There's talk at Wilder's Security Forum of a new Ransomeware which is spreading by P2P networks. This Ransomeware is able to flash your bios, but it is not known at this time the changes it is making to the bios. One user which has already fallen victim to this malware says replacing your hard drive will not remove the threat. Zfactor at Wilders is trying to obatain a sample which compromised a friends computer. The victim says he has scanned his computer with norton, eset, avira, avast, dr web, bitdefender, webroot, gdata, fsecure, panda, avg, emsisoft, vipre, mcafee, comodo, ikarus, kaspersky, trend, fortinet among others , and none of them have detected the threat. The victim of this threat says he still has not been able to remove the threat even after replacing the hard drive. He says he is going to replace the memory next which I myself do not think will help from the sound of it. The Ransomewear has him locked out of the bios. I think as we find out more about this threat that it's complexity will be comparible to Stuxnet even though they are totally two different types of malware. I difinitely do not want to have to deal with removing this one. Look at post 4, and 14 of this thread for more information http://www.wilderssecurity.com/showthread.php?p=2247738#post2247738
Is Webroot's Threat Research Group aware of any new Ransomeware or variants that are spreading by P2P Networks that is causing such damage? Has Webroot obtained any samples, or has anything appeared in the cloud yet that sounds like what the victim mentioned above has been infected with? The victim believe's he got it torrenting. He says none of the AV companies are currently detecting this threat. He is currently using Bitdefender. This one will cause major financial losses if it becomes wide spread. Can you imagine the damage it will cause if it spreads to Small Busineses- Medium size Businesses, Corporate, and Government networks!?
Edited @ 1933 6/30/2013: By the way nothing has been confirmed yet. The only cases I have heard of at this time are the two users in the Widler's thread which the link above leads to.
Page 1 / 1
On some private security forums that I'm a member at have not posted anything at this time and also searching for such reveals nothing ATM? Also if it's P2P related I have no concern, it's interesting though that it attacks the BIOS if the malware runs. You can search this Term and it will get results in the Netherlands: You steal music I lock your pc [Ransomware]
Daniel
Daniel
Lets just hope it does not become wide spread beyond P2P Networks. Regardless, a professional Security Company is responsible for protecting their customers from all threats regardless of orgin to a certain extinct. There are still lawful use of P2P technology. It's also about taking pride in ones work to be able to say we were the first to discover or detect that threat. Our products are state of the art; cutting edge. We work hard to protect our customers. I could go on, but I think everyone gets the picture. 🙂
I know and it will be nice if one of the Webroot Threat Researchers would chime in on this when they come online. ;)
TH
TH
I was hoping they have already obtained a sample or maybe the cloud has or will identify it soon.
A part of me is extremely curious to see a real life example of this. BIOS infections are extremely rare and I havent seen one in a very long time. You would be so unlucky to get infected by one, thankfully my PC at home has a dual bios that you can flash one if it gets damaged. In the good old days if you got one of these you could swap out the bios by pulling out the physical chip. That isnt an option anymore!
I will see if I can find any sample I will check my usual source. If anybody gets a d/l link drop me a PM. If anybody suspects they are infected with this DO NOT REBOOT YOUR PC. You can reflash your BIOS with the correct image, rebooting your PC before doing so will mean your PC wont boot. As for the report the cynic in me says that this isnt out in the wild 🙂 However its going to be hard to trace down a sample.
I am also curious to how exactly the path of the infection and will effect UEFI PC`s or only older BIOS PC`s?
I will see if I can find any sample I will check my usual source. If anybody gets a d/l link drop me a PM. If anybody suspects they are infected with this DO NOT REBOOT YOUR PC. You can reflash your BIOS with the correct image, rebooting your PC before doing so will mean your PC wont boot. As for the report the cynic in me says that this isnt out in the wild 🙂 However its going to be hard to trace down a sample.
I am also curious to how exactly the path of the infection and will effect UEFI PC`s or only older BIOS PC`s?
Nobody seems to have posted a sample online nor is there much information about the rogue, other than screenshots. Going to keep checking online.
What about passwording your Bios and elevating UAC to ask for credentials even with an Admin account?
This will prevent;
Installing any .exe
flashing the BIOS
This will prevent;
Installing any .exe
flashing the BIOS
I imagine password protecting your BIOS won't do much because it's only applicable on power up so once your in - your in, so flashing is still possible.@ wrote:
What about passwording your Bios and elevating UAC to ask for credentials even with an Admin account?
This will prevent;
Installing any .exe
flashing the BIOS
I'm still amazed at how something as specific as BIOS (specific hardware, models etc) can be exploited so simply, perhaps this is why we are not seeing many samples and the exploited version is generic (then again, why even bother going for a BIOS exploit - makes me think hoax).
What do you mean by " once your in - your in" ???
On my laptop (an old ThinkPad R60) I have the option
Flash BIOS Updating by End-User ----> Dissabled ,
with the explanation for "Dissabled" : Entering Supervisor password is required to update Flash BIOS
So it seems like , without a Supervisor password you CANNOT update Flash BIOS
On my laptop (an old ThinkPad R60) I have the option
Flash BIOS Updating by End-User ----> Dissabled ,
with the explanation for "Dissabled" : Entering Supervisor password is required to update Flash BIOS
So it seems like , without a Supervisor password you CANNOT update Flash BIOS
You can flash the BIOS in windows and I dont think a BIOS password will stop that.
topor wrote:
So it seems like , without a Supervisor password you CANNOT update Flash BIOS
Rakanisheu wrote:
You can flash the BIOS in windows and I dont think a BIOS password will stop that.And I just tested that theory on my Dell M4500 Workstation which got a new BIOS update at the start of last month. What I did was turn on the System password in the BIOS (for access to the system when powered on) for testing.
Ran the update as normal, laptop reboot and went to BIOS Update Progress and didn't ask for password (as the BIOS is clever and only looks for a password from a cold boot).
Again I have to go back to the issue at hand - every model of laptop / desktop in the world has different signed / particular BIOS updates and I don't believe a "generic" build could be universally designed unless it's dedicated to a specific make / model.
Have a look at this article as some are saying it's a Hoax notice post #29 & #31: http://www.wilderssecurity.com/showthread.php?t=349647&page=2
"filename "lcrm.exe"
Also look at the translated thread links in this Article: http://www.malwareremovalguides.info/you-steal-music-i-lock-your-pc-ransomware/
Daniel
"filename "lcrm.exe"
Also look at the translated thread links in this Article: http://www.malwareremovalguides.info/you-steal-music-i-lock-your-pc-ransomware/
Daniel
I'm curious as to how many Brands, and models this Ransomeware is able to compromise. I think for the most part each brand, and each model # use a different authentication key for the bios? I mean each brand of PC does not use the same authentication key for all it's models. Maybe a particular brand of PC might use the same authentication key for several of it's models, but not all. Doesn't it depend on the chipset? Does someone like HP, Gateway, etc.. use the same chipset in several of it's models, or do they normally use a different chipset for each model?
Yahoo mail is working for me now 🙂 Yah!! lol
Definately settled on hoax. Even if it was possible to create a uninversal BIOS package for all devices - why even bother? This is definately not ransomware - the only reason ransomware exists is for money and this "malware" disables your PC. So unless someones comes to your door asking for a cheque, I think we are safe ;)
EDIT: And confirmed - https://www.security.nl/artikel/46857/1/Onbekend_BIOS-virus_zeer_waarschijnlijk_hoax.html
EDIT: And confirmed - https://www.security.nl/artikel/46857/1/Onbekend_BIOS-virus_zeer_waarschijnlijk_hoax.html
If someone comes to my door demanding money to unlock my PC's then I have the answer for that. They might find themself paying me to unlock them lol
Yes, i'm inclined to think it is a hoax as well after seeing Zfactor's reply over at Wilders. It would have been great to get a sample of malware with such high capaibilities, but i'm also releived there is no infection spreading rapidly in the wilder with those capabilities as far as I know. Who knows about tomorrow though. Maybe with how well designed some malware is becoming it could be a reality at any time.
Hi EamonF,
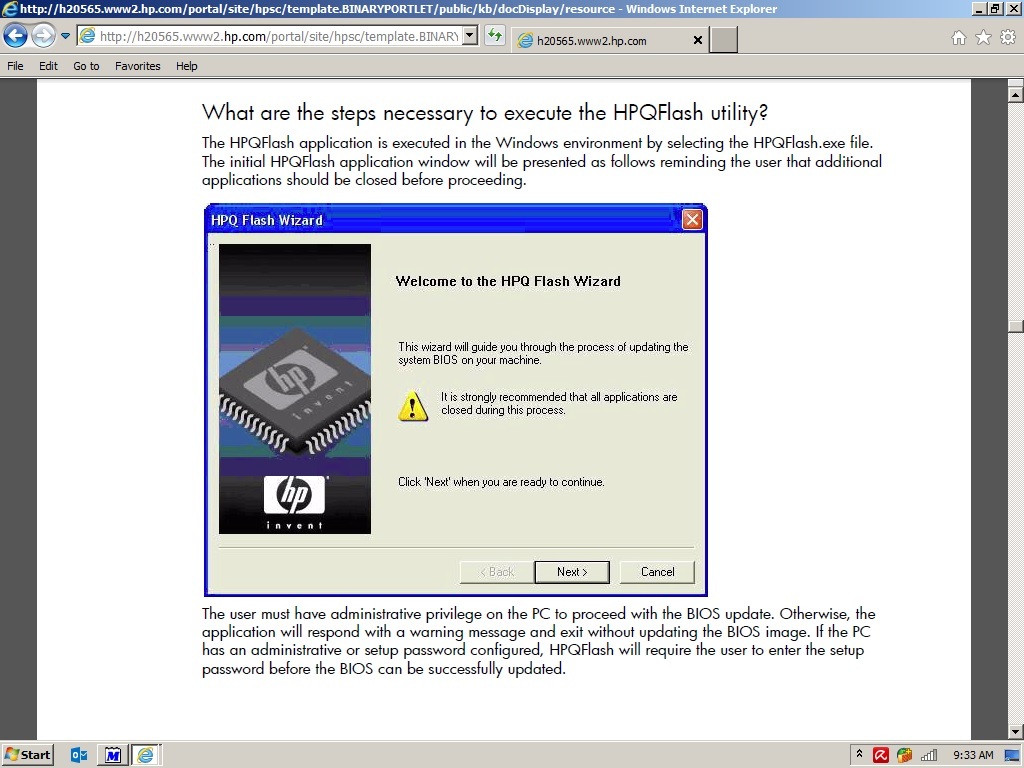
Business line Dell machines have multiple layers of BIOS password options. Owner password (only avaliable through Dell CCTK), Setup password, and System password.
The BIOS setup password will need to be entered to update the BIOS if it is set.
Business line Dell machines have multiple layers of BIOS password options. Owner password (only avaliable through Dell CCTK), Setup password, and System password.
The BIOS setup password will need to be entered to update the BIOS if it is set.
Yes, I believe it is a good ideal to password protect the BIOS. Just don't forget the password! Do you mean Dell will be the only one to have the password? Doesn't the local Network Admin have the BIOS password without having to contact Dell?
BIOS system/setup passwords (they're really UEFI now, but we'll keep calling it that) are separate from the operating system and stored on a chip actually on the motherboard. Although the passwords can be set when you're inside of the OS on enterprise-grade machines using special drivers and programs, IT has no special ability to override them. (Unless they're smart and they've set an Owner password or are using Intel AMT/vPro.)
When it comes to forgotten BIOS passwords, there are two options. With desktops you can reset the BIOS "memory" with a jumper/by removing the battery. In the case of laptops, if you'e lucky the BIOS will generate an alphanumeric string with an algorithm based on the machine's configuration. You can tell that code to the manufacturer, and if they believe you are the valid owner, they can provide a "response" code that will unlock the password. If you don't have that option, the thing is bricked.
Unfortunately, the algorithms that generate these codes are simple to reverse engineer and there are programs to generate these codes without the manufacturer's involvement. But beware, unless you're getting these programs direct from the person who actually coded it, you're actually just downloading a fake one that's really just a virus.
In the case of business machines, there are other management layers so there can be other passwords and locks involved. I'm just discussing the run of the mill system/setup passwords. HDD passwords are also actually on the HDD itself, you can't just reset those.
When it comes to forgotten BIOS passwords, there are two options. With desktops you can reset the BIOS "memory" with a jumper/by removing the battery. In the case of laptops, if you'e lucky the BIOS will generate an alphanumeric string with an algorithm based on the machine's configuration. You can tell that code to the manufacturer, and if they believe you are the valid owner, they can provide a "response" code that will unlock the password. If you don't have that option, the thing is bricked.
Unfortunately, the algorithms that generate these codes are simple to reverse engineer and there are programs to generate these codes without the manufacturer's involvement. But beware, unless you're getting these programs direct from the person who actually coded it, you're actually just downloading a fake one that's really just a virus.
In the case of business machines, there are other management layers so there can be other passwords and locks involved. I'm just discussing the run of the mill system/setup passwords. HDD passwords are also actually on the HDD itself, you can't just reset those.
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.