Just a heads up, my business email account suspiciously sent out numerous emails yesterday morning to clients with a Word doc attachment. The attachment contained the above mentioned trojan which also goes by:
W97M.POWLOAD.NSFGAICR, or
W97M.Downloader
Specific details here:
https://www.trendmicro.com/vinfo/au/threat-encyclopedia/malware/trojan.w97m.powload.nsfgaicr
Webroot did not catch this on my system during numerous system scans on multiple devices. I had to reinstall my OS for other reasons (the wonders of Bootcamp), so subsequent scans with Webroot, Trend Micro and Windows Defender are clean. But by then the damage was done. The source was Russia, and by then they had the email password and access to my account, which means they knew who I'd been recently communicating with.
Malicious emails were sent to people I'd had recent conversations with, some of who were expecting documentation from me, so they assumed the attachment was safe and opened it which then infected their system. Many of these contacts were not in my address book, and the malware was clever enough to simply mask the phony email as a "reply" to the most recent legitimate email in each thread. The client system (Trend Micro) identified the trojan, and I was notified by them, but it was too late.
I don't know if the Webroot trojan database is not up to date, or whether Trend Micro is simply more capable of catching this. Just pointing this out and hoping it doesn't happen to anyone else. What a mess.
Page 1 / 2
Can you get us an MD5 Hash? https://www.webroot.com/blog/2015/12/02/whats-in-a-name/
Sorry, no. I have no idea how any of that works. I'm just a guy who's computer sent out a whackload of emails with a word doc attached that when opened said it was made with Office online and the user needed to click a button to run the VBA script. Because my clients were expecting a report from me, they thought it was legitimate.
Very true and as you said some well known AV's missed it but we can't tell you anything about the file unless you still have WSA installed? If so Submit a Support Ticket and they can look into it for you and let you know!
Thanks,
Thanks,
I still have WSA installed on all my devices, but the file that was emailed out was never on my computer in that form. The email my clients received contained a word doc named simply [my last name].doc.
Presumably, I must have received the Trojan in a similar way days, weeks or months prior. So likely some other similarly purposed malware was on my system and avoided detection from WSA and Windows Defender at the time. I reinstalled Bootcamp about a week ago for completely unrelated reasons, and by reformatting that partition I would have wiped any sign of it. But the virus had already scraped my email credentials, and just the other day it sent out the malware attachment.
Do you suppose it's any use to have one of my contacts forward the bugged email to WSA support? I don't have the email or attachment myself since it wasn't generated from my computer. Not sure how to coordinate that.
Presumably, I must have received the Trojan in a similar way days, weeks or months prior. So likely some other similarly purposed malware was on my system and avoided detection from WSA and Windows Defender at the time. I reinstalled Bootcamp about a week ago for completely unrelated reasons, and by reformatting that partition I would have wiped any sign of it. But the virus had already scraped my email credentials, and just the other day it sent out the malware attachment.
Do you suppose it's any use to have one of my contacts forward the bugged email to WSA support? I don't have the email or attachment myself since it wasn't generated from my computer. Not sure how to coordinate that.
No, only from you and it's hard to say where and how as we can only do so much on the Community so a Support Ticket is always the best way.@ wrote:
I still have WSA installed on all my devices, but the file that was emailed out was never on my computer in that form. The email my clients received contained a word doc named simply [my last name].doc.
Presumably, I must have received the Trojan in a similar way days, weeks or months prior. So likely some other similarly purposed malware was on my system and avoided detection from WSA and Windows Defender at the time. I reinstalled Bootcamp about a week ago for completely unrelated reasons, and by reformatting that partition I would have wiped any sign of it. But the virus had already scraped my email credentials, and just the other day it sent out the malware attachment.
Do you suppose it's any use to have one of my contacts forward the bugged email to WSA support? I don't have the email or attachment myself since it wasn't generated from my computer. Not sure how to coordinate that.
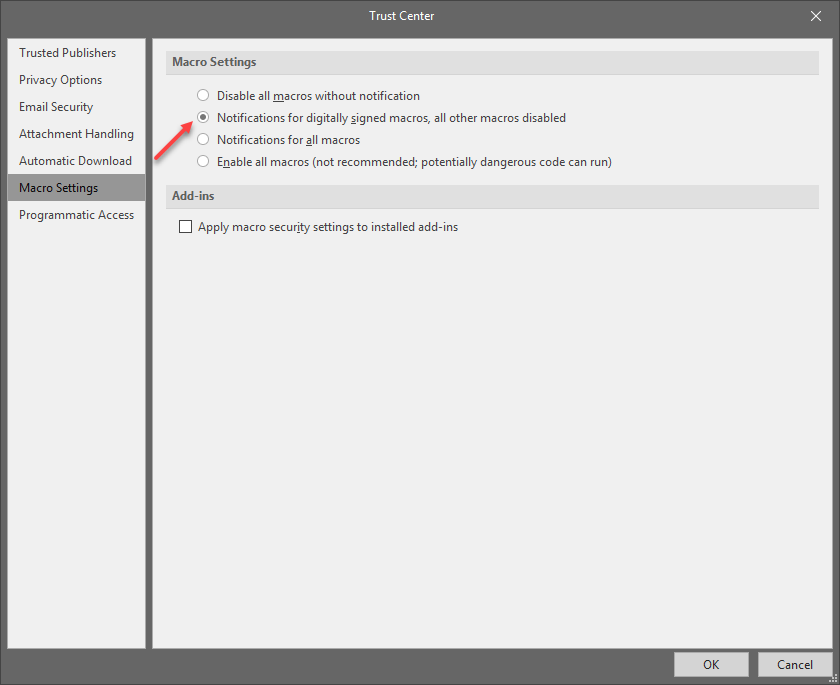
It could of downloaded a payload when the users open the said Word Doc. WSA doesn't scan word doc's as they are harmless but if Macro's are enabled then it could download the payload then WSA would detect the payload. https://support.office.com/en-us/article/enable-or-disable-macros-in-office-files-12b036fd-d140-4e74-b45e-16fed1a7e5c6
Personally I have Macro's disabled in all Office Programs!
What is a macro, who makes them, and what is the security risk?
Macros automate frequently used tasks to save time on keystrokes and mouse actions. Many were created by using Visual Basic for Applications (VBA) and are written by software developers. However, some macros can pose a potential security risk. A person with malicious intent, also known as a hacker, can introduce a destructive macro in a file that can spread a virus on your computer or into your organization's network.
Really sorry to hear about this. Please, if you can @ , keep us posted regarding your exchanges with Support.
It would be interesting to know how this happened, why this happened and what Webroot did to rectify the situation.
Thanks!
It would be interesting to know how this happened, why this happened and what Webroot did to rectify the situation.
Thanks!
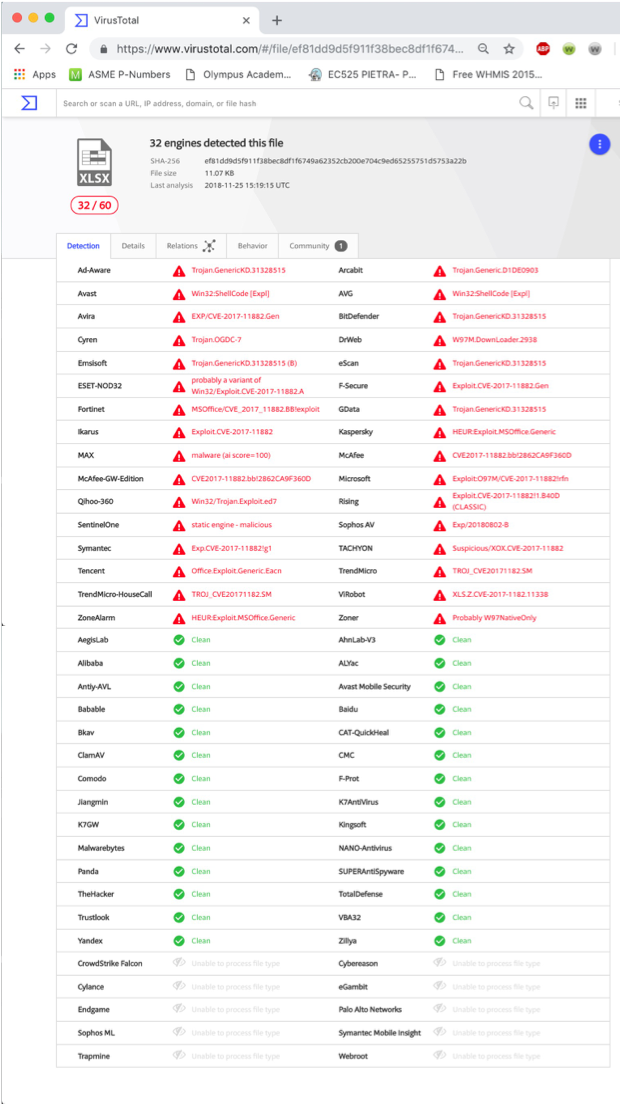
A computer genius friend of mine determined this:
MD5 hash: 9e00d9d69c5ece6e4949be92b0568e40
Performance of various software in detecting it. Note Webroot at bottom, unable to detect...
Ad-Aware, VB.EmoDldr.14.Gen
Arcabit, HEUR.VBA.Trojan.e
BitDefender, VB.EmoDldr.14.Gen
CAT-QuickHeal, W97M.Emotet.Heur
DrWeb, W97M.DownLoader.3178
Emsisoft, VB.EmoDldr.14.Gen (B)
Endgame, malicious (high confidence)
eScan, VB.EmoDldr.14.Gen
ESET-NOD32, VBA/TrojanDownloader.Agent.LVO
F-Secure, VB.EmoDldr.14.Gen
Fortinet, VBA/Agent.LTL!tr.dldr
GData, Macro.Trojan-Downloader.Shallow.S
Ikarus, Trojan.VBA.Agent
Kaspersky, HEUR:Trojan-Downloader.MSOffice.SLoad.gen
MAX, malware (ai score=87)
McAfee, W97M/Downloader!9E00D9D69C5E
McAfee-GW-Edition, BehavesLike.Downloader.ml
Microsoft, Trojan:O97M/Sonbokli.A!cl
NANO-Antivirus, Trojan.Ole2.Vbs-heuristic.druvzi
Qihoo-360, virus.office.qexvmc.1080
Rising, Macro.Agent.dx (CLASSIC)
SentinelOne, static engine - malicious
Symantec, ISB.Downloader!gen186
TACHYON, Suspicious/W97M.Obfus.Gen.6
Tencent, Heur.Macro.Generic.Gen.h
TrendMicro, Trojan.W97M.POWLOAD.AB
TrendMicro-HouseCall, Trojan.W97M.POWLOAD.AB
ZoneAlarm, HEUR:Trojan-Downloader.MSOffice.SLoad.gen
Zoner, Probably W97Obfuscated
AegisLab, Clean
AhnLab-V3, Clean
ALYac, Clean
Antiy-AVL, Clean
Avast, Clean
Avast Mobile Security, Clean
AVG, Clean
Avira, Clean
Babable, Clean
Baidu, Clean
Bkav, Clean
ClamAV, Clean
CMC, Clean
Comodo, Clean
Cyren, Clean
F-Prot, Clean
Jiangmin, Clean
K7AntiVirus, Clean
K7GW, Clean
Kingsoft, Clean
Malwarebytes, Clean
Panda, Clean
Sophos AV, Clean
SUPERAntiSpyware, Clean
TheHacker, Clean
VBA32, Clean Yandex, Clean
Zillya, Clean
Alibaba, Unable to process file type
CrowdStrike Falcon, Unable to process file type
Cybereason, Unable to process file type
Cylance, Unable to process file type
eGambit, Unable to process file type
Palo Alto Networks, Unable to process file type
Sophos ML, Unable to process file type
Symantec Mobile Insight, Unable to process file type
Trapmine, Unable to process file type
Trustlook, Unable to process file type
Webroot, Unable to process file type
MD5 hash: 9e00d9d69c5ece6e4949be92b0568e40
Performance of various software in detecting it. Note Webroot at bottom, unable to detect...
Ad-Aware, VB.EmoDldr.14.Gen
Arcabit, HEUR.VBA.Trojan.e
BitDefender, VB.EmoDldr.14.Gen
CAT-QuickHeal, W97M.Emotet.Heur
DrWeb, W97M.DownLoader.3178
Emsisoft, VB.EmoDldr.14.Gen (B)
Endgame, malicious (high confidence)
eScan, VB.EmoDldr.14.Gen
ESET-NOD32, VBA/TrojanDownloader.Agent.LVO
F-Secure, VB.EmoDldr.14.Gen
Fortinet, VBA/Agent.LTL!tr.dldr
GData, Macro.Trojan-Downloader.Shallow.S
Ikarus, Trojan.VBA.Agent
Kaspersky, HEUR:Trojan-Downloader.MSOffice.SLoad.gen
MAX, malware (ai score=87)
McAfee, W97M/Downloader!9E00D9D69C5E
McAfee-GW-Edition, BehavesLike.Downloader.ml
Microsoft, Trojan:O97M/Sonbokli.A!cl
NANO-Antivirus, Trojan.Ole2.Vbs-heuristic.druvzi
Qihoo-360, virus.office.qexvmc.1080
Rising, Macro.Agent.dx (CLASSIC)
SentinelOne, static engine - malicious
Symantec, ISB.Downloader!gen186
TACHYON, Suspicious/W97M.Obfus.Gen.6
Tencent, Heur.Macro.Generic.Gen.h
TrendMicro, Trojan.W97M.POWLOAD.AB
TrendMicro-HouseCall, Trojan.W97M.POWLOAD.AB
ZoneAlarm, HEUR:Trojan-Downloader.MSOffice.SLoad.gen
Zoner, Probably W97Obfuscated
AegisLab, Clean
AhnLab-V3, Clean
ALYac, Clean
Antiy-AVL, Clean
Avast, Clean
Avast Mobile Security, Clean
AVG, Clean
Avira, Clean
Babable, Clean
Baidu, Clean
Bkav, Clean
ClamAV, Clean
CMC, Clean
Comodo, Clean
Cyren, Clean
F-Prot, Clean
Jiangmin, Clean
K7AntiVirus, Clean
K7GW, Clean
Kingsoft, Clean
Malwarebytes, Clean
Panda, Clean
Sophos AV, Clean
SUPERAntiSpyware, Clean
TheHacker, Clean
VBA32, Clean Yandex, Clean
Zillya, Clean
Alibaba, Unable to process file type
CrowdStrike Falcon, Unable to process file type
Cybereason, Unable to process file type
Cylance, Unable to process file type
eGambit, Unable to process file type
Palo Alto Networks, Unable to process file type
Sophos ML, Unable to process file type
Symantec Mobile Insight, Unable to process file type
Trapmine, Unable to process file type
Trustlook, Unable to process file type
Webroot, Unable to process file type
Support ticket sent
Was that VirusTotal? If so, do bear in mind this post.@ wrote:
Performance of various software in detecting it. Note Webroot at bottom, unable to detect...
Hi Muddy7,
Not sure if it was VT or not. My buddy ran it last night and I got the email this morning from him, so I just copy pasted from the email.
Not sure if it was VT or not. My buddy ran it last night and I got the email this morning from him, so I just copy pasted from the email.
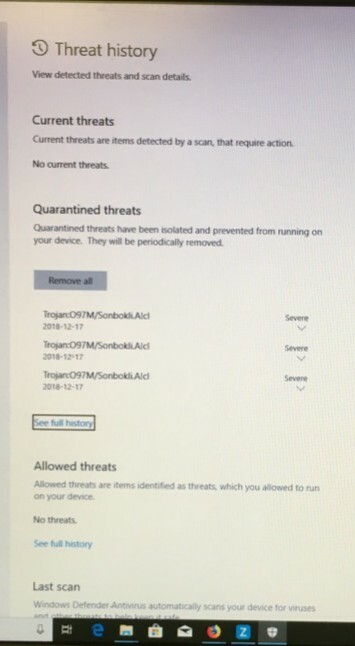
One of my clients caught it with Windows Defender. He did not run the macro in the Word doc. He also runs Webroot which did not pick it up.
As I said WSA doesn't scan Word Doc's or Email clients such as Outlook or Thunderbird only if the file actually ran the Macro then it would detect the payload it tries to download and run on ones system then WSA would stop it.@ wrote:
One of my clients caught it with Windows Defender. He did not run the macro in the Word doc. He also runs Webroot which did not pick it up.
Then that's a problem, because Webroot missed what simple (and free) Windows Defender picked up, as well as Trend Micro.
The only reason that Windows Defender was disabled on my system was that when Webroot (or any 'other' virus protection, I think), the real time shield from Windows defender gets disabled automatically.
The only reason that Windows Defender was disabled on my system was that when Webroot (or any 'other' virus protection, I think), the real time shield from Windows defender gets disabled automatically.
I don't think you are understanding what I'm trying to say, so I will just leave it as is and if you want to know more Contact Webroot Support.@ wrote:
Then that's a problem, because Webroot missed what simple (and free) Windows Defender picked up, as well as Trend Micro.
The only reason that Windows Defender was disabled on my system was that when Webroot (or any 'other' virus protection, I think), the real time shield from Windows defender gets disabled automatically.
Unless I'm misunderstanding what a few of the recipients have told me, my understanding is that those people running Windows Defender were warned (popup, or however windows defender does it) *prior* to them running any macro in the word doc, thus avoiding infection.
Trend Micro identified the trojan immediately after running the macro, thus having to quarantine their computers but avoiding any additional problems.
I believe I was the only one running Webroot, and the trojan/malware/whatever was living in my system, wreaking havoc undetected.
I will continue my back and forth with support and see where it goes. Cheers
Trend Micro identified the trojan immediately after running the macro, thus having to quarantine their computers but avoiding any additional problems.
I believe I was the only one running Webroot, and the trojan/malware/whatever was living in my system, wreaking havoc undetected.
I will continue my back and forth with support and see where it goes. Cheers
Let's put it another way.
Had you run the macro, Webroot would have behaved the same way as TrendMicro did (except, imho, it would have blocked the payload not "after" running the macro but instantly)
As TripleHelix says:
All this hopefully Webroot Support will get to the bottom of. As I already said, I very much hope you can keep us posted so we know what happened.
Thanks!
Had you run the macro, Webroot would have behaved the same way as TrendMicro did (except, imho, it would have blocked the payload not "after" running the macro but instantly)
As TripleHelix says:
... only if the file actually ran the Macro then it would detect the payload it tries to download and run on ones system then WSA would stop it.But then the next question is: was the infected Word document ever on your machine? True, something very bad seems to have happened inasmuch as the hackers got hold of the mail addresses of your recent contacts and your communications with them. But did they send that Word document from your machine or did they spoof your email address? Either is possible.
All this hopefully Webroot Support will get to the bottom of. As I already said, I very much hope you can keep us posted so we know what happened.
Thanks!
For sure, I'll keep the thread active and let everyone know what happened.
I agree with your first statement, in that if I did get a similar email from someone else and clicked on the macro, I would have expected whatever VBA code that ran, and infected my system, to get flagged by WSA. But I did not receive (to my recollection) any previous email like that, and certainly nothing I clicked on. I did receive a pdf file from a contact a few months ago that I tried to open but it didn't do anything. I then realized that it was likely spam, ran WSA (which is always running anyways) and nothing came up. Whether that was it or not remains a mystery. Somehow my system obviously got infected by something that remained undetected and cause damage. The only reason my system is clean now is because I had to re-partition my Bootcamp drive and reinstall Windows (audio driver problems, tried to update Bootcamp drivers, install hung, bricked my Windows bootup... just a giant spiral of nonsense that cost me about 5 days trying to get everything back to normal, then this)
I don't think the [lastname].doc file ever existed on my computer. The must have spoofed my email address because my computer was powered down when the emails went out.
Good times.
I agree with your first statement, in that if I did get a similar email from someone else and clicked on the macro, I would have expected whatever VBA code that ran, and infected my system, to get flagged by WSA. But I did not receive (to my recollection) any previous email like that, and certainly nothing I clicked on. I did receive a pdf file from a contact a few months ago that I tried to open but it didn't do anything. I then realized that it was likely spam, ran WSA (which is always running anyways) and nothing came up. Whether that was it or not remains a mystery. Somehow my system obviously got infected by something that remained undetected and cause damage. The only reason my system is clean now is because I had to re-partition my Bootcamp drive and reinstall Windows (audio driver problems, tried to update Bootcamp drivers, install hung, bricked my Windows bootup... just a giant spiral of nonsense that cost me about 5 days trying to get everything back to normal, then this)
I don't think the [lastname].doc file ever existed on my computer. The must have spoofed my email address because my computer was powered down when the emails went out.
Good times.
Thanks! I think I can safely say that we're all interested in what happened.
By the way:
To my mind (and I am far from being an IT expert 😞 — so do correct me, someone else, if I am wrong in my speculations), there are two possibilities.
EITHER:
Your machine was compromised
OR:
Something was compromised somewhere in between your sending your recent mails and their arriving at their destination.
Yet another reason why, if Webroot can still get to the bottom of all this notwithstanding your repartitioning and reinstalling OS, it'll be really interesting to know.
Having said that, I'm really, really sorry that this has cost you 5 days of running around trying to get things back to normal. I can well imagine how exasperated you feel and that Webroot is not exactly the flavour of the month for you at the moment.
By the way:
I'm not even sure of that!@ wrote:
Somehow my system obviously got infected by something that remained undetected and cause damage.
To my mind (and I am far from being an IT expert 😞 — so do correct me, someone else, if I am wrong in my speculations), there are two possibilities.
EITHER:
Your machine was compromised
OR:
Something was compromised somewhere in between your sending your recent mails and their arriving at their destination.
Yet another reason why, if Webroot can still get to the bottom of all this notwithstanding your repartitioning and reinstalling OS, it'll be really interesting to know.
Having said that, I'm really, really sorry that this has cost you 5 days of running around trying to get things back to normal. I can well imagine how exasperated you feel and that Webroot is not exactly the flavour of the month for you at the moment.
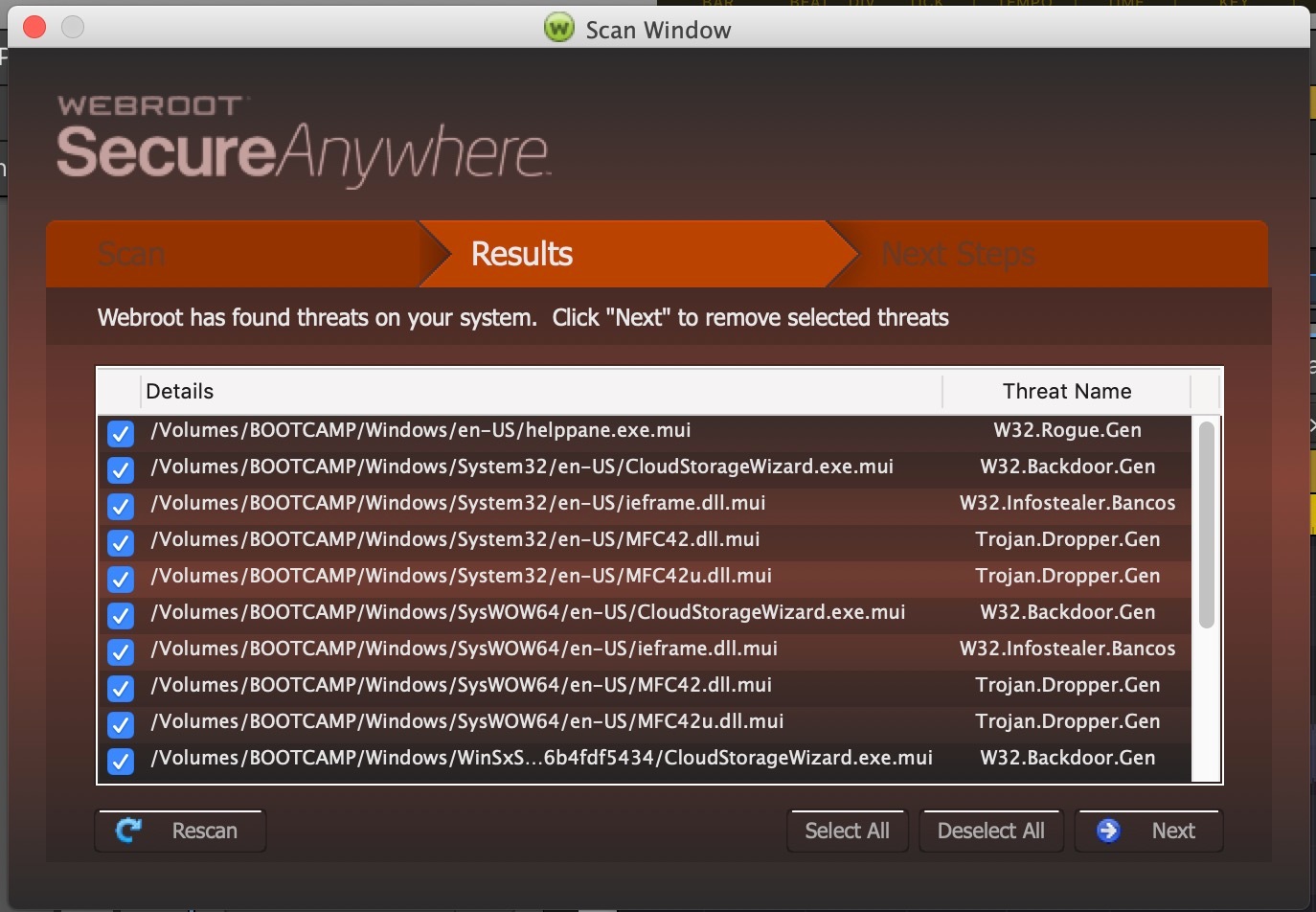
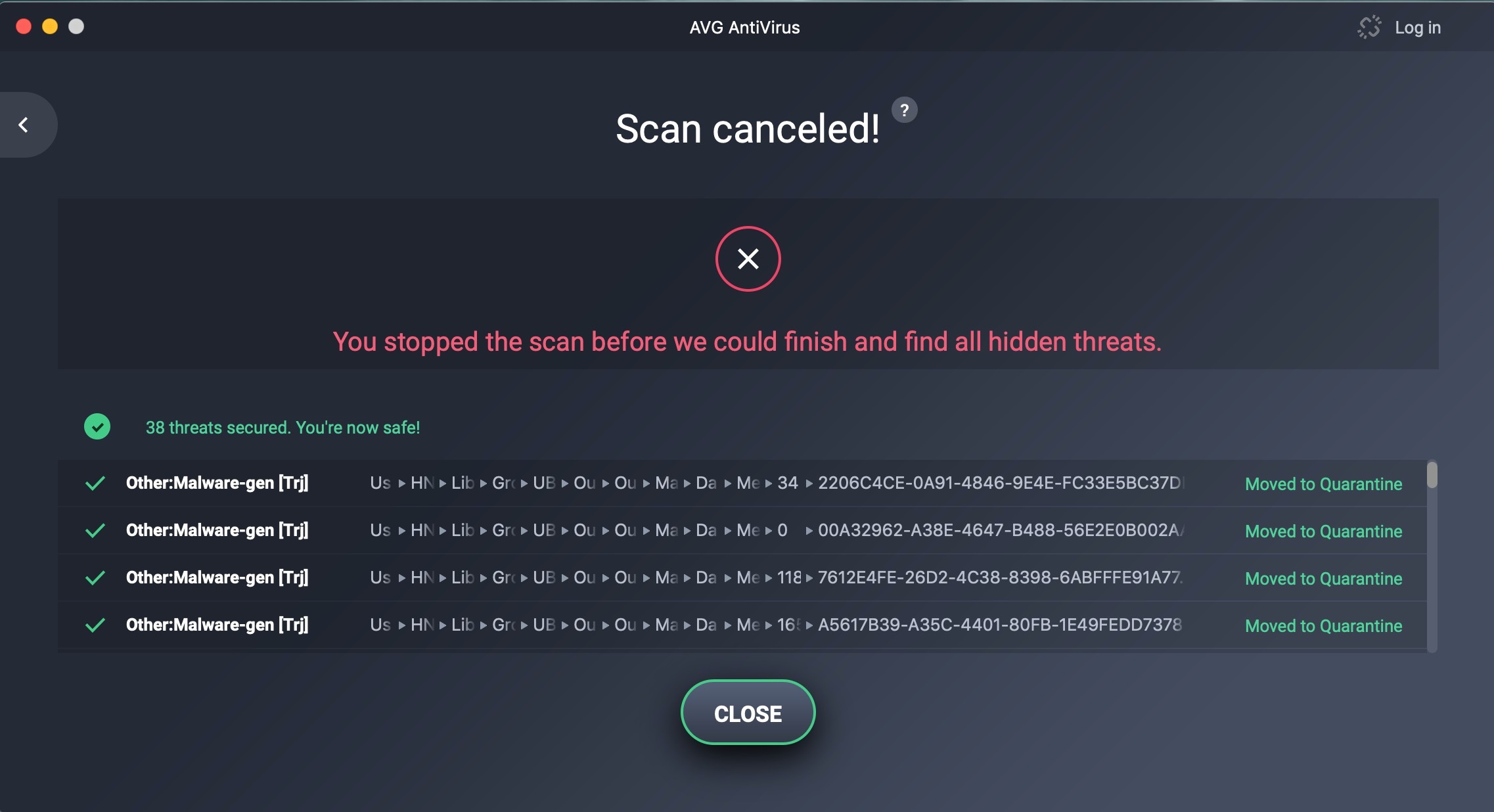
OK, this just happened.... was on my Mac partition and suddently Webroot pops up and says it's found threats on my Bootcamp partition. I hit 'Next', and it says it can't.
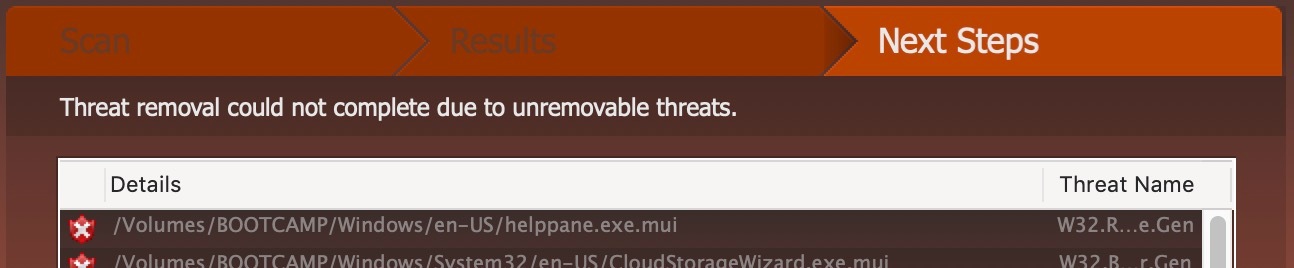
Here is the message that says it can't remove the threats:
Then I installed AVG Free and ran it, which finds a tonne on my Mac partition in my Outlook folder:
Crazy. I'm going to jump to Windows and run AVG. I will then go back to OSX and finish AVG. It was taking forever.
Update: Support just told me "We are not seeing any indication that your computer has been infected after reviewing logs"...
(sigh)
Here is the message that says it can't remove the threats:
Then I installed AVG Free and ran it, which finds a tonne on my Mac partition in my Outlook folder:
Crazy. I'm going to jump to Windows and run AVG. I will then go back to OSX and finish AVG. It was taking forever.
Update: Support just told me "We are not seeing any indication that your computer has been infected after reviewing logs"...
(sigh)
From the pics, looks like an extremely serious infection. But we're only helpers so we unfortunately can do nothing to assist you in disinfecting your computer. I trust you're keeping Support in the loop and have provided them with the same information as you have to us, as they will be able to handle this.
Hello HollowMan,
I see that you are running Windows Boot Camp on a Mac computer. When you put your support ticket in did you specifically tell them that this is a Mac machine that you are having problems with? Also have you set your Microsoft setting like @MacDaddy385 to see if he has any input to this problem.
I see that you are running Windows Boot Camp on a Mac computer. When you put your support ticket in did you specifically tell them that this is a Mac machine that you are having problems with? Also have you set your Microsoft setting like @MacDaddy385 to see if he has any input to this problem.
Hi Dave,
Thanks for the heads up. I double checked the OSX and Windows partitions and both already had the same macro security settings as you suggested.
Support has stated that the AVG results in my Outlook folder are likely false calls. And as of yet there is no explanation for the fact that Webroot run from OSX show infections in the Bootcamp partition, but no threats when run from Windows.
I think what I'll do is get some lighter fluid and start a small, dangerously toxic ritual laptop burning in my backyard. Then I'll head to Staples and buy a looseleaf notebook and some Bic pens. There's no school like the old school, right?
Thanks for the heads up. I double checked the OSX and Windows partitions and both already had the same macro security settings as you suggested.
Support has stated that the AVG results in my Outlook folder are likely false calls. And as of yet there is no explanation for the fact that Webroot run from OSX show infections in the Bootcamp partition, but no threats when run from Windows.
I think what I'll do is get some lighter fluid and start a small, dangerously toxic ritual laptop burning in my backyard. Then I'll head to Staples and buy a looseleaf notebook and some Bic pens. There's no school like the old school, right?
Here is the conclusion, after about 30 messages back and forth with support and a 2-hr remote session this afternoon:
For the morbidly curious, the md5 hash was: f321826851c6c84c8657ef237916b572
I'm forced to move away from Webroot and into something like Bit Defender that will scan email attachments like these. With malware being disguised as emails from known contacts as replies to existing emails, with seemingly legitimate attachments and even including the correct .sig file... it becomes far less simple to separate the good from the bad. Myself as a business owner and probably many others simply don't have the time to call our contacts when they send an attachment and ask them if it's the correct one. The fact that Webroot and some others can't scan these file types is precisely why hackers are using them.
For the record, I don't recall being dumb enough to blindly click on anything anyone ever sends me. I think we're all pretty savvy that way. I have no idea how the initial infection got established, but it's a moot point. The fact is that my company email was used to distribute malware in exactly the same form that Webroot is unable to detect. It may detect the payload once any nefarious code has downloaded the nasty stuff, but at that point it might be too late. Other software packages can identify the attachment as malicious right out of the gate.
Also for the record, support from WSA was excellent.
Thanks everyone for the help. Here's to less malware in 2019!
-P
- All of the threats on the OSX partition were false positives.
- Some of the threats on the Windows partition were legitimate, but undetected by Webroot. WSA does not scan email attachments such as .docx files.
For the morbidly curious, the md5 hash was: f321826851c6c84c8657ef237916b572
I'm forced to move away from Webroot and into something like Bit Defender that will scan email attachments like these. With malware being disguised as emails from known contacts as replies to existing emails, with seemingly legitimate attachments and even including the correct .sig file... it becomes far less simple to separate the good from the bad. Myself as a business owner and probably many others simply don't have the time to call our contacts when they send an attachment and ask them if it's the correct one. The fact that Webroot and some others can't scan these file types is precisely why hackers are using them.
For the record, I don't recall being dumb enough to blindly click on anything anyone ever sends me. I think we're all pretty savvy that way. I have no idea how the initial infection got established, but it's a moot point. The fact is that my company email was used to distribute malware in exactly the same form that Webroot is unable to detect. It may detect the payload once any nefarious code has downloaded the nasty stuff, but at that point it might be too late. Other software packages can identify the attachment as malicious right out of the gate.
Also for the record, support from WSA was excellent.
Thanks everyone for the help. Here's to less malware in 2019!
-P
Thanks, @ , for your very helpful explanation of what happened. Thanks above all for letting us know, as you had promised to do, what transpired 😃.
I just have one query. You say:
The information you gave us was that some of your customers you had recently conversed with were receiving emails from your email address with malicious Word documents (payload delivered through a malicious macro, apparently) attached:
The answer to each of those questions makes a great deal of difference as if the answer to each is the latter, then no compromise actually took place due to Webroot.
As I see it, Webroot's policy of not scanning email attachments (a policy I agree with, for reasons I won't go into in this post) only presents a clear danger when you would forward to another recipient email attachments you have received from a sender without having previously opened them yourself—a pretty improbable scenario, it would seem to me.
Having said that, I can understand why you now feel a bit leery of Webroot, given the experience you have encountered, even though I believe Webroot's policy is sound. So, presuming you have decided to change your AV, I wish you all the best with whatever other solution you opt for 😉
I just have one query. You say:
I'm not convinced that happened. My experience of Webroot SecureAnywhere and its legacy product Prevx (>12 years) gives me some reason to doubt that your email app on your computer is likely to have been compromised.@ wrote:
The fact is that my company email was used to distribute malware in exactly the same form that Webroot is unable to detect.
The information you gave us was that some of your customers you had recently conversed with were receiving emails from your email address with malicious Word documents (payload delivered through a malicious macro, apparently) attached:
My questions at the time were:@ wrote:
Malicious emails were sent to people I'd had recent conversations with, some of who were expecting documentation from me
- Did those emails come from your computer or was your email address spoofed?
- Did the offender get access to your recent email communications with your customers by compromising your machine or did something get compromised somewhere between those communications leaving your machine and their arriving at the recipients' machines?
The answer to each of those questions makes a great deal of difference as if the answer to each is the latter, then no compromise actually took place due to Webroot.
As I see it, Webroot's policy of not scanning email attachments (a policy I agree with, for reasons I won't go into in this post) only presents a clear danger when you would forward to another recipient email attachments you have received from a sender without having previously opened them yourself—a pretty improbable scenario, it would seem to me.
Having said that, I can understand why you now feel a bit leery of Webroot, given the experience you have encountered, even though I believe Webroot's policy is sound. So, presuming you have decided to change your AV, I wish you all the best with whatever other solution you opt for 😉
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.