at this time
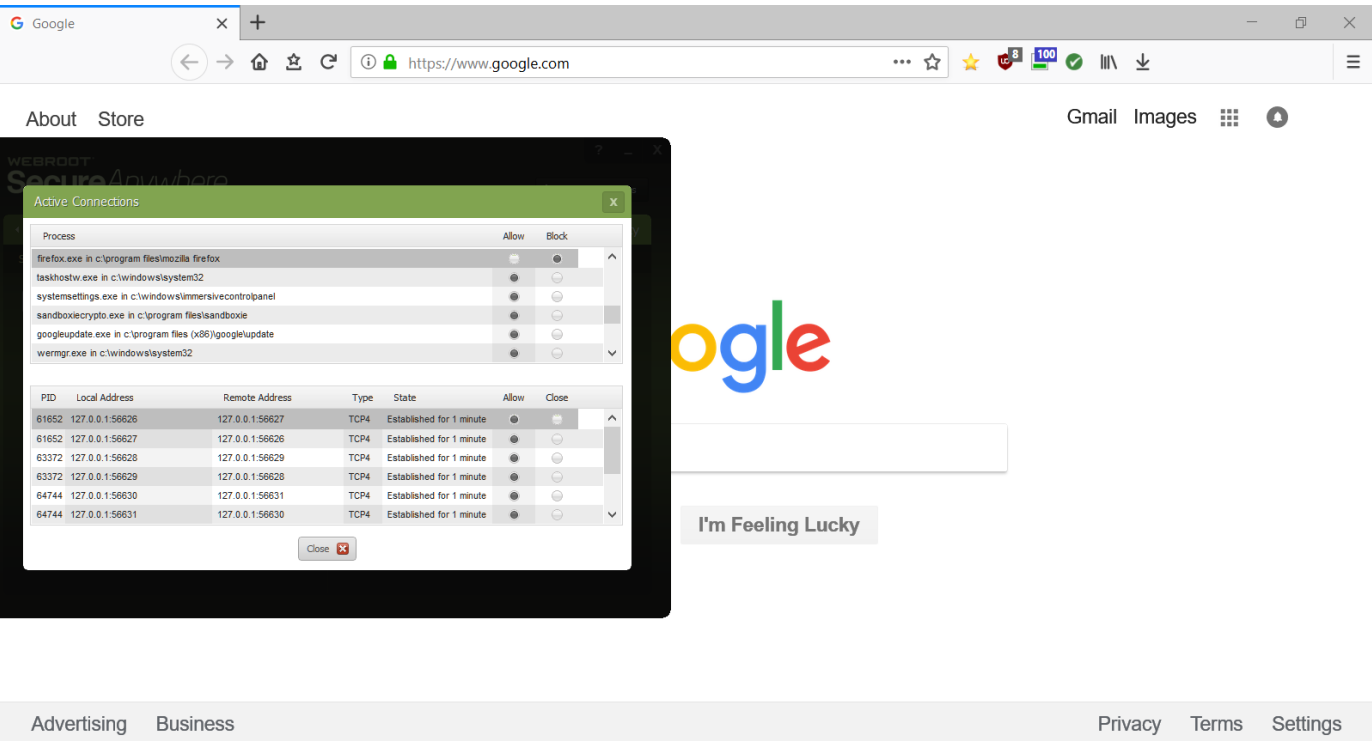
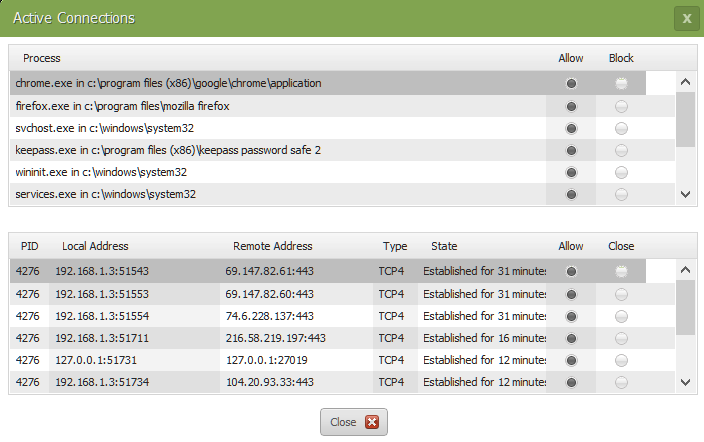
An established connection is not broken with Active Connections for firefox.exe moved to Block. And a new connection for firefox.exe (calling Firefox) is not prevented (Firefox call lands on my homepage and other pages and is fully facing the net) with Active Connection for firefox.exe at Block.
Just me?
Thanks
Page 1 / 2
Uninstalled Antivirus 9.0.24.37 & Installed Beta 9.0.24.37
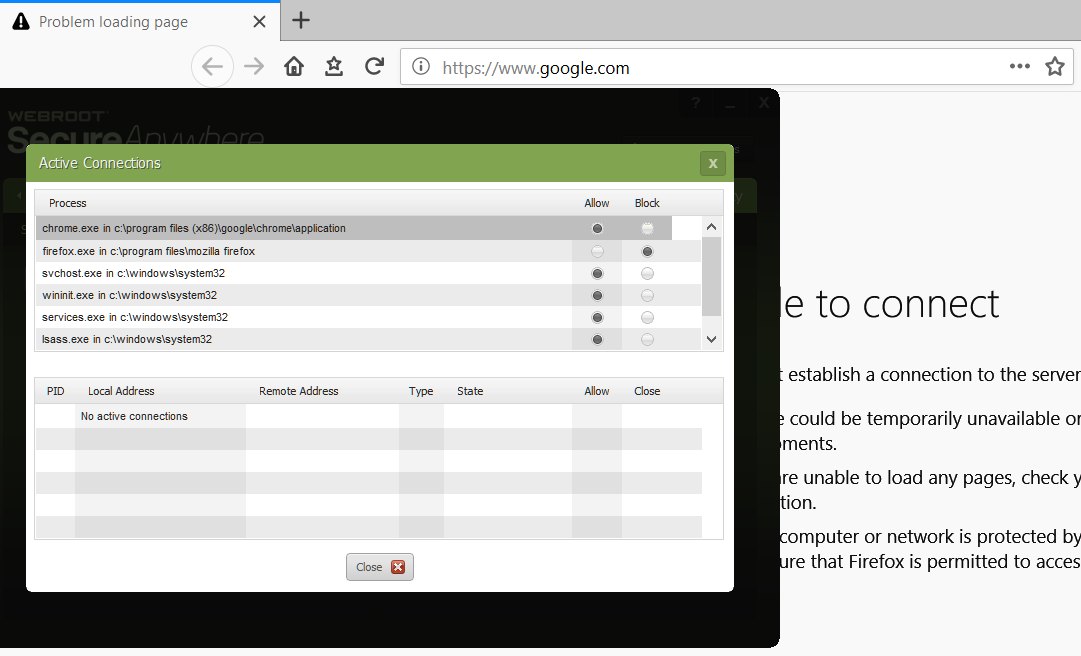
Firefox as expected | Unable to connect
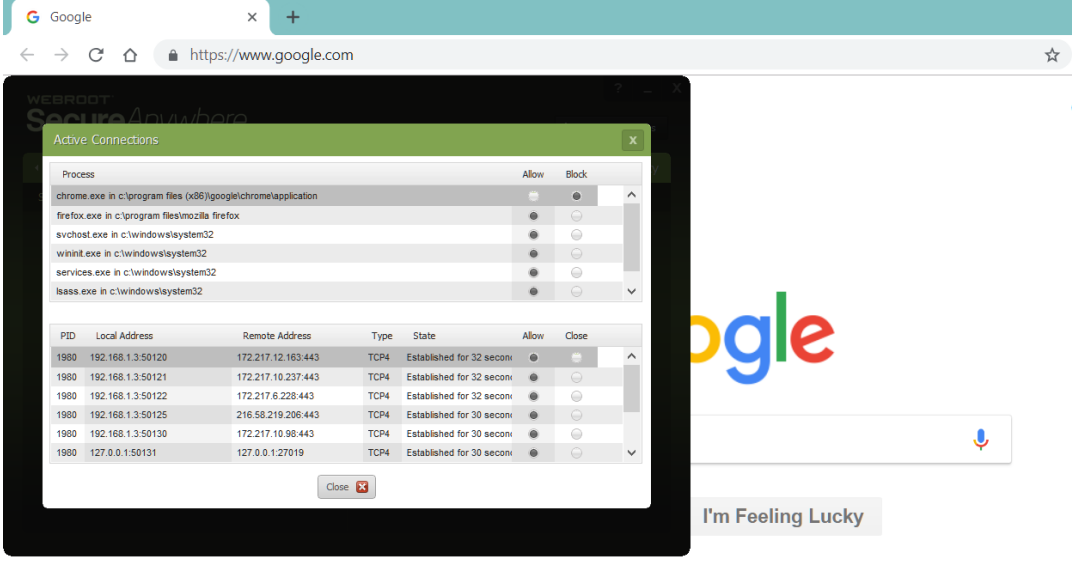
Chrome not as expected
opened Ticket
Thanks
Firefox as expected | Unable to connect
Chrome not as expected
opened Ticket
Thanks
So if you can't block a program from calling out with it's Firewall (Win 8.1 & Win 10) then how does WSA stop Malware from calling out? I would assume the level it's being Monitored at? That's what I would reply back to support about...
1) Active Connections - Block (move Allow to Block) works on an active firefox.exe connection = breaks connection.
1a) move Allow to Block with Firefox not active + call Firefox = Unable to connect.
2) Active Connections - Block (move Allow to Block) works on an active chrome.exe connection = breaks connection.
2b) move Allow to Block with Chrome not active + call Chrome = Chrome connects.
1a) vs 2b) = ?
and FWIW my observations are with Caveat: "at this time"
1a) move Allow to Block with Firefox not active + call Firefox = Unable to connect.
2) Active Connections - Block (move Allow to Block) works on an active chrome.exe connection = breaks connection.
2b) move Allow to Block with Chrome not active + call Chrome = Chrome connects.
1a) vs 2b) = ?
and FWIW my observations are with Caveat: "at this time"
Well @TechToc Lucas would know.
This, unlike some what seemed to me—albeit from a non-techie, lay-person's point of view—to be nit-picking points about very unlikely real-life scenarios coming some years ago from hjlbx (now known as Lockdown), seems to me by contrast a very important observation that needs feedback from a Webroot technician if only to reassure us.
Thanks, and please do keep us posted,@bjm_ 
Thanks, and please do keep us posted,

Thanks, and please do keep us posted,

Really! Thanks for that info now I know why he is so Critical of WSA on MT!

FWIW ~ to clarify.
Please disregard opening post (post 1). Please start reading from post 2. I did ask in post 1. Just me?. I was asking whether my observations in post 1 were an anomaly (one-off) observed by "Just me".
So, after agent re-install my observations in post 1 did show as one-off.
Please start reading from post 2.
So, to the concern whether agent can block a program calling out.
By my observe:
1) Active Connections - Block (move Allow to Block) works on an active firefox.exe connection = breaks connection.
2) Active Connections - Block (move Allow to Block) works on an active chrome.exe connection = breaks connection.
So, I'm left with 1a) vs 2b).
1a) move Allow to Block with Firefox not active + call Firefox = Unable to connect.
2b) move Allow to Block with Chrome not active + call Chrome = Chrome connects.
I don't know whether Webroot agent is designed to block non-active + call.
By my observe (1a & 2b): Firefox is unable to connect. Chrome connects.
Webroot agent does break already active connection (1 & 2) by my simple test....which does not represent real-world event.
Note: I have not tried other browsers/programs.
Thanks for reading. My apology for any confusion.
Please disregard opening post (post 1). Please start reading from post 2. I did ask in post 1. Just me?. I was asking whether my observations in post 1 were an anomaly (one-off) observed by "Just me".
So, after agent re-install my observations in post 1 did show as one-off.
Please start reading from post 2.
So, to the concern whether agent can block a program calling out.
By my observe:
1) Active Connections - Block (move Allow to Block) works on an active firefox.exe connection = breaks connection.
2) Active Connections - Block (move Allow to Block) works on an active chrome.exe connection = breaks connection.
So, I'm left with 1a) vs 2b).
1a) move Allow to Block with Firefox not active + call Firefox = Unable to connect.
2b) move Allow to Block with Chrome not active + call Chrome = Chrome connects.
I don't know whether Webroot agent is designed to block non-active + call.
By my observe (1a & 2b): Firefox is unable to connect. Chrome connects.
Webroot agent does break already active connection (1 & 2) by my simple test....which does not represent real-world event.
Note: I have not tried other browsers/programs.
Thanks for reading. My apology for any confusion.
This is a case where I am expecting a Webroot technician (like @TechToc ) to reassure us. I would be surprised if this proves to be a problem with malware being able to phone out. But obviously would appreciate reassurance.
I personally think it was good, even important, for@bjm_ to point this anomaly out. And to ask for answers, both from Support and on this Forum. I'm looking forward to hearing what Support says re:
So if you can't block a program from calling out with it's Firewall (Win 8.1 & Win 10) then how does WSA stop Malware from calling out? I would assume the level it's being Monitored at?
Btw my policy is to tell someone when I disagree with them. And to tell them when I agree with them.
Well, I'll try and keep a low profile on this thread until we get a response either from Support, communicated to us by@bjm_ , or by a Webroot technician responding directly to this thread, or both.
Maybe@LLiddell or @freydrew , would you be able to help expedite a response on this one?
EDIT: Maybe my previous post wasn't clear to all. I was contrasting the dim view I took of hjlbx's posts at the time, and the valid question that I think@bjm_ addresses in this thread.
I personally think it was good, even important, for
Btw my policy is to tell someone when I disagree with them. And to tell them when I agree with them.
Well, I'll try and keep a low profile on this thread until we get a response either from Support, communicated to us by
Maybe
EDIT: Maybe my previous post wasn't clear to all. I was contrasting the dim view I took of hjlbx's posts at the time, and the valid question that I think
🙂 Good work TH on noting who was replying. That said, BJM_ I'm still a bit confused on what it is exactly you are attempting to show here.
You have two different applications:
It seems to me that the question is why doesn't Chrome behave the same way?
With that said, after moving through a number of different permutations of this, The behavior appears to be PID (Process Identifier) based. As a result, different tabs, as well as processes are handled in differing ways within the agent. This is behavior that is somewhat unique to browsers. I'm sure everyone is aware that launching any modern browser launches a number of subsequent processes, This is a sandboxing and fault tolerance behavior in the event of malicious code execution, as well as runaway scripts. This allows for termination of the specific process without interfering with the user's browser session.
Malware rarely behaves in this way, and generally only launches a single process or a child and parent process, each with unique functions. And, in many case one or the other PID could be a perfectly legitimate application.
The firewall functions describe here were not intended to block legitimate browser traffic. Additionally, the firewall functionality is highly tied to agent state (threat detected state, vs. normal non-infected state). Further, it was never designed to perform functions of a software firewall, and really shouldn't be used that way. It's function within the agent is to prevent malicious software from communicating over the internet. In my experience, it does this pretty well.
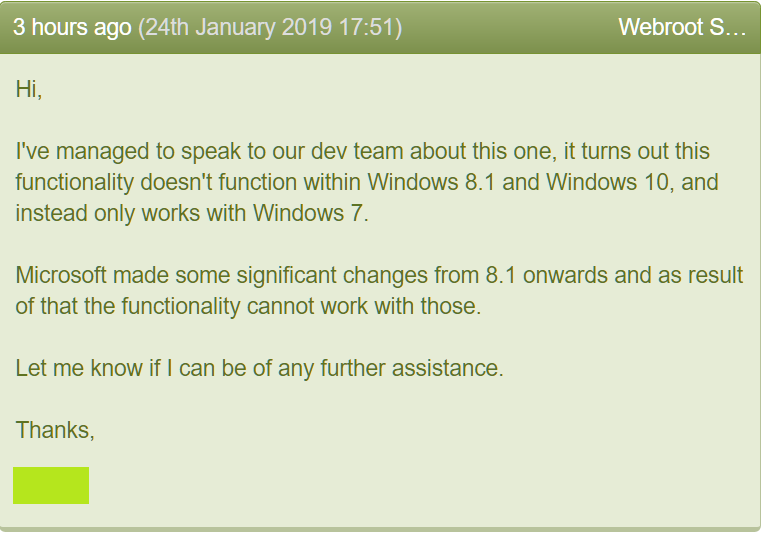
With that said, my earlier statements are still accurate. The behavior of the Active Processes list differs between Windows 7, and Windows 8/10. Some of you may remember that the screen wasn't functional at all until sometime after Windows 10 was launched. This was the result of significant changes in how we perform this function between operating systems.
I appreciate the testing here, however, to address the issue in a more real world accurate sense I'd recommend leveraging a single internet based application that launches a single PID and performing the block in this scenario
Hope this clarifies my understanding of this test. Please let me know if I can offer additional information.
You have two different applications:
- Firefox
- Chrome
It seems to me that the question is why doesn't Chrome behave the same way?
With that said, after moving through a number of different permutations of this, The behavior appears to be PID (Process Identifier) based. As a result, different tabs, as well as processes are handled in differing ways within the agent. This is behavior that is somewhat unique to browsers. I'm sure everyone is aware that launching any modern browser launches a number of subsequent processes, This is a sandboxing and fault tolerance behavior in the event of malicious code execution, as well as runaway scripts. This allows for termination of the specific process without interfering with the user's browser session.
Malware rarely behaves in this way, and generally only launches a single process or a child and parent process, each with unique functions. And, in many case one or the other PID could be a perfectly legitimate application.
The firewall functions describe here were not intended to block legitimate browser traffic. Additionally, the firewall functionality is highly tied to agent state (threat detected state, vs. normal non-infected state). Further, it was never designed to perform functions of a software firewall, and really shouldn't be used that way. It's function within the agent is to prevent malicious software from communicating over the internet. In my experience, it does this pretty well.
With that said, my earlier statements are still accurate. The behavior of the Active Processes list differs between Windows 7, and Windows 8/10. Some of you may remember that the screen wasn't functional at all until sometime after Windows 10 was launched. This was the result of significant changes in how we perform this function between operating systems.
I appreciate the testing here, however, to address the issue in a more real world accurate sense I'd recommend leveraging a single internet based application that launches a single PID and performing the block in this scenario
Hope this clarifies my understanding of this test. Please let me know if I can offer additional information.
Thanks Lucas and have a great day and Weekend!
Cheers,
Cheers,
...and thanks for responding so quickly 

Noted: agent firewall was never designed to perform functions of a software firewall, and really shouldn't be used that way.
Thanks: important need-to-know information.
It seems to me that the question is why doesn't Chrome behave the same way?
Yep.
....to address the issue in a more real world accurate sense I'd recommend leveraging a single internet based application that launches a single PID and performing the block in this scenario
Noted.
bjm_
My personal understanding is that he isn’t trying to "show" anything but rather trying to probe Webroot to see if it is really what it claims to be.
My gut-feeling, and after some amount of communication with him, is that, compared to me for example:
- I, having used Prevx/Webroot for more than 12 years now, am convinced that it works really well, at least until someone can show me otherwise.
- On the other hand, bjm_ takes the view of a healthy skeptic: that is, he is probing and testing Webroot to see if it is what it claims to be, and will not be convinced until he can see all his questions answered satisfactorily.
Yes, I am alarmed too by certain behaviour I have seen on his part on the MT website, and I have strongly challenged him about this in a publically facing post, i.e. in a public post on this Forum rather than by PM. That exchange continued subsequently by PM and the above is how I have come to understand bjm_’s attitude.
No, he is not a Webroot cheerleader but maybe that is a good thing. Maybe, if we allow him to probe Webroot, and let Webroot patiently deal with and try to reply to each question he (quite legitimately imo) asks, this could help those who question Webroot’s approach to better understand how Webroot works—and maybe, as a bonus, help us to understand Webroot even better.
That is why I welcome this, and any other legitimate, question he has to ask, as he probes and tests its core functions.
Anyway, that's just my opinion.
Respectfully, I'm not attempting to show anything, here.
I was trying to understand a bit more about the Block and Close feature.
Agent offers me Block and Close function.
https://docs.webroot.com/us/en/home/wsa_pc_userguide/wsa_pc_userguide.htm#UsingFirewallWebShieldProtection/ManagingActiveConnections.htm does not speak to Block nor Close.
That's all. No ulterior motive. No hidden agenda. No grand scheme.
I'm not that complicated. Just curious.
That's all. I'm not trying to garner favor & try not to step harshly.
I'm bewildered why my questions, comments, opinions, observations here or elsewhere are met with suspicion....met with harsh.
I'm unknowing why anything I say here or elsewhere is under scrutiny.
I didn't run over anyone's dog.
Block and Close function....curious.
That's all. No agenda. Just curious.
bjm_
I think the discordance between what you say elsewhere and what you say here shocks people.
But I agree 100% with the rest of what you say

Bottom Line: No member will ever know what's all the features "Under the Hood" of Webroot. 

"shocks"
IDK. Sorry.
I'm not that invested one way or the other.
bjm_

I know more than yesterday. Whether I'll remember...that's an open question.

I am really surprised at this debate and especially that there would be a need to emphasise the fact that the WRSA outbound firewall component is NOT a full blown firewall, and only a 'hardening' of the resident firewall's outbound component.
That has always been the case, from the year dot, re. WRSA and is the reason why users MUST either use the built in Windows Firewall or a suitable 3rd party alternative, with both inbound & outbound components fully enabled.
Thought that was common knowledge...but always OK to be disabused of this view if it is incorrect.
Regards, Baldrick
That has always been the case, from the year dot, re. WRSA and is the reason why users MUST either use the built in Windows Firewall or a suitable 3rd party alternative, with both inbound & outbound components fully enabled.
Thought that was common knowledge...but always OK to be disabused of this view if it is incorrect.
Regards, Baldrick
.....and how do you et al use Block and Close ?
https://docs.webroot.com/us/en/home/wsa_pc_userguide/wsa_pc_userguide.htm#UsingFirewallWebShieldProtection/ManagingActiveConnections.htm does not speak to Block nor Close.
https://docs.webroot.com/us/en/home/wsa_pc_userguide/wsa_pc_userguide.htm#UsingFirewallWebShieldProtection/ManagingActiveConnections.htm does not speak to Block nor Close.
"The SecureAnywhere firewall monitors data traffic traveling out of your computer ports. It looks for untrusted processes that try to connect to the Internet and steal your personal information. It works with the Windows firewall, which monitors data traffic coming into your computer. With both the SecureAnywhere and Windows firewall turned on, your data has complete inbound and outbound protection.
You should not turn off either the Windows firewall or the SecureAnywhere firewall. If they are disabled, your system is open to many types of threats whenever you connect to the Internet or to a network. These firewalls can block malware, hacking attempts, and other online threats before they can cause damage to your system or compromise your security.
The SecureAnywhere firewall is preconfigured to filter traffic on your computer. It works in the background without disrupting your normal activities. If the firewall detects any unrecognized traffic, it opens an alert where you can block the traffic or allow it to proceed."
In general, I never have to change or adjust the Active Connections...WRSA just does its stuff. And I will leave it at that.
Regards, Baldrick
You should not turn off either the Windows firewall or the SecureAnywhere firewall. If they are disabled, your system is open to many types of threats whenever you connect to the Internet or to a network. These firewalls can block malware, hacking attempts, and other online threats before they can cause damage to your system or compromise your security.
The SecureAnywhere firewall is preconfigured to filter traffic on your computer. It works in the background without disrupting your normal activities. If the firewall detects any unrecognized traffic, it opens an alert where you can block the traffic or allow it to proceed."
In general, I never have to change or adjust the Active Connections...WRSA just does its stuff. And I will leave it at that.
Regards, Baldrick
*** A -- B -- C ***
A-- I use Block and Close. I know why/how.
B-- I do not use Block and Close. I do not know why/how.
C-- Other. Please explain.
A-- I use Block and Close. I know why/how.
B-- I do not use Block and Close. I do not know why/how.
C-- Other. Please explain.
A-- I use Block and Close. I know why/how.
B-- I do not use Block and Close. I do not know why/how.
C-- Other. Please explain.
??????????????????
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.