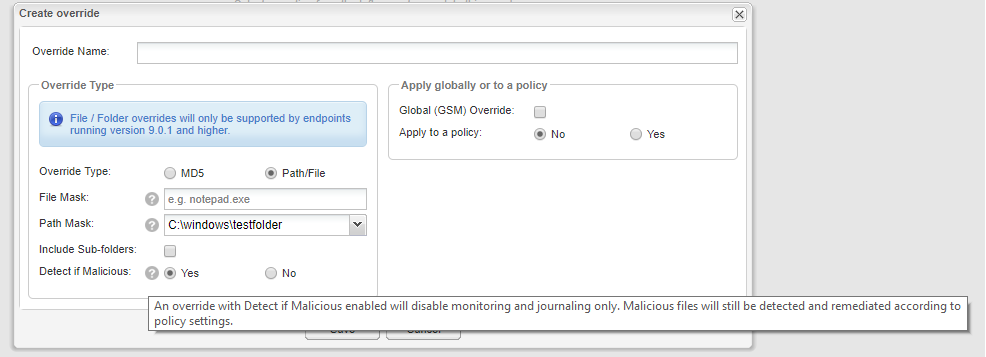
As a sanity check, did you have 'Detect if Malicious' marked as Yes?
If so, files marked as malicious in our Threat Intelligence by us will be blocked, regardless of the scope of the override.
Regards,
Paul
As a sanity check, did you have 'Detect if Malicious' marked as Yes?
If so, files marked as malicious in our Threat Intelligence by us will be blocked, regardless of the scope of the override.
Regards,
Paul
WR_Paul
With no disrespect intended, the longer I've thought about this, the more curious I am --If this is an override, which we all assume to be to prevent false positives, why is there a "detect if malicious" option? I'd be great if "Detect if malicious" reported what it thought was suspicious action in an override folder and submitted to Webroot for analysis, but took no other action, allowing inspection by an administrator and the choice to act, but as it takes action, it seems counter-intuitive to the idea of an override itself.
Why would one create an override, only to have Webroot detect the issue and not obey the override? Thanks for any answers here, I've just found the way this action works to be for lack of a better word, incorrect, ever since I first saw it.
With no disrespect intended, the longer I've thought about this, the more curious I am --If this is an override, which we all assume to be to prevent false positives, why is there a "detect if malicious" option? I'd be great if "Detect if malicious" reported what it thought was suspicious action in an override folder and submitted to Webroot for analysis, but took no other action, allowing inspection by an administrator and the choice to act, but as it takes action, it seems counter-intuitive to the idea of an override itself.
Why would one create an override, only to have Webroot detect the issue and not obey the override? Thanks for any answers here, I've just found the way this action works to be for lack of a better word, incorrect, ever since I first saw it.
Great question, DTMT.
When using this specific override functionality, there are two key use cases which we've seen our customers wish to cover, keeping in mind the three conditions we classify files under - Good, Bad, Unknown:
Use Case 1 - Prevent FP's on files that Webroot believe are 'Bad', but our customers deem as non malicious - 'Good'
Use Case 2 - Prevent journalling/monitoring of 'Unknown' files to prevent potential conflicts - a good example is what Citrix recommends their customers do - Citrix Recommended AV exclusions
Under the second use case, the admin may wish to prevent the monitoring of files within an entire folder, but if malware were to be dropped in the folder Webroot would classify it as malicious and deal with it appropriately. Hence why we have the 'Detect if Malicious' option.
If you have any further questions or suggestions, please don't hesitate to reach out as we can pass these onto the Product Teams.
Regards,
Paul
When using this specific override functionality, there are two key use cases which we've seen our customers wish to cover, keeping in mind the three conditions we classify files under - Good, Bad, Unknown:
Use Case 1 - Prevent FP's on files that Webroot believe are 'Bad', but our customers deem as non malicious - 'Good'
Use Case 2 - Prevent journalling/monitoring of 'Unknown' files to prevent potential conflicts - a good example is what Citrix recommends their customers do - Citrix Recommended AV exclusions
Under the second use case, the admin may wish to prevent the monitoring of files within an entire folder, but if malware were to be dropped in the folder Webroot would classify it as malicious and deal with it appropriately. Hence why we have the 'Detect if Malicious' option.
If you have any further questions or suggestions, please don't hesitate to reach out as we can pass these onto the Product Teams.
Regards,
Paul
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.