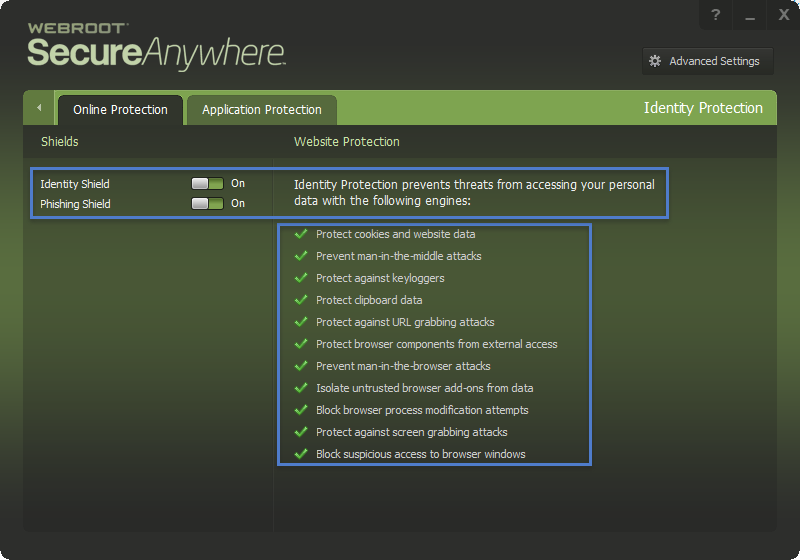
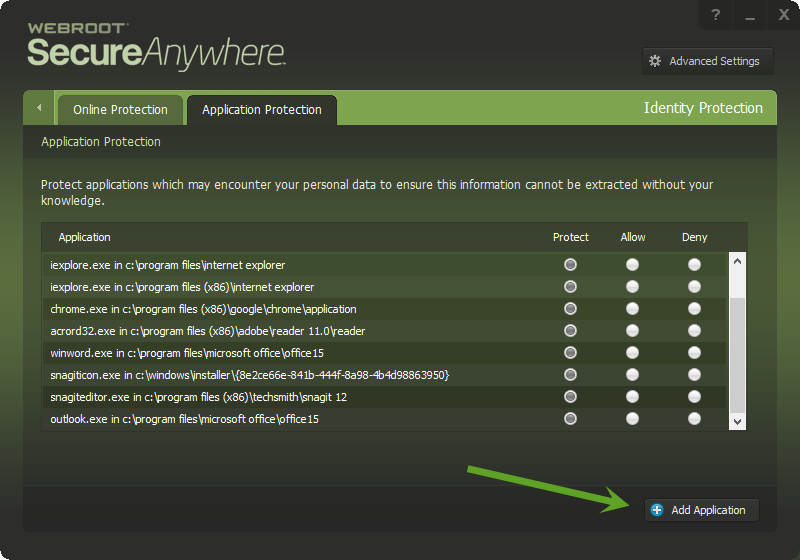
Re. this video by Webrooot: https://www.youtube.com/watch?v=uKMZ1Ukw_7I
Can you please confirm that this (unknown and undetected) keylogger would be automatically blocked from sending the captured keystrokes to a remote server? i.e. would the Webroot firewall component prompt me before allowing an unknown (as yet unverified) application from connecting outbound?
Thanks
PJ
Answer
If Webroot misses a virus can that virus connect to remote server and send my keystrokes?
Best answer by DanP
Hello PJCarmody,
To answer your questions...
- Is there a pop-up on Win 7? Wondering about false positives, whereby Unknown programs are silently blocked from accessing the Internet
You will see prompts when Unknown processes are trying to access the internet.
- From the video it looks like the Unknown keylogger is able to do what it wants, until and if it is becomes Known at which point if it consider Bad then it will be Blocked and all its activities up until that time will be reversed?
The keystroke logging would still be blocked. The changes made to the file system and registry are what would be reversed during rollback.
- >all keystrokes are protected by Webroot regardless of what a files determination is
- from what I can see this only applies to Protected Applications; ones have been pre-added to the list, or manually added later, correct?
The Protected Applications are not the only applications that are protected from keylogging.
-Dan
To answer your questions...
- Is there a pop-up on Win 7? Wondering about false positives, whereby Unknown programs are silently blocked from accessing the Internet
You will see prompts when Unknown processes are trying to access the internet.
- From the video it looks like the Unknown keylogger is able to do what it wants, until and if it is becomes Known at which point if it consider Bad then it will be Blocked and all its activities up until that time will be reversed?
The keystroke logging would still be blocked. The changes made to the file system and registry are what would be reversed during rollback.
- >all keystrokes are protected by Webroot regardless of what a files determination is
- from what I can see this only applies to Protected Applications; ones have been pre-added to the list, or manually added later, correct?
The Protected Applications are not the only applications that are protected from keylogging.
-Dan
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.