Hi Webroot community!
I have a few questions about Webroot forensics.
Background
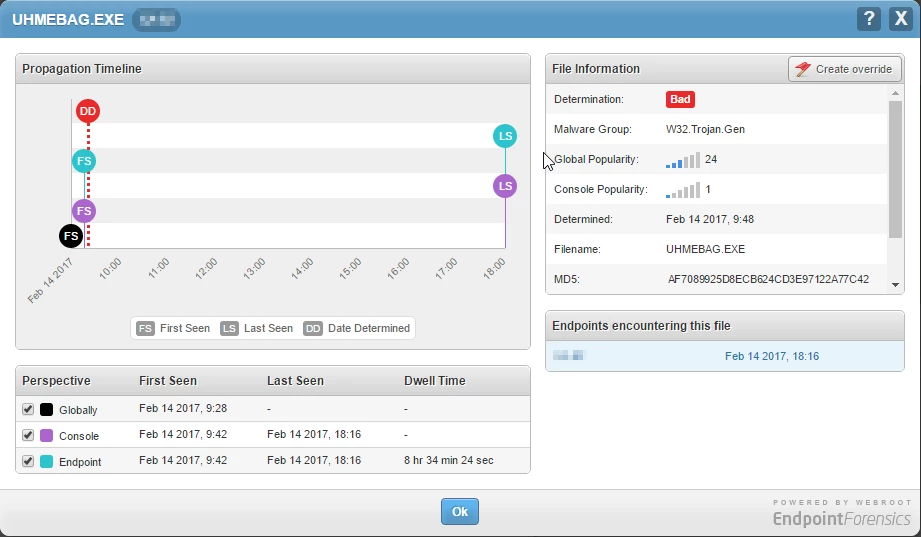
User clicks URL in phising e-mail and manually downloads and runs payload from the resulting landing page. First seen (endpoint) 09:42. A minute, or so, after initialization it had run it's course and encrypted about 10GB worth of data across 3 different servers. The server where the webroot client is installed only had a few hundred megs encrypted - the users profile folder and foxit reader install directory. Most of the files being encrypted was a fileserver and an application server (servers without webroot).
At 09:48 the process is determined bad (DD).
What is expected behaviour after DD? Remediation/rollback? Does the client only report back to the webroot network at set poll interval or does it treat threats differently? How long should I wait for webroot to do it's thing? Is there a way for me to observe webroot remediation in real time (not indirect methods like I/O activity etc.).?
Now, I should mention that I started manually deleting all encrypted files at 10:15 ish and restoring them from backup. Webroot might actually have started remediation without me knowing it and I just missed it?
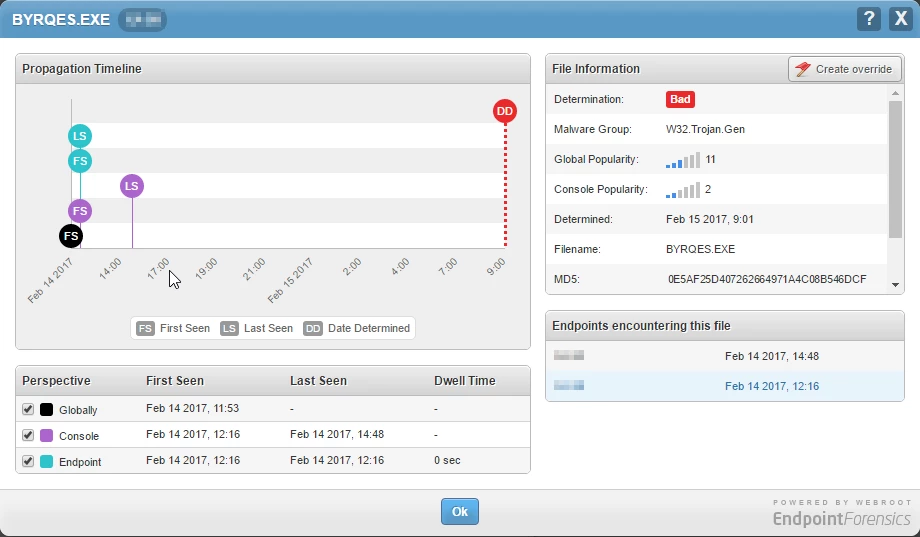
The next day Webroot stopped Cryptolocker from doing harm again. This time different servers involved but the delivery method was basically the same as the day before.
Logically, at least in my head, remediation shouldn't happen until after dd but this last forensic report disproves that.
Any clear thoughts on how the forensic report should be read would be appreciated.
Regards
Ronny
Be the first to reply!
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.