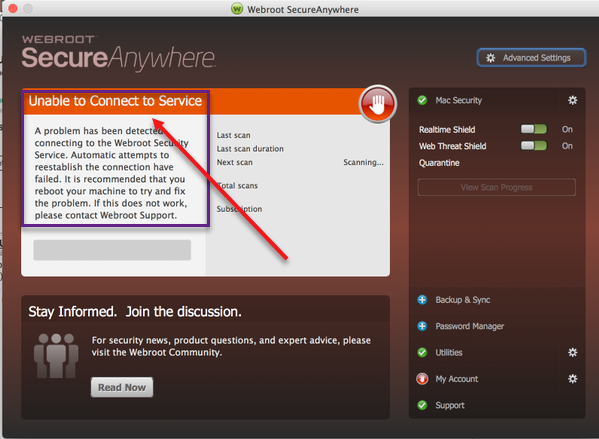
My Webroot settings won't let me click any boxes to put a checkmark and all of the checks I had are gone (all settings are unchecked), I see the red ! on the icon and it seems like there are threats to remove but I can't see any listed in the appropriate area also it won't scan any files. Any ideas? I think my computer has been hacked and I've got a lot of other weird issues as well that wiping and restoring it won't help. I'm using a 2016 Macbook Pro with macOS Sierra 10.12.4 but problems have been going on forever.
Page 1 / 1
Hello chasedaniel, Welcome to the Webroot Community Forum. :D
Sorry you are having problems with WSA. Please try a reboot of the computer. If that does not help please DO NOT UNINSTALL / REINSTALL WSA. That would wipe out the roll back feature if the computer is infected. Please Contact Support and they will sort this problem for you.
Please submit a Support Ticket or Contact Webroot Support to sort this problem. This service is FREE with a Paid Subscription.
Support Ticket System is Open 24/7
HTH,
Dave.;)
Sorry you are having problems with WSA. Please try a reboot of the computer. If that does not help please DO NOT UNINSTALL / REINSTALL WSA. That would wipe out the roll back feature if the computer is infected. Please Contact Support and they will sort this problem for you.
Please submit a Support Ticket or Contact Webroot Support to sort this problem. This service is FREE with a Paid Subscription.
Support Ticket System is Open 24/7
HTH,
Dave.;)
Hi thanks for the info. I do not actually have a paid subscription yet but was thinking of renewing. I previously had a subscription threw best buy but I think that has expired and I am using a trial right now. Do you have any idea what this could be? I'm kind of hesitant to pay for a subscription if I'll be running into this type problem frequently. I tried it once before several months ago and the same thing happened. I've also seen another AV software suite (installed at different a time) thrown in the trash along with other random files.
I'd really like to get a better understanding of what is happening and am happy to pay for a subscription if I could be sure that this massive problem which Apple has been beyond useless to the point where this is my last Mac and I own 4 of right now and $2000000 dollars in other Apple products almost all acting strangely in some way. Lots of fake certificates, keychain requests, webcam turns on random times throughout the day. I used a file recovery software program and it found mostly EFI files that had been deleted not by me and I don't remember any of the updates in the last 2 weeks say firmware update anywhere.
AppleCare seriously thinks I'm making it up and tried to do some fraud investigation which went nowhere and was fairly telling on their part that the only effort they'd put into was trying to blame it all on me. Sorry to rant but I'm not sure what to do. I have these sketchy kext on my computer that move around their address and I'm thinking they are related to everything:
MacBook-Pro:~ kextstat -a -s
Index Refs Address Size Wired Architecture Name (Version) UUID <Linked Against>
5 133 0xffffff7f80a00000 0x3dd0 0x3dd0 ????/???? com.apple.kpi.mach (16.5.0) E18B885B-776C-4F3A-88D4-C823FAFE12A1
3 140 0xffffff7f80a04000 0x21040 0x21040 ????/???? com.apple.kpi.iokit (16.5.0) E2BA46F4-C06A-4ACE-81E5-D9A4B6E061AA
4 146 0xffffff7f80a26000 0xd200 0xd200 ????/???? com.apple.kpi.libkern (16.5.0) 21ABA52A-C45A-4A1B-8824-F6EB5295ADDE
6 65 0xffffff7f80a34000 0xbbf0 0xbbf0 ????/???? com.apple.kpi.private (16.5.0) F0CD0AC2-92DF-4FF9-80A5-21B68641D28E
7 85 0xffffff7f80a40000 0x5890 0x5890 ????/???? com.apple.kpi.unsupported (16.5.0) 4AE97C68-EB51-4545-A2EB-007EE5A66503
1 112 0xffffff7f80a46000 0x9d90 0x9d90 ????/???? com.apple.kpi.bsd (16.5.0) D4161E07-43B8-4D47-ABFE-7DF2D693ED9A
16 16 0xffffff7f80a50000 0x27000 0x27000 x86_64 com.apple.iokit.IOStorageFamily (2.1) F908D7F5-4F54-3B89-8657-57F06350F4DB <7 6 5 4 3 1>
137 0 0xffffff7f80aef000 0x5000 0x5000 x86_64 com.webroot.driver.WebrootSecureAnywhere (23) DEFC5BE2-BCC1-3F62-9F9B-78CF3FDC1ECA <5 4 3 1>
84 3 0xffffff7f80afc000 0x2b000 0x2b000 x86_64 com.apple.iokit.IOSCSIArchitectureModelFamily (394.50.1) 82139727-96EE-3990-B7E3-950D3F9799F5 <6 5 4 3 1>
12 36 0xffffff7f80b3f000 0x35000 0x35000 x86_64 com.apple.iokit.IOPCIFamily (2.9) C6E3195E-A0D7-3B71-B5F4-9EE9E182D4FC <7 6 5 4 3>
8 7 0xffffff7f80e0c000 0xa9000 0xa9000 x86_64 com.apple.kec.corecrypto (1.0) E3701C61-A548-3181-9F3E-C90DF8327185 <7 6 5 4 3 1>
145 2 0xffffff7f80eb5000 0x5000 0x5000 x86_64 com.apple.kext.triggers (1.0) 3EAB29BE-4C7C-3D6C-B20B-B48707426005 <7 6 5 4 3 1>
9 0 0xffffff7f80f22000 0xf000 0xf000 x86_64 com.apple.kec.pthread (1) 4EFF2F70-C9B9-3176-BF83-F1B660C42135 <7 6 5 4 1>
133 0 0xffffff7f80f31000 0xf000 0xf000 x86_64 com.apple.driver.pmtelemetry (1) 963D5479-A74A-35FA-AFAA-6D61989DAD4D <7 6 5 4 3>
146 0 0xffffff7f8103b000 0x9000 0x9000 x86_64 com.apple.filesystems.autofs (3.0) E79E1801-8AB8-3BB1-A1F2-3CA5F9C7C648 <145 7 6 5 4 3 1>
11 36 0xffffff7f810e5000 0x9000 0x9000 x86_64 com.apple.iokit.IOACPIFamily (1.4) 4F7FB6AD-2498-3F71-827C-ED7AA4BF2511 <7 6 4 3>
18 1 0xffffff7f810ee000 0xd000 0xd000 x86_64 com.apple.driver.AppleBusPowerController (1.0) DB526B45-1A45-3A81-A0C1-57F826CADEDF <11 5 4 3>
19 18 0xffffff7f810fb000 0x69000 0x69000 x86_64 com.apple.iokit.IOUSBHostFamily (1.1) 96FD82D0-CFF5-3EDE-971A-456CB10DBEBF <18 7 6 5 4 3 1>
39 2 0xffffff7f8116c000 0x9a000 0x9a000 x86_64 com.apple.iokit.IOUSBFamily (900.4.1) 616CA05C-34A4-393E-8A17-93C7FC67BBDF <19 12 7 5 4 3 1>
72 6 0xffffff7f81218000 0xe000 0xe000 x86_64 com.apple.iokit.IOSerialFamily (11) 272855EE-C816-329B-927C-383C40F83F1A <7 6 5 4 3 1>
2 8 0xffffff7f81234000 0x3940 0x3940 ????/???? com.apple.kpi.dsep (16.5.0) 6B33C49C-82D8-4830-AC91-ECF9B9EE3A8C
Notice how they are an unknown architecture (????/????). They also match this description of some mac malware that lives in RAM or NVRAM i think acording to this textbook The Art of Memory Forensics page 817. Also I've got some that are from an unknown developer in /Library/Extensions:
ACS6x.kext
ArcMSR.kext
ATTOCelerityFC8.kext
ATTOExpressSASHBA2.kext
ATTOExpressSASRAID2.kext
CalDigitHDProDrv.kext
HighPointIOP.kext
HighPointRR.kext
PromiseSTEX.kext
SoftRAID.kext
I hear that apple has pretty much said the hell with it in terms of security though and is just kind of letting a lot of things that seem like problems exist so I don't know what to think and the AppleCare people are seriously brainswashed or something bc all they can say is "that's perfectly normal." I have odd things in my network traffic and other random issues too I'm not thinking of right now but I'd really like to figure this out because I'm thinking of looking into some sort of legal action since they've allowed a serious invasion of my privacy and probably countless other people and pretty much have done everything possible to try to allow these problems to continue, although I know it would probably be pointless.
I'd really like to get a better understanding of what is happening and am happy to pay for a subscription if I could be sure that this massive problem which Apple has been beyond useless to the point where this is my last Mac and I own 4 of right now and $2000000 dollars in other Apple products almost all acting strangely in some way. Lots of fake certificates, keychain requests, webcam turns on random times throughout the day. I used a file recovery software program and it found mostly EFI files that had been deleted not by me and I don't remember any of the updates in the last 2 weeks say firmware update anywhere.
AppleCare seriously thinks I'm making it up and tried to do some fraud investigation which went nowhere and was fairly telling on their part that the only effort they'd put into was trying to blame it all on me. Sorry to rant but I'm not sure what to do. I have these sketchy kext on my computer that move around their address and I'm thinking they are related to everything:
MacBook-Pro:~ kextstat -a -s
Index Refs Address Size Wired Architecture Name (Version) UUID <Linked Against>
5 133 0xffffff7f80a00000 0x3dd0 0x3dd0 ????/???? com.apple.kpi.mach (16.5.0) E18B885B-776C-4F3A-88D4-C823FAFE12A1
3 140 0xffffff7f80a04000 0x21040 0x21040 ????/???? com.apple.kpi.iokit (16.5.0) E2BA46F4-C06A-4ACE-81E5-D9A4B6E061AA
4 146 0xffffff7f80a26000 0xd200 0xd200 ????/???? com.apple.kpi.libkern (16.5.0) 21ABA52A-C45A-4A1B-8824-F6EB5295ADDE
6 65 0xffffff7f80a34000 0xbbf0 0xbbf0 ????/???? com.apple.kpi.private (16.5.0) F0CD0AC2-92DF-4FF9-80A5-21B68641D28E
7 85 0xffffff7f80a40000 0x5890 0x5890 ????/???? com.apple.kpi.unsupported (16.5.0) 4AE97C68-EB51-4545-A2EB-007EE5A66503
1 112 0xffffff7f80a46000 0x9d90 0x9d90 ????/???? com.apple.kpi.bsd (16.5.0) D4161E07-43B8-4D47-ABFE-7DF2D693ED9A
16 16 0xffffff7f80a50000 0x27000 0x27000 x86_64 com.apple.iokit.IOStorageFamily (2.1) F908D7F5-4F54-3B89-8657-57F06350F4DB <7 6 5 4 3 1>
137 0 0xffffff7f80aef000 0x5000 0x5000 x86_64 com.webroot.driver.WebrootSecureAnywhere (23) DEFC5BE2-BCC1-3F62-9F9B-78CF3FDC1ECA <5 4 3 1>
84 3 0xffffff7f80afc000 0x2b000 0x2b000 x86_64 com.apple.iokit.IOSCSIArchitectureModelFamily (394.50.1) 82139727-96EE-3990-B7E3-950D3F9799F5 <6 5 4 3 1>
12 36 0xffffff7f80b3f000 0x35000 0x35000 x86_64 com.apple.iokit.IOPCIFamily (2.9) C6E3195E-A0D7-3B71-B5F4-9EE9E182D4FC <7 6 5 4 3>
8 7 0xffffff7f80e0c000 0xa9000 0xa9000 x86_64 com.apple.kec.corecrypto (1.0) E3701C61-A548-3181-9F3E-C90DF8327185 <7 6 5 4 3 1>
145 2 0xffffff7f80eb5000 0x5000 0x5000 x86_64 com.apple.kext.triggers (1.0) 3EAB29BE-4C7C-3D6C-B20B-B48707426005 <7 6 5 4 3 1>
9 0 0xffffff7f80f22000 0xf000 0xf000 x86_64 com.apple.kec.pthread (1) 4EFF2F70-C9B9-3176-BF83-F1B660C42135 <7 6 5 4 1>
133 0 0xffffff7f80f31000 0xf000 0xf000 x86_64 com.apple.driver.pmtelemetry (1) 963D5479-A74A-35FA-AFAA-6D61989DAD4D <7 6 5 4 3>
146 0 0xffffff7f8103b000 0x9000 0x9000 x86_64 com.apple.filesystems.autofs (3.0) E79E1801-8AB8-3BB1-A1F2-3CA5F9C7C648 <145 7 6 5 4 3 1>
11 36 0xffffff7f810e5000 0x9000 0x9000 x86_64 com.apple.iokit.IOACPIFamily (1.4) 4F7FB6AD-2498-3F71-827C-ED7AA4BF2511 <7 6 4 3>
18 1 0xffffff7f810ee000 0xd000 0xd000 x86_64 com.apple.driver.AppleBusPowerController (1.0) DB526B45-1A45-3A81-A0C1-57F826CADEDF <11 5 4 3>
19 18 0xffffff7f810fb000 0x69000 0x69000 x86_64 com.apple.iokit.IOUSBHostFamily (1.1) 96FD82D0-CFF5-3EDE-971A-456CB10DBEBF <18 7 6 5 4 3 1>
39 2 0xffffff7f8116c000 0x9a000 0x9a000 x86_64 com.apple.iokit.IOUSBFamily (900.4.1) 616CA05C-34A4-393E-8A17-93C7FC67BBDF <19 12 7 5 4 3 1>
72 6 0xffffff7f81218000 0xe000 0xe000 x86_64 com.apple.iokit.IOSerialFamily (11) 272855EE-C816-329B-927C-383C40F83F1A <7 6 5 4 3 1>
2 8 0xffffff7f81234000 0x3940 0x3940 ????/???? com.apple.kpi.dsep (16.5.0) 6B33C49C-82D8-4830-AC91-ECF9B9EE3A8C
Notice how they are an unknown architecture (????/????). They also match this description of some mac malware that lives in RAM or NVRAM i think acording to this textbook The Art of Memory Forensics page 817. Also I've got some that are from an unknown developer in /Library/Extensions:
ACS6x.kext
ArcMSR.kext
ATTOCelerityFC8.kext
ATTOExpressSASHBA2.kext
ATTOExpressSASRAID2.kext
CalDigitHDProDrv.kext
HighPointIOP.kext
HighPointRR.kext
PromiseSTEX.kext
SoftRAID.kext
I hear that apple has pretty much said the hell with it in terms of security though and is just kind of letting a lot of things that seem like problems exist so I don't know what to think and the AppleCare people are seriously brainswashed or something bc all they can say is "that's perfectly normal." I have odd things in my network traffic and other random issues too I'm not thinking of right now but I'd really like to figure this out because I'm thinking of looking into some sort of legal action since they've allowed a serious invasion of my privacy and probably countless other people and pretty much have done everything possible to try to allow these problems to continue, although I know it would probably be pointless.
Those kext were all 16.1.0 a few hours ago but before that were 16.5.0 btw. It's really strange I don't get it. They all change index number too and position on that list.
Please Submit a Support Ticket and they will let you know what's going on https://www.webrootanywhere.com/servicewelcome.asp also I see in one of the pictures that it looks like WSA can't connect to the Internet or it's Service so make sure it can connect to the internet and do another scan and if in the end it doesn't work contact support!
Thanks,
Daniel
Thanks,
Daniel
Even if your running a Trial Subscription I would still reach out to Webroot Support. They may need to look at WSA Logs on your computer to sort the problem.
As both @ and @ have said, our Support Team needs to address this.
@ , I've opened a support ticket on your behalf with our Team. Please do let us know the resolution!
Thanks for doing that. Do I need a tracking number or anything like that or will their reply come as a message on this site?
I had previously spoken to someone named Josh who was definitely helpful but I thought I had the problem resolved and never got around to screen sharing with him because Apple decided it was a fake computer (seriously) and they've since verified its not...
I had previously spoken to someone named Josh who was definitely helpful but I thought I had the problem resolved and never got around to screen sharing with him because Apple decided it was a fake computer (seriously) and they've since verified its not...
Hi thanks of the tip. I thought this was strange too since I am connected to the internet and I'm not sure why I can use the internet but it can't connect to the server. It makes me think someone purposely did something to make the program unusable.
Hello chasedaniel,@ wrote:
Thanks for doing that. Do I need a tracking number or anything like that or will their reply come as a message on this site?
You should get an email from Support with a link and a Password. Click on the link, put your email address associated with your Webroot Product, enter the password they gave you and you will see the reply from Support in the Support Ticket.
HTH,
Dave.
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.