Hi Guys
I find a on polish website SpyShelter simulation for testing for example keyloggers:
link for this testing software - http://www.spyshelter.com/download/AntiTest.zip
It's rather strange that WR automatically add this app to "allow processes" under "system control"
and let this software to capture all traffic on the my keyboard.
Please let me know what you think about this guys and why this is trust app?
Page 1 / 1
Hi Sebastian_ITPS
Sebastian_ITPS wrote:
"Please let me know what you think about this guys and why this is trust app?"
Sebastian_ITPS wrote:
"Please let me know what you think about this guys and why this is trust app?"
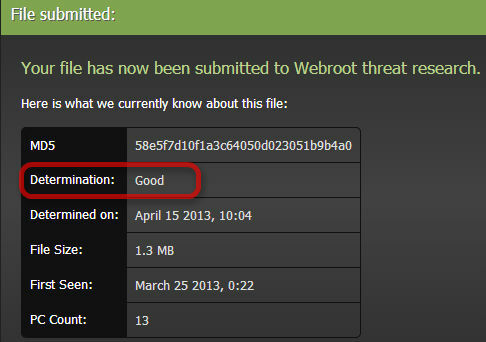
And why this file is a good one?
I know that this so called test didn't create any additional file and didn't try send this logs outside but still.
I know that this so called test didn't create any additional file and didn't try send this logs outside but still.
"And why this file is a good one?"
This file is not a threat.
In any case, you can set the option "monitor" or "block" via WSA
The testing tools are not simulating malware accurately.
JoeJ VP Endpoint Solutions Engineering :
"In any event, screen grabbers and keyloggers are almost irrelevant these days when it comes to real malware. Threats are using much more advanced techniques which is what WSA focuses on protecting: man in the browser attacks, memory injection, system call hooking, and a myriad of other approaches. They tend to not use the obvious ones like screen capture/keylogging because they generate too much data and are too easy to detect as malicious behaviors. WSA excels at blocking the most advanced techniques and has been doing so for years without any threats bypassing it."
This file is not a threat.
In any case, you can set the option "monitor" or "block" via WSA
The testing tools are not simulating malware accurately.
JoeJ VP Endpoint Solutions Engineering :
"In any event, screen grabbers and keyloggers are almost irrelevant these days when it comes to real malware. Threats are using much more advanced techniques which is what WSA focuses on protecting: man in the browser attacks, memory injection, system call hooking, and a myriad of other approaches. They tend to not use the obvious ones like screen capture/keylogging because they generate too much data and are too easy to detect as malicious behaviors. WSA excels at blocking the most advanced techniques and has been doing so for years without any threats bypassing it."
Thank you for the answer.
Thank Sebastian
Happy to help
Best regard, Petr.
Happy to help
Best regard, Petr.
I hope for sanity sake this program works. Since I went wi-fi I have keylogger issues I fight every keystroke I type. Techs think there is nothing wrong. Let them remote service and they tell me it is fixed. I go to login to an account and away we go - characters flying into wrong places, having to reset passwords due to lock out security. Even typing this message I have had to deal with my keystrokes flipping around. So, I downloaded SpyShelter. Do you recommend WSA as well? They, Webroot, installed touchfreeze. I use laptop, Toshiba, and they insult my intelligence telling me I have caps lock on or that my hand is htting my mouse. Not the case. HELP!!! Many thanks to any advice/guidance the community can provide.
Given the recent bank hacking with loss estimates of hundreds of million dollars up to 2 billion, I think the statement "In any event, screen grabbers and keyloggers are almost irrelevant these days when it comes to real malware. Threats are using much more advanced techniques which is what WSA focuses on protecting: man in the browser attacks, memory injection, system call hooking, and a myriad of other approaches. [...........] needs reconsiddring.
What I read about that hack is that they used a vulnerability of unpatched version of MS Word, but also inserted key loggers and transmitted screen grabs about every 2 seconds.
B.t.w. I get no warning from WR when running key_sim from Zamana, that test just collects all keys I type and even macro generated inputs. The test does not collect Password inputs generated by LastPass.
What does happen though, is that after a boot I cannot run that test again. I wonder whether that somewhat late blocking is done by WR. The message I get is something like windows cannot find the path or you may not have access. Renaming the directory containg that test exe, enables running it again.
What I read about that hack is that they used a vulnerability of unpatched version of MS Word, but also inserted key loggers and transmitted screen grabs about every 2 seconds.
B.t.w. I get no warning from WR when running key_sim from Zamana, that test just collects all keys I type and even macro generated inputs. The test does not collect Password inputs generated by LastPass.
What does happen though, is that after a boot I cannot run that test again. I wonder whether that somewhat late blocking is done by WR. The message I get is something like windows cannot find the path or you may not have access. Renaming the directory containg that test exe, enables running it again.
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.