I recently bought an HP laptop with Windows 10 Home installed on it, previously using Windows 7 and WRSA on othr PCs.
I installed WRSA Antivirus on the new laptop and the Windows 10 firewall is switched on, also the WRSA firewall is switched on.
I am a long-time WRSA user and recall that the WRSA firewall works in a complementary way on top of the Windows firewall, so no problems so far....
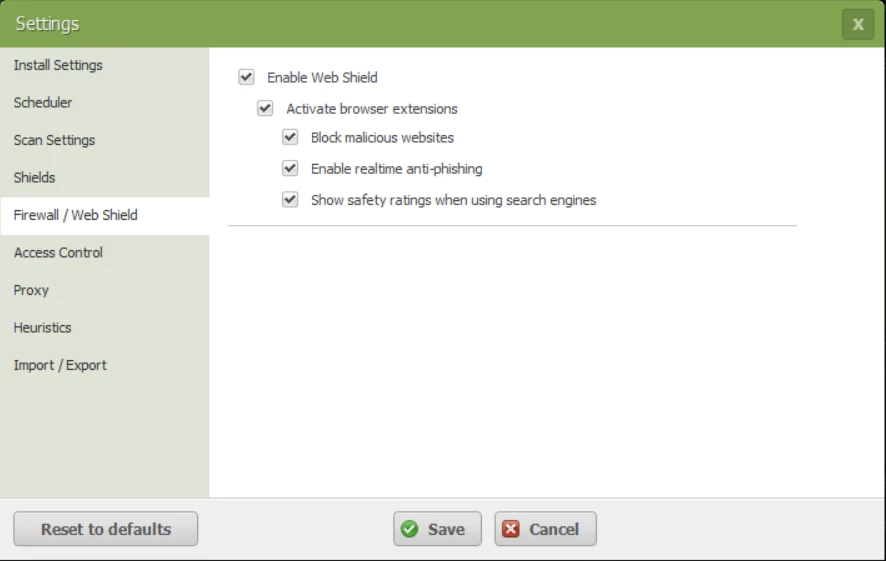
In advanced settings, under Firewall / Webshield there appear only webshield options, the Firewall options are completely blank. Is this normal on Windows 10 ?
I previously used WRSA Complete so I thought that restriction might be due to version differences as well?
Screenshot attached. Appreciate a quick answer please, need to go travelling soon and would like to increase the level of firewall protection to alert when new unknown processes start, not just when WRSA thinks I am infected..
Page 1 / 2
Yes that is normal on W10 and has been like this since W8. The WSA product version makes no difference.
It is explained here.
It is explained here.
Interesting, thanks. So what does the WRSA firewall actually do then? It's not linked directly to the Windows firewall insomuch as when I disable the WRSA firewall the Windows 10 firewall remains on. What are the WRSA firewall actions, same as on Windows 7 but without the ability to control options?
It still has a Firewall and it's a Smart Firewall as it will block malware from calling out to it's control center and you will get a pop-up if that's the case. If you want more granular control maybe look for a third party firewall but again it still uses the same API's from Windows 10. https://en.wikipedia.org/wiki/Application_programming_interface
Note what JoeJ said here:
"PrevxHelp( JoeJ, VP of Development ) wrote:
The firewall in Windows 8 is much easier to work with than previous platforms because of the built in OS controls. Every vendor needs to use the same APIs now (the older methods are deprecated), but that's exactly why we aren't doing it currently - no matter what vendor wraps the APIs, it will be exactly the same underlying calls which are built into the OS, and you can use the OS UI to do the same job if you want to customize it.
The reason why we have the functionality on Windows 7 and not Windows 8 is because Microsoft doesn't expose the same normalized interfaces on Windows 7 (or require vendors to use the new APIs)."
Thanks,
Daniel 😉
Note what JoeJ said here:
"PrevxHelp( JoeJ, VP of Development ) wrote:
The firewall in Windows 8 is much easier to work with than previous platforms because of the built in OS controls. Every vendor needs to use the same APIs now (the older methods are deprecated), but that's exactly why we aren't doing it currently - no matter what vendor wraps the APIs, it will be exactly the same underlying calls which are built into the OS, and you can use the OS UI to do the same job if you want to customize it.
The reason why we have the functionality on Windows 7 and not Windows 8 is because Microsoft doesn't expose the same normalized interfaces on Windows 7 (or require vendors to use the new APIs)."
Thanks,
Daniel 😉
@ wrote:
It still has a Firewall and it's a Smart Firewall as it will block malware from calling out to it's control center and you will get a pop-up if that's the case. If you want more granular control maybe look for a third party firewall but again it still uses the same API's from Windows 10. https://en.wikipedia.org/wiki/Application_programming_interface
Note what JoeJ said here:
"PrevxHelp( JoeJ, VP of Development ) wrote:
The firewall in Windows 8 is much easier to work with than previous platforms because of the built in OS controls. Every vendor needs to use the same APIs now (the older methods are deprecated), but that's exactly why we aren't doing it currently - no matter what vendor wraps the APIs, it will be exactly the same underlying calls which are built into the OS, and you can use the OS UI to do the same job if you want to customize it.
The reason why we have the functionality on Windows 7 and not Windows 8 is because Microsoft doesn't expose the same normalized interfaces on Windows 7 (or require vendors to use the new APIs)."
Thanks,
Daniel ;)
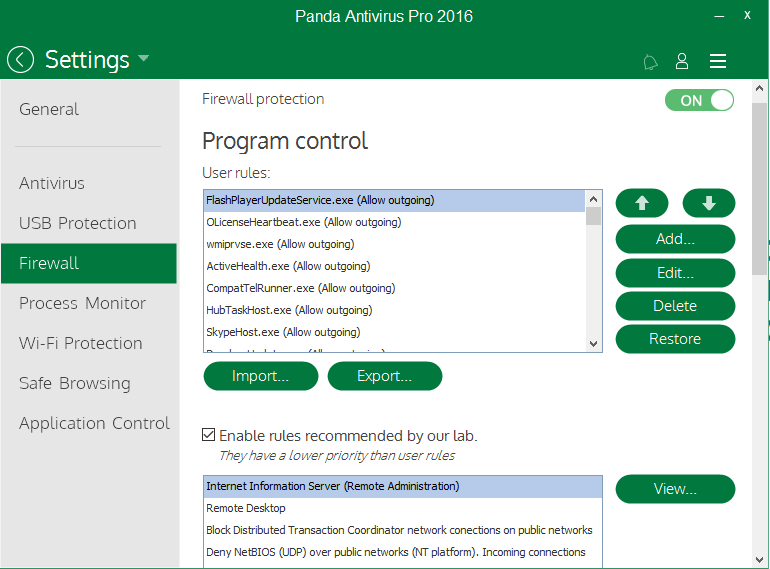
I thought that sounded a great reason Daniel, thanks for sharing, but yesterday I did a test on Panda because I was curious after seeing something on their website, and I was then really surprised to see that they seem to have firewall control over processes in Windows 10 in a similar way to WRSA on Windows 7 but which is not available in Windows 10.
I've attached a screenshot for reference (hope this is not going against forum rules, it's not intentional, pls remove if needed) I just want to illustrate my strong desire to have WRSA return to this firewall ability in Windows 10 which another company seems to be already providing. If I am "barking up the wrong tree" please let me know!
Hi cavehomme
There is a great deal of confusion about this particular area of WSA and to be honest we are not sure as to exactly the limitations and under what rules the Development Team are operating under. As you example shows there are ways to do what you are requesting but the issue remains as to whether the design of WSA currently would allow this or not.
Of course, we can expend a great deal of time and/or lines of posts in a debate that at the end of it may be moot as it is down to Webroot's product strategy, etc.
Having said that there is nothing to stop you from opening a Feature Request for this in the Ideas Exchange. There have been a number of these over the last year or so and none have gained much traction witht he Development Team but perhaps a new Request, formed based on what you have provided in this thread may have more chance of success. So go ahead, raise a request, and we will see how much traction this one gains and whether in the light of what the competition is now doing the Development Team are prepared to take another look at some more granular outbound firewall functionality being included in future versions.
Regards, Baldrick
There is a great deal of confusion about this particular area of WSA and to be honest we are not sure as to exactly the limitations and under what rules the Development Team are operating under. As you example shows there are ways to do what you are requesting but the issue remains as to whether the design of WSA currently would allow this or not.
Of course, we can expend a great deal of time and/or lines of posts in a debate that at the end of it may be moot as it is down to Webroot's product strategy, etc.
Having said that there is nothing to stop you from opening a Feature Request for this in the Ideas Exchange. There have been a number of these over the last year or so and none have gained much traction witht he Development Team but perhaps a new Request, formed based on what you have provided in this thread may have more chance of success. So go ahead, raise a request, and we will see how much traction this one gains and whether in the light of what the competition is now doing the Development Team are prepared to take another look at some more granular outbound firewall functionality being included in future versions.
Regards, Baldrick
Thanks for the suggestion Baldrick. My understanding form the earlier post was that it was not technically possible due to the way that Windows 10 works compared to Windows 7, but now it seems that it's possibly a product design choice. That's a big difference and it's not something unfortunately I've got time to think more about and post requests at the moment, but thanks again for the suggestion.
Perhaps I am barking up the wrong tree, thinking about it, all I simply want the Windows 7 WRSA feature enableed of not allowing unknown outbound processes to communicate to the internet rather than the default option of not allowing this only when infected....but perhaps someone can let me know if perhaps this might be already the default in the WRSA Windows 10 version albeit hidden? I don't need the rest of the granularity options, I don't want to tinker with processes, etc, just that simple but important option. Thanks!
Perhaps I am barking up the wrong tree, thinking about it, all I simply want the Windows 7 WRSA feature enableed of not allowing unknown outbound processes to communicate to the internet rather than the default option of not allowing this only when infected....but perhaps someone can let me know if perhaps this might be already the default in the WRSA Windows 10 version albeit hidden? I don't need the rest of the granularity options, I don't want to tinker with processes, etc, just that simple but important option. Thanks!
Hi cavehomme
I completely understand where you are coming from with this...you just want the Windows 7 level fucntionalioty; nothing more...and I suspect that many of us out there feel the same way so I would urge you to open a Feature Request so that all those that agree with you can comment/support the suggestion and also it becomes apparent to the Development Team that there is a requirment for this feature to be reinstated, etc. Especially since you are quite correct and we are seeing a number of applications out there that are managing to interface with the WPS (as opposed to the older, and now defunct, WFC) functionality and thereby have some control as to what occurs outbound.
With reagrd to "...this might be already the default in the WRSA Windows 10 version albeit hidden?" I can categorically state that this is not currently possible in WSA and there is no 'hidden' fucntionality that would allo one to do that...apologies!
Regards, Baldrick
I completely understand where you are coming from with this...you just want the Windows 7 level fucntionalioty; nothing more...and I suspect that many of us out there feel the same way so I would urge you to open a Feature Request so that all those that agree with you can comment/support the suggestion and also it becomes apparent to the Development Team that there is a requirment for this feature to be reinstated, etc. Especially since you are quite correct and we are seeing a number of applications out there that are managing to interface with the WPS (as opposed to the older, and now defunct, WFC) functionality and thereby have some control as to what occurs outbound.
With reagrd to "...this might be already the default in the WRSA Windows 10 version albeit hidden?" I can categorically state that this is not currently possible in WSA and there is no 'hidden' fucntionality that would allo one to do that...apologies!
Regards, Baldrick
Thanks for clarifying Baldrick.
I may now need to eat my earlier words, I have just discovered that Panda AV Pro in fact includes a fully functioning firewall that REPLACES the Windows firewall ! I had no idea and thought it was just outbound control. I don't know what extra their IS suite offers but it's surprising to see a firewall in the AV product since it's not really just an AV then.
Anyway, where this leads me to is that most likely the original statement is correct that the option / granularity that I seek cannot be achieved in Windows 10 due to the restrictions imposed by Microsoft. Anway, I guess I have confidence in WRSA to make the right choices and so I'll continue to use it. Just hope my earlier feature request (not directly related to this issue) of immediately removing known threats via an online lookup gets approved.
Apologies for any confusion that I caused, I'll be more awake next time I post ! 😉
I may now need to eat my earlier words, I have just discovered that Panda AV Pro in fact includes a fully functioning firewall that REPLACES the Windows firewall ! I had no idea and thought it was just outbound control. I don't know what extra their IS suite offers but it's surprising to see a firewall in the AV product since it's not really just an AV then.
Anyway, where this leads me to is that most likely the original statement is correct that the option / granularity that I seek cannot be achieved in Windows 10 due to the restrictions imposed by Microsoft. Anway, I guess I have confidence in WRSA to make the right choices and so I'll continue to use it. Just hope my earlier feature request (not directly related to this issue) of immediately removing known threats via an online lookup gets approved.
Apologies for any confusion that I caused, I'll be more awake next time I post ! 😉
Hi cavehomme
Not at all, and no need to apologise as you have quite eloquently raised and discussed on a point that is, I suspect, more of a concern to many users than they might want to admit.
I for one would much prefer to be able to control what is allowed outbound from within WSA as was possible under Windows 7, and I do believe that there is indeed a way of doing that as evidenced by a number of standalone apps that are effectively WIndows Firewall 'helpers'. I have often asked myself as to why this sort of functionality could not be included in WSA, but I think that it is because to do so there would need to be either 2 version of WSA; one for Windows 7 & before leveraging the WFC functionality and another for WIndows 8 & above leveraging the Windows Firewall-related functionality that came in from Windows 8 onwards.
Clearly two versions would not be good or sensible and to have both functionality catered for in the one app would most likely increase the size of the app and therefore to some extent add 'bloat' to it.
I agree with you in terms of trusting WSA to handle outbound communications properly but it is a bit of a pain in the neck if one does in fact inadvertently block something that one later wants to allow and as fare as I know (and anyone who knows differently please step in here) the only way to resolve that issue is to uninstall WSA and then clean re-install it.
Anyway, I will be intrigued to see what this debates sparks off. ;)
Regards, Baldrick
Not at all, and no need to apologise as you have quite eloquently raised and discussed on a point that is, I suspect, more of a concern to many users than they might want to admit.
I for one would much prefer to be able to control what is allowed outbound from within WSA as was possible under Windows 7, and I do believe that there is indeed a way of doing that as evidenced by a number of standalone apps that are effectively WIndows Firewall 'helpers'. I have often asked myself as to why this sort of functionality could not be included in WSA, but I think that it is because to do so there would need to be either 2 version of WSA; one for Windows 7 & before leveraging the WFC functionality and another for WIndows 8 & above leveraging the Windows Firewall-related functionality that came in from Windows 8 onwards.
Clearly two versions would not be good or sensible and to have both functionality catered for in the one app would most likely increase the size of the app and therefore to some extent add 'bloat' to it.
I agree with you in terms of trusting WSA to handle outbound communications properly but it is a bit of a pain in the neck if one does in fact inadvertently block something that one later wants to allow and as fare as I know (and anyone who knows differently please step in here) the only way to resolve that issue is to uninstall WSA and then clean re-install it.
Anyway, I will be intrigued to see what this debates sparks off. ;)
Regards, Baldrick
I don't have much to contribute to this discussion but I have always felt that there is a lot of confusion regarding this issue.
It seems that since the introduction of Windows 8 when the ability to adjust the firewall settings in WSA was eliminated, the confusion started when users upgraded from Win7 (or earlier) and hasn't been helped by the fact that the online user guide still refers to the firewall settings available in Win7. Many of the recent upgraders to Win10 have become aware of this change and I do feel that WSA need to address this matter one way or the other.
It seems that since the introduction of Windows 8 when the ability to adjust the firewall settings in WSA was eliminated, the confusion started when users upgraded from Win7 (or earlier) and hasn't been helped by the fact that the online user guide still refers to the firewall settings available in Win7. Many of the recent upgraders to Win10 have become aware of this change and I do feel that WSA need to address this matter one way or the other.
I'm just saying Webroot could but they would be using the same API's built in Windows 8 and 10 as all other Firewalls have to as well. I would like to see the Granular control back but I don't think it's a priority for Webroot.
As I posted here: https://community.webroot.com/t5/Webroot-SecureAnywhere-Antivirus/No-firewall-settings-for-WRSA-AV-on-Windows-10/m-p/239337#M23002
Daniel
As I posted here: https://community.webroot.com/t5/Webroot-SecureAnywhere-Antivirus/No-firewall-settings-for-WRSA-AV-on-Windows-10/m-p/239337#M23002
Daniel
Completely agree, Daniel...I suspect that given the differences between what is available in Windows 7 and subsequant versions of Windows it is just not a very important topic at the moment in terms of the WSA road map...more is the pity as I thinkthat it is an area where an improvement would be welcomed by many user.
I think that fundamentally it comes down to an issue of trust. We don't necessarily need lots of drill-down options to control things if we fundamentally trust 100% the Webroot team.@ wrote:
Completely agree, Daniel...I suspect that given the differences between what is available in Windows 7 and subsequant versions of Windows it is just not a very important topic at the moment in terms of the WSA road map...more is the pity as I thinkthat it is an area where an improvement would be welcomed by many user.
But in my tests this weekend I'm now really sitting on the fence on the trust issue. I downloaded 10 attachments from the past week in my spam folder with WRSA enabled and not a single squeak from WRSA. So I then scanned each file, again not a squeak. I then uploaded all of them to Virustotal and indeed they were all malware, but typically only 50% of AV softwares detected them as being malicious.
Interestingly ALL of the sample were identified as malware by Windows Defender. So guess what? I've now fallen back to WD because I simply trust it more....I find that difficult to say and accept, but based on not only my test, but also AV Test and AV Comparatives they are now ranking WD at 95% or above detection rates.
To detect the other 5% and for secure banking, I would love to use WRSA in the same way that MS Security Essentials and WRSA can co-exist on Windows 7, but it's impossible on Windows 10 because WD is switched off when Windows detects WRSA as full AV solution and not treated as just an extra layer of security.
So now to get approaching 100% malware coverage I am reverting to either Malwarebytes Premium which DOES work as an extra layer of security on top of WD, or possibly Spyshelter or Zemana, but they are taking me back to the horrible days of chatty HIPS alerts even for trusted processes and applications, ouch!
Bottom line is that I really want to make WRSA work, but due to the issues I've noticed plus the fact that as a workaround I can't run WD + WRSA as the extra layer, I am being forced by Webroot design policy to look to alternative solutions. I really want to keep giving my money to Webroot, but they need to wake up and deal with some of these issue. I'm not being arrogant but I guess that for each one person like me there might be a few hundred or even thousands thinking and doing the same, just quietly in the background without sharing their experiences or frustrations on this forum.
Hi cavehomme
I think that you may have failed to understand how WSA is designed to work; the principle which is alien to the more traditional view of scanning everything, reporting everything that is malicious and then removing it. WSA works very differently by focusing it's resource in watching for and dealing effectively with ACTIVE malware, i.e., when a malware payload attempts to execute WSA jumps on it and nails it.
After all, a piece of malware that is not active is just another piece of software and does no harm, so why waste precious resources on it UNTIL it tries to activate.
That is how WSA works...and as you say it is a matter of some trust as to whether one is prepared to put ones faith in such a non traditional approach. But let me speak from personal experience...I have used WSA, every since it was introduced (which was shortly after it acquired Prevx, and I had been using Prevx prior to the acquisition), I have been attacked a small number of times and in every single case WSA has protected me completely.
Now nothing is 100%, not even WSA, but I personally would not use anything else as my primary line of defence against malware.
Not sure if that helps but just wanted to share with you.
Regards, Baldrick
I think that you may have failed to understand how WSA is designed to work; the principle which is alien to the more traditional view of scanning everything, reporting everything that is malicious and then removing it. WSA works very differently by focusing it's resource in watching for and dealing effectively with ACTIVE malware, i.e., when a malware payload attempts to execute WSA jumps on it and nails it.
After all, a piece of malware that is not active is just another piece of software and does no harm, so why waste precious resources on it UNTIL it tries to activate.
That is how WSA works...and as you say it is a matter of some trust as to whether one is prepared to put ones faith in such a non traditional approach. But let me speak from personal experience...I have used WSA, every since it was introduced (which was shortly after it acquired Prevx, and I had been using Prevx prior to the acquisition), I have been attacked a small number of times and in every single case WSA has protected me completely.
Now nothing is 100%, not even WSA, but I personally would not use anything else as my primary line of defence against malware.
Not sure if that helps but just wanted to share with you.
Regards, Baldrick
To understand how WSA works this thread from Kit is awesome: https://community.webroot.com/t5/Webroot-SecureAnywhere-Antivirus/Scanning-PC-suspiciously-fast/m-p/6636#M215 as well these videos:
Daniel
Daniel
Thanks for sharing Baldrick.@ wrote:
Hi cavehomme
I think that you may have failed to understand how WSA is designed to work; the principle which is alien to the more traditional view of scanning everything, reporting everything that is malicious and then removing it. WSA works very differently by focusing it's resource in watching for and dealing effectively with ACTIVE malware, i.e., when a malware payload attempts to execute WSA jumps on it and nails it.
After all, a piece of malware that is not active is just another piece of software and does no harm, so why waste precious resources on it UNTIL it tries to activate.
That is how WSA works...and as you say it is a matter of some trust as to whether one is prepared to put ones faith in such a non traditional approach. But let me speak from personal experience...I have used WSA, every since it was introduced (which was shortly after it acquired Prevx, and I had been using Prevx prior to the acquisition), I have been attacked a small number of times and in every single case WSA has protected me completely.
Now nothing is 100%, not even WSA, but I personally would not use anything else as my primary line of defence against malware.
Not sure if that helps but just wanted to share with you.
Regards, Baldrick
I've been using the software since it was Prevx and I do know the approach to malware detection, however, when you have a pieces of malware sitting on your drive AND there is the option in Explorer to scan those files for malware, which to me suggests the more traditional approach to scanning and detection for at least that function, but then it fails to detect any of 10 malware samples from the past week, unlike 50% or more of the 40+ Virustotal scanners, then my trust wobbles severely.
Put another way, if WRSA was only about active malware detection then it would not, I guess, scan passive files being downloaded nor provide the option to scan passive files sitting on the hard drive. So I conclude that it is menat to do both active and passive, with the latter being by cloud lookup therefore not creating bloat to the application. The application then must have complex algorithms which monitor active malware and jump on it and roll-back changes if needed.
In Win 7 having WRSA (or Prevx) hovdering over MS SE and pouncing whenever it slipped up was great, but it's not allowing that in Windows 10. To rely on WRSA when the passive detection component failed 10/10 times and then to trust it to actually then kick into action 10/10 times if I activated that malware...well, as I said, it's a trust-step too far at the moment considering I saw all those failures. I do however respect yours and others choices. Anyway, WRSA remains installed on 4 out of 5 less critical PCs, just not my main one for business. :)
Cheers,
Cavehomme
Hi cavehomme
WSA has not failed to detect those 10 elements of malware it has just not because they are of no consequence or no threat to your system...that is all. It is a false sens of security when one has a more traditional AV or IS app scan ones system, declare it has found 100 threats and either quarantined and/or deleted them. That is all well and good but if none of them were goingt o cause any damage then what is the point...a false sense of security.
Personally, I think that detecting & dealing with active malware consisently and throughly, as WSA does, is far more important than the more traditional approach. And it gets worse, when the traditional AVs & ISs include cookies in their threat tally.
Of course, it is horses for courses and one must do what one thinks is for the best. So good luck to you in your search for something better than WSA...unfortuantely I do not think that will find it.
Regards, Baldrick
WSA has not failed to detect those 10 elements of malware it has just not because they are of no consequence or no threat to your system...that is all. It is a false sens of security when one has a more traditional AV or IS app scan ones system, declare it has found 100 threats and either quarantined and/or deleted them. That is all well and good but if none of them were goingt o cause any damage then what is the point...a false sense of security.
Personally, I think that detecting & dealing with active malware consisently and throughly, as WSA does, is far more important than the more traditional approach. And it gets worse, when the traditional AVs & ISs include cookies in their threat tally.
Of course, it is horses for courses and one must do what one thinks is for the best. So good luck to you in your search for something better than WSA...unfortuantely I do not think that will find it.
Regards, Baldrick
Now that this thread has broadened out into a discussion of WSA's scanning and file detection methodology, I find I have a couple more comments.
The regular deep scan that WSA undertakes looks at those files that are "are running, definitely will run, or are likely to run".
In my case that is somewhere around 30,000 files. If malware is found, then the file is quarantined and marked for removal.
The 10 files that ? downloaded into his spam folder and then scanned with WSA via a right mouse click, were not marked as malicious by WSA but were by 50% of the AVs on Virus Total. This suggests to me that the files were more likely to be PUA/PUPs that we know WSA is not as aggressive at detecting and removing as some other AVs that always want to be seen to be doing something. Whatever they were, the fact that half of the traditional AV programs did not detect them, indicates that they were unlikely to be malicious in the true sense.
Like ?, I also like to have a second opinion and user a well known free scanner every few days. This scan checks around 350,000 files (65 GB) and since I have been running WSA, has never found anything.
So to ?, I would just like to say that I do not believe that you need to have Windows Defender running on your system as well as WSA. If you use WSA as your main AV and do occasional full scans with a second opinion scanner, you get the best of both worlds - a very light resource real-time AV in WSA and the reassurance that if any malicious files are lurking in unlikely places on your hard drive, they will be picked up by the second opinion full scanner.
I hope this is of assistance ? but if I am off the mark with any of the above, I would be grateful of feedback.
Regards
Nemo
The regular deep scan that WSA undertakes looks at those files that are "are running, definitely will run, or are likely to run".
In my case that is somewhere around 30,000 files. If malware is found, then the file is quarantined and marked for removal.
The 10 files that ? downloaded into his spam folder and then scanned with WSA via a right mouse click, were not marked as malicious by WSA but were by 50% of the AVs on Virus Total. This suggests to me that the files were more likely to be PUA/PUPs that we know WSA is not as aggressive at detecting and removing as some other AVs that always want to be seen to be doing something. Whatever they were, the fact that half of the traditional AV programs did not detect them, indicates that they were unlikely to be malicious in the true sense.
Like ?, I also like to have a second opinion and user a well known free scanner every few days. This scan checks around 350,000 files (65 GB) and since I have been running WSA, has never found anything.
So to ?, I would just like to say that I do not believe that you need to have Windows Defender running on your system as well as WSA. If you use WSA as your main AV and do occasional full scans with a second opinion scanner, you get the best of both worlds - a very light resource real-time AV in WSA and the reassurance that if any malicious files are lurking in unlikely places on your hard drive, they will be picked up by the second opinion full scanner.
I hope this is of assistance ? but if I am off the mark with any of the above, I would be grateful of feedback.
Regards
Nemo
@ wrote:
Now that this thread has broadened out into a discussion of WSA's scanning and file detection methodology, I find I have a couple more comments.
The regular deep scan that WSA undertakes looks at those files that are "are running, definitely will run, or are likely to run".
In my case that is somewhere around 30,000 files. If malware is found, then the file is quarantined and marked for removal.
The 10 files that@ downloaded into his spam folder and then scanned with WSA via a right mouse click, were not marked as malicious by WSA but were by 50% of the AVs on Virus Total. This suggests to me that the files were more likely to be PUA/PUPs that we know WSA is not as aggressive at detecting and removing as some other AVs that always want to be seen to be doing something. Whatever they were, the fact that half of the traditional AV programs did not detect them, indicates that they were unlikely to be malicious in the true sense.
Like@ , I also like to have a second opinion and user a well known free scanner every few days. This scan checks around 350,000 files (65 GB) and since I have been running WSA, has never found anything.
So to@ , I would just like to say that I do not believe that you need to have Windows Defender running on your system as well as WSA. If you use WSA as your main AV and do occasional full scans with a second opinion scanner, you get the best of both worlds - a very light resource real-time AV in WSA and the reassurance that if any malicious files are lurking in unlikely places on your hard drive, they will be picked up by the second opinion full scanner.
I hope this is of assistance@ but if I am off the mark with any of the above, I would be grateful of feedback.
Regards
Nemo
Thanks for the suggestions Nemo, I'm essentially actually doing what you suggest on the other 4 PCs which are all Windows 7s.
Regarding the 10 malware samples, they were definitely not PUPs, they were identified as various Trojans as well as a couple of Macro viruses. That's why I really was surprised that a random sample of 10 from the past week would not trigger an alert on manual scan; that's the whole purpose surely of a manual scan since the malware is not active at that point. Otherwise, Webroot should just remove this feature and rely 100% on pouncing on active malware ;)
Anyway, apart from beig a bit confused now about Webroots approach, I continue to stick with them for most of my protection, at least on Widows 7 since it's combined with the extra layer of security of having MSE.
Thanks for the feedback caveman. I also use Win 7 but was interested to hear that you cannot run WD with WSA on W10.
I am somewhat confused by these 10 sample files that you downloaded. You say that they were identified as Trojans or viruses but that half of the VirusTotal AVs gave them a clean bill of health, as did WSA. This suggests to me that they cannot be particularly malicious or surely they would be detected by all the AVs.
Anyway, if nothing else, this thread has provided a good summary of how Webroot works!
I am somewhat confused by these 10 sample files that you downloaded. You say that they were identified as Trojans or viruses but that half of the VirusTotal AVs gave them a clean bill of health, as did WSA. This suggests to me that they cannot be particularly malicious or surely they would be detected by all the AVs.
Anyway, if nothing else, this thread has provided a good summary of how Webroot works!
Nemo, here is just the most recent sample of those 10 malwares, doesn't look like a PUP to me, just a nasty JS trojan downloader. As to why so many companies would not detect it, well, I feel sorry for their users if they got hit with this!@ wrote:
Thanks for the feedback caveman. I also use Win 7 but was interested to hear that you cannot run WD with WSA on W10.
I am somewhat confused by these 10 sample files that you downloaded. You say that they were identified as Trojans or viruses but that half of the VirusTotal AVs gave them a clean bill of health, as did WSA. This suggests to me that they cannot be particularly malicious or surely they would be detected by all the AVs.
Anyway, if nothing else, this thread has provided a good summary of how Webroot works!
https://www.virustotal.com/en/file/be6dd0157cd7ca8bbff9137b539e0def4d3ab9dfd77bfe2e37b6ded578489d75/analysis/1456152535/
Here is a description, as to what it does...
http://www.certego.net/en/news/italian-spam-campaigns-using-js-nemucod-downloader/
Hope this helps.
Thanks caveman - that is interesting.
I see that it is a Trojan downloader and was not picked up by many of the major AVs out there. Presumably they, like Webroot, consider it benign until it is activated when they would spring into action.
It would be interesting if we could hear directly from a member of the Webroot team on this.
EDIT
Having had a further look at this it still seems to me that this file could be considered to be a PUA/PUP since its purpose is to "download and install other programs onto your PC without your consent, including other malware" (per MS). Not saying I would like it residing on my PC, I wouldn't, but it would be harmless until activated. At which point WSA would kick in. Still it is interesting to see that WSA and many of the other big boys do not detect it.
I see that it is a Trojan downloader and was not picked up by many of the major AVs out there. Presumably they, like Webroot, consider it benign until it is activated when they would spring into action.
It would be interesting if we could hear directly from a member of the Webroot team on this.
EDIT
Having had a further look at this it still seems to me that this file could be considered to be a PUA/PUP since its purpose is to "download and install other programs onto your PC without your consent, including other malware" (per MS). Not saying I would like it residing on my PC, I wouldn't, but it would be harmless until activated. At which point WSA would kick in. Still it is interesting to see that WSA and many of the other big boys do not detect it.
@ wrote:
Thanks caveman - that is interesting.
I see that it is a Trojan downloader and was not picked up by many of the major AVs out there. Presumably they, like Webroot, consider it benign until it is activated when they would spring into action.
It would be interesting if we could hear directly from a member of the Webroot team on this.
EDIT
Having had a further look at this it still seems to me that this file could be considered to be a PUA/PUP since its purpose is to "download and install other programs onto your PC without your consent, including other malware" (per MS). Not saying I would like it residing on my PC, I wouldn't, but it would be harmless until activated. At which point WSA would kick in. Still it is interesting to see that WSA and many of the other big boys do not detect it.
Yes I'd be interested to hear more.
As far as classification is concerned, if ESET and other respected companies classify the malware as a trojan, that's scary enough for me :)
I think a common thread in non-detection across those samples are Comodo and Symantec. The others are smaller or regional companies. Most of the other big boys and girls managed to detect them. I know from experience that Comodo has poor detection but they work on the principle of "default deny", so anything that is not whitelisted is blocked; not the most user friendly nor necessarily effective solution.
Anyway, we've gone slightly off track a bit from the original purpose of the thread, but I hope that someone from Webroot can throw more light on why these are ignored by WRSA, here are just 3:
https://www.virustotal.com/en/file/be6dd0157cd7ca8bbff9137b539e0def4d3ab9dfd77bfe2e37b6ded578489d75/analysis/1456152535/
https://www.virustotal.com/en/file/212897bf0735fd28f20c6092adcd4a1388d55922c74575a9177b255e01c454de/analysis/1456159749/
https://www.virustotal.com/en/file/56948e255c7f1cc28c445ea7d0230f56ed3073701b7dd61c4fd3a67310d6b2b8/analysis/1456160192/
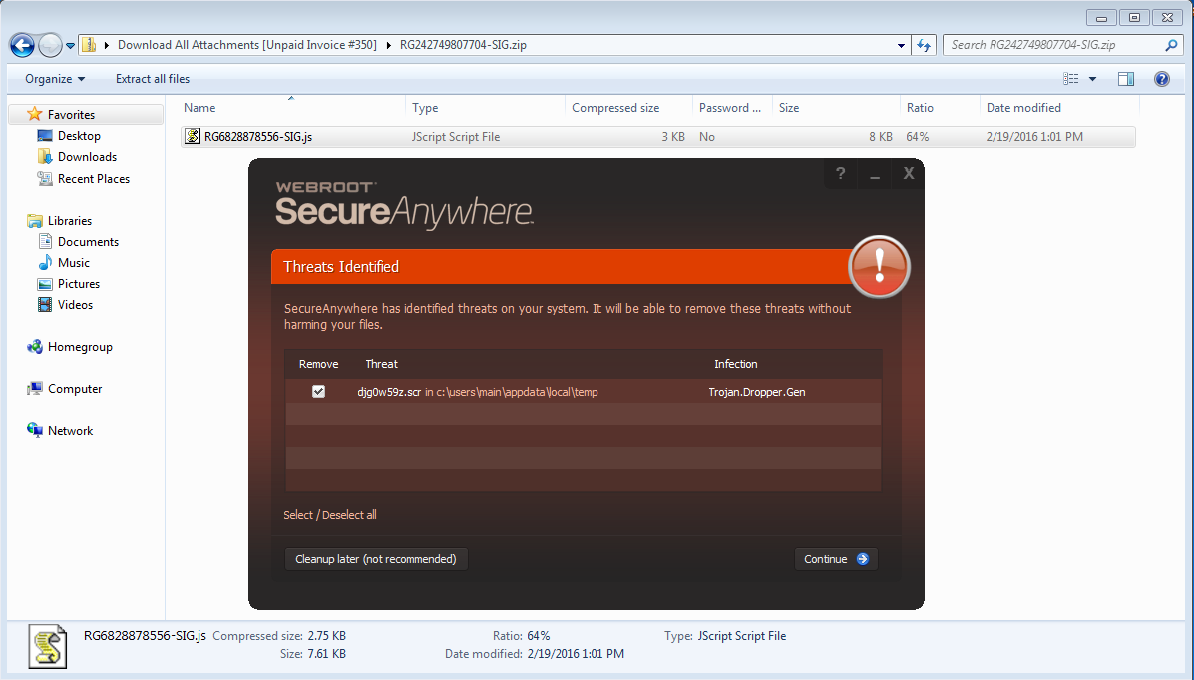
I just had a look at this. This is a .zip file that contains another .zip file that contains the malicious .js file. If you were to download the .zip attachment from the email containing it, unzip that file, then extract and run .js file from the .zip file that is cointained within the attachment, the downloaded payload will be blocked:@ wrote:
Nemo, here is just the most recent sample of those 10 malwares, doesn't look like a PUP to me, just a nasty JS trojan downloader. As to why so many companies would not detect it, well, I feel sorry for their users if they got hit with this!@ wrote:
Thanks for the feedback caveman. I also use Win 7 but was interested to hear that you cannot run WD with WSA on W10.
I am somewhat confused by these 10 sample files that you downloaded. You say that they were identified as Trojans or viruses but that half of the VirusTotal AVs gave them a clean bill of health, as did WSA. This suggests to me that they cannot be particularly malicious or surely they would be detected by all the AVs.
Anyway, if nothing else, this thread has provided a good summary of how Webroot works!
https://www.virustotal.com/en/file/be6dd0157cd7ca8bbff9137b539e0def4d3ab9dfd77bfe2e37b6ded578489d75/analysis/1456152535/
Here is a description, as to what it does...
http://www.certego.net/en/news/italian-spam-campaigns-using-js-nemucod-downloader/
Hope this helps.
I'll have a look at the other samples that you have listed, but I'm guessing we'll block the paylod on those too. If not, I'll update our detections for them.
-Dan
Many thanks Dan for your input. Assuming all samples behave similarly, then we it looks as though we are quite safe - and have been all along! 😃
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.