Why can't Webroot detect malicious Word DOCs?
I just got this doc in a spear phish e-mail and Webroot totally failed to identify the threat. This particular attack is 8 years old
First Seen In The Wild: 2010-11-20 23:29:33
According to Virustotal the reason is that "Webroot: Unable to process file type" which suggests that Webroot can't detect ANY malicous word doc. That's pretty scary since we know it is a very common attack vector.
Is work being done on this? 8 years later can we get some protection?
https://www.virustotal.com/#/file/bc5e2cef534da102cd8b025ad4b404cf8cd832bced80c99918714bf3e3af3a13/details
Page 1 / 1
The only suggestion I can add is to Submit a Support Ticket with the info you supplied and ask them why and please let us know what they say as we would like to know as well! The Community Staff are now gone and will not be back till Monday but support in open 24/7/365.
Thanks,
Thanks,
I did make a support ticket. The official response is:
"This macro-enabled word document runs powershell to download and execute a malicious payload for the 'Emotet' banking trojan. While we do not yet detect the document itself, we would detect the execution of the payload in real time, and the hash for this payload has already been determined as malicious in our threat database."
Which sounds like I would have been protected if the VBA code had ran. Furthermore:
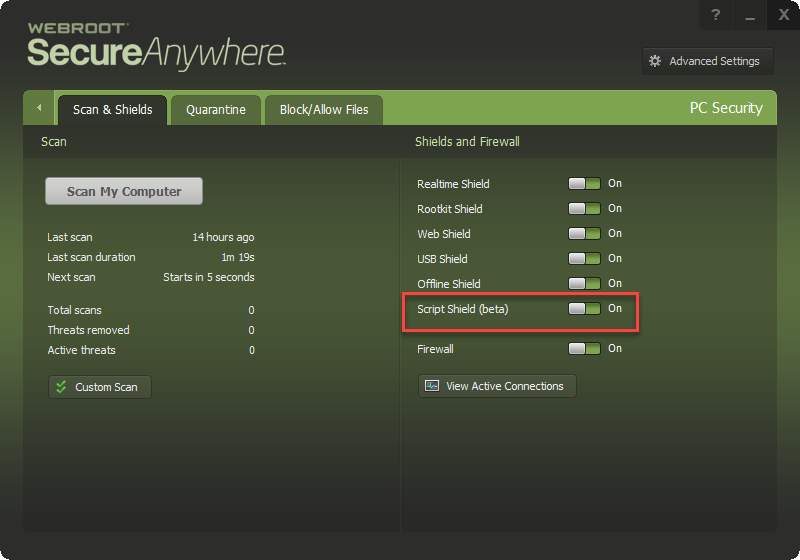
"We are currently beta testing our 'script shield' addition to our protective coverage, which will be better at detecting non-PE vectors such as .js files, powershell scripts, etc. Once that rolls out we should be able to stop the process at the powershell script execution (using this infection as an example), before it could connect and download the actual payload."
Which sounds like they are working on a more layered approach to blocking these attacks, as the payload will change over time.
"This macro-enabled word document runs powershell to download and execute a malicious payload for the 'Emotet' banking trojan. While we do not yet detect the document itself, we would detect the execution of the payload in real time, and the hash for this payload has already been determined as malicious in our threat database."
Which sounds like I would have been protected if the VBA code had ran. Furthermore:
"We are currently beta testing our 'script shield' addition to our protective coverage, which will be better at detecting non-PE vectors such as .js files, powershell scripts, etc. Once that rolls out we should be able to stop the process at the powershell script execution (using this infection as an example), before it could connect and download the actual payload."
Which sounds like they are working on a more layered approach to blocking these attacks, as the payload will change over time.
Thanks for the info from support! Yes we are Beta Testing the new Script Shield see picture below:@ wrote:
I did make a support ticket. The official response is:
"This macro-enabled word document runs powershell to download and execute a malicious payload for the 'Emotet' banking trojan. While we do not yet detect the document itself, we would detect the execution of the payload in real time, and the hash for this payload has already been determined as malicious in our threat database."
Which sounds like I would have been protected if the VBA code had ran. Furthermore:
"We are currently beta testing our 'script shield' addition to our protective coverage, which will be better at detecting non-PE vectors such as .js files, powershell scripts, etc. Once that rolls out we should be able to stop the process at the powershell script execution (using this infection as an example), before it could connect and download the actual payload."
Which sounds like they are working on a more layered approach to blocking these attacks, as the payload will change over time.
Thank you @ for posting Supports reply. Good info. 😉
@ wrote:
So , let's make this clear:
The malware is 8 years old, detected by the free MSE , but not Webroot, which is still "working" on some sort of detection...
Remind me again, why should I pay $30 /year for Webroot, when the free MSE performs better?
Just curios...
From the post above...
"While we do not yet detect the document itself, we would detect the execution of the payload in real time, and the hash for this payload has already been determined as malicious in our threat database."
Had the payload been executed, Webroot would've jumped on it.
So what's your point? (other than to start crap, as usual).
Just curious.
Hi total1, You have already answered your own question. It would be downright bonkers of you to pay for something you didnt feel was going to do you any good. Now, I dont think you are 100% bonkers but Ill have to read some more of your postings to make up my mind.
When time permits, will you post up some more comments so we can determine once and for all if you really are 100% bonkers ?
When time permits, will you post up some more comments so we can determine once and for all if you really are 100% bonkers ?
Then don't. There is nobody here forcing you to, I am sure you will enjoy MSE.@ wrote:
Sorry but I do not intend to spend neither money nor time with an antivirus which refuses to participate in any third party evaluation (AV Comparatives, AV Test) and has a detection rate inferior to MSE which is the basic antivirus of all times.
@ wrote:
Sorry but I do not intend to spend neither money nor time with an antivirus which refuses to participate in any third party evaluation ...Yet, you’ll waste your and everyone else’s time here, on and off for years incidentally, to bi+ch and moan about a product you haven’t used in years?
Unbelievable.
Perfectly put.@ wrote:
Yet, you’ll waste your and everyone else’s time here, on and off for years incidentally, to bi+ch and moan about a product you haven’t used in years?
Unbelievable.
@ wrote:
Enjoing already for the last 3 YEARS.@ wrote:
Then don't. There is nobody here forcing you to, I am sure you will enjoy MSE.@ wrote:
Still have an unused Webroot license (3pc) in my account, never intend to use.
Greetings 2U total1, very much oblige you spending our valuable time and thereby confirming our suspicions.On a side note, did you know that the best time to go to the Dentist is 2:30 ?
Who gave Kudos to the SPAMBOT?
Some people just want to watch the world burn...
Some people just want to watch the world burn...
What do you expect when you come to a forum with a negative attitude? Hmm@ wrote:
Enjoing already for the last 3 YEARS.@ wrote:
Then don't. There is nobody here forcing you to, I am sure you will enjoy MSE.@ wrote:
Still have an unused Webroot license (3pc) in my account, never intend to use.
OK, I'll grant you that,@ wrote:
to agree each other and to give KUDOS each other in a fantasia world...
But the problem is, you are the biggest problem. OK, Webroot is complete rubbish. OK, all of us are Koolaid fantasists. And yet you are still here. Honestly, you must have a gigantic personal problem whatever it is, because although you've seen the light you can't move on. Here you still are, stuck with us same kooky cult fantasists. Please, do yourself a favour and do move on. Life is too precious to waste on idiots like us or on cr*p AV products like ours.
Fantastic! Move on 😃@ wrote:
Thank you for your eye-opener statement.@ wrote:
Life is too precious to waste on idiots like us or on cr*p AV products like ours.
I will follow your advice.
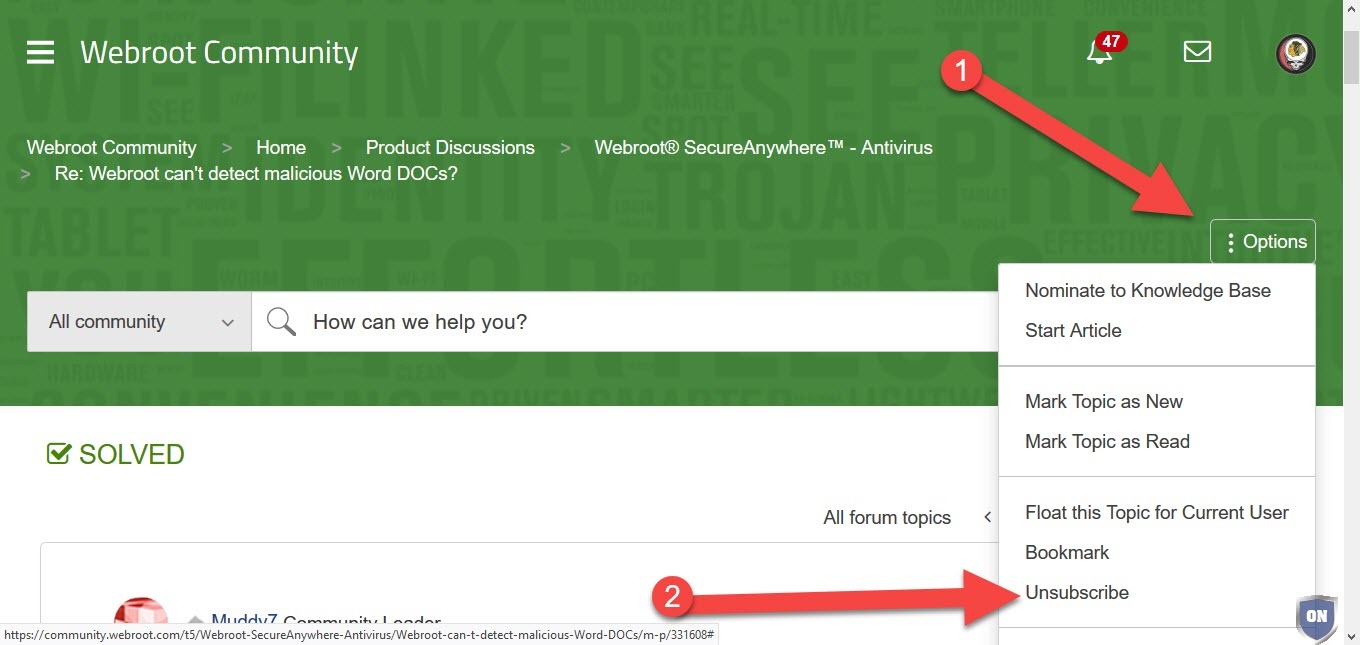
Are there any moderators on this forum? I marked my accepted answer a long time ago and I keep getting these e-mails about thread updates. This thread derailed and should have been locked by now. There is nothing more to be added here.
You are automatically subscribed to a thread once you participate. To unsubscribe, click the three dots ("Options") in the upper-right of the thread and select "unsubscribe".@ wrote:
Are there any moderators on this forum? I marked my accepted answer a long time ago and I keep getting these e-mails about thread updates. This thread derailed and should have been locked by now. There is nothing more to be added here.
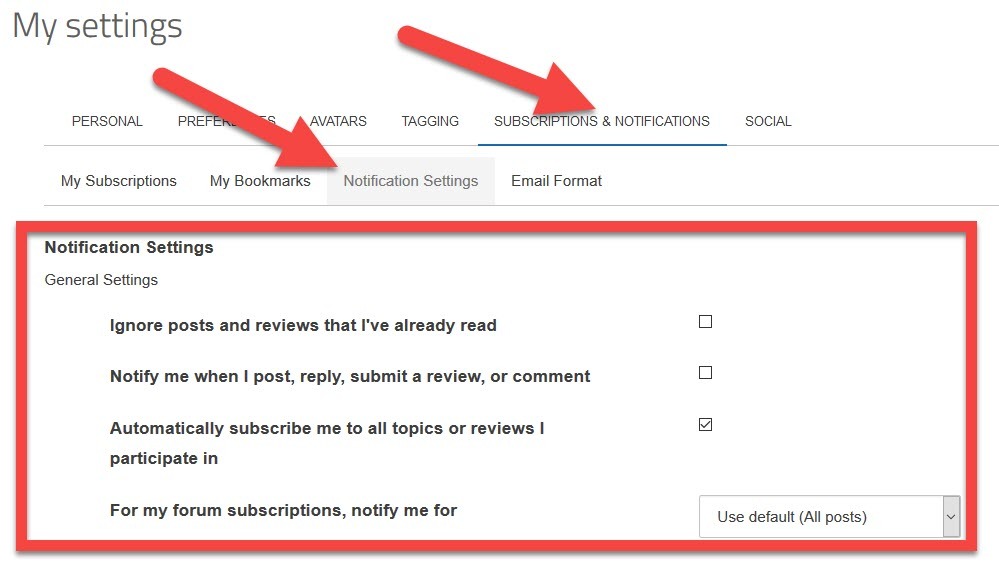
Also, these settings can be changed in your profile settings:
Hope this info helps. Also, they don't ever lock threads around here, though they should. 😉
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.