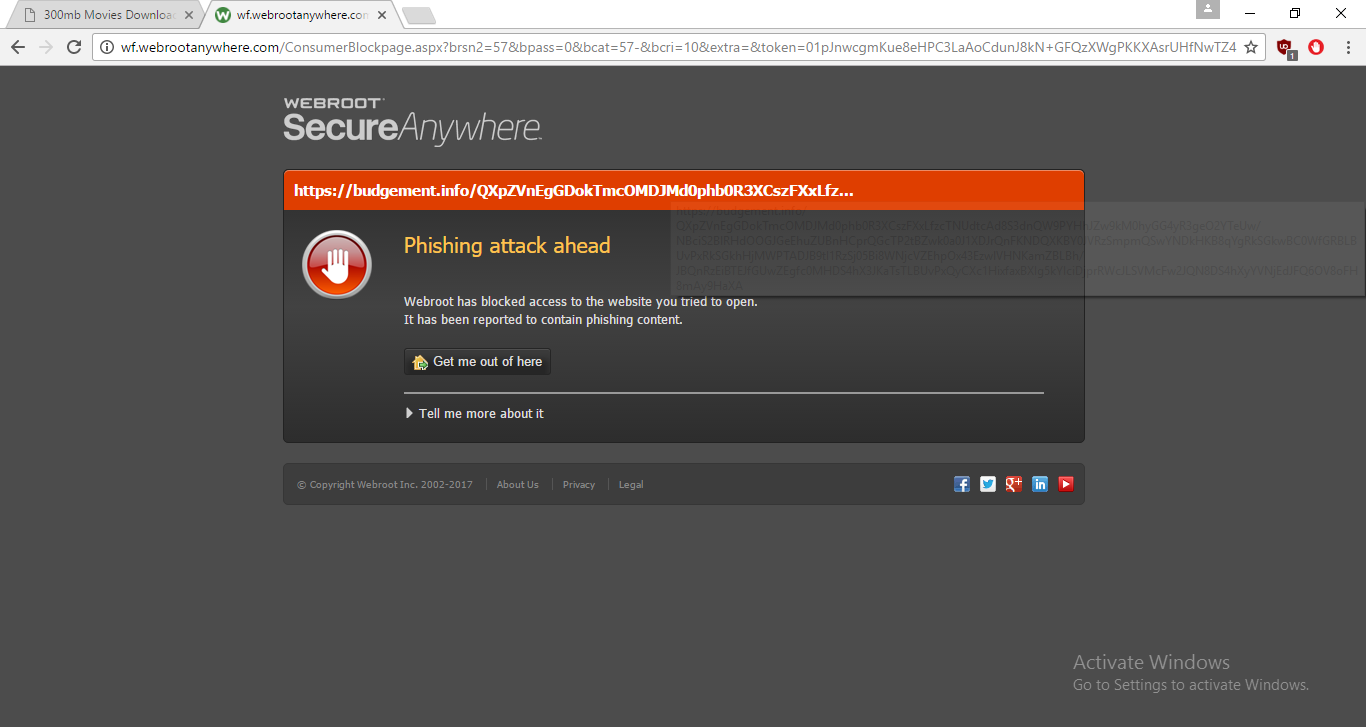
malicious attacked not got caught by webrrot in ie latest version...
i visit
https://www.300mbmoviess.com
you have too much malicious attack but this is isn't getting blocked
//
same is blocked in chrome
steps to produce
1. open ie with webroot extensions enabled....
2.go here
https://www.300mbmoviess.com
3.click anywhere in page
4.you will get malicious popup which is not getting blocked in ie but in chrome same is blocked
In ie webroot is unable to catch this....
can we have idea@webroot threat research team
Page 1 / 2
WSA may not have given the phishing attack warning under Edge (because there is currenlty no Web Threat Extension available) but when the payload attempted a download it was instantly dtected by WSA and quarantined.
So no issue here in terms of WSA protection.
And by the way, I hope that you are not indulging or reporting on previate malware testing activity as to do so is contrary to Community Guidelines...;)
Regards, Baldrick
So no issue here in terms of WSA protection.
And by the way, I hope that you are not indulging or reporting on previate malware testing activity as to do so is contrary to Community Guidelines...;)
Regards, Baldrick
HI samual91,
In addition to the info that Baldrick has posted.
I would recommend an Adblocker like the ones suggested below.
For Internet Explorer Ad Block Plus: https://adblockplus.org/
For Firefox uBlock Origin: https://addons.mozilla.org/en-US/firefox/addon/ublock-origin/?src=ss or Privacy Badger: https://addons.mozilla.org/en-us/firefox/addon/privacy-badger-firefox/
Google Chrome uBlock Origin: https://chrome.google.com/webstore/detail/ublock-origin/cjpalhdlnbpafiamejdnhcphjbkeiagm?hl=en or Privacy Badger: https://chrome.google.com/webstore/detail/privacy-badger/pkehgijcmpdhfbdbbnkijodmdjhbjlgp
I experienced no such popups on the site. ;)
BD
In addition to the info that Baldrick has posted.
I would recommend an Adblocker like the ones suggested below.
For Internet Explorer Ad Block Plus: https://adblockplus.org/
For Firefox uBlock Origin: https://addons.mozilla.org/en-US/firefox/addon/ublock-origin/?src=ss or Privacy Badger: https://addons.mozilla.org/en-us/firefox/addon/privacy-badger-firefox/
Google Chrome uBlock Origin: https://chrome.google.com/webstore/detail/ublock-origin/cjpalhdlnbpafiamejdnhcphjbkeiagm?hl=en or Privacy Badger: https://chrome.google.com/webstore/detail/privacy-badger/pkehgijcmpdhfbdbbnkijodmdjhbjlgp
I experienced no such popups on the site. ;)
BD
test yourself in your machine with intenet explorer and compare result with chrome
No issues here with IE...but then again my version of IE has the Web Filtering Extension installed & enabled. Have you checked to see if it is in your IE...;)
Baldrick
Baldrick
enabled
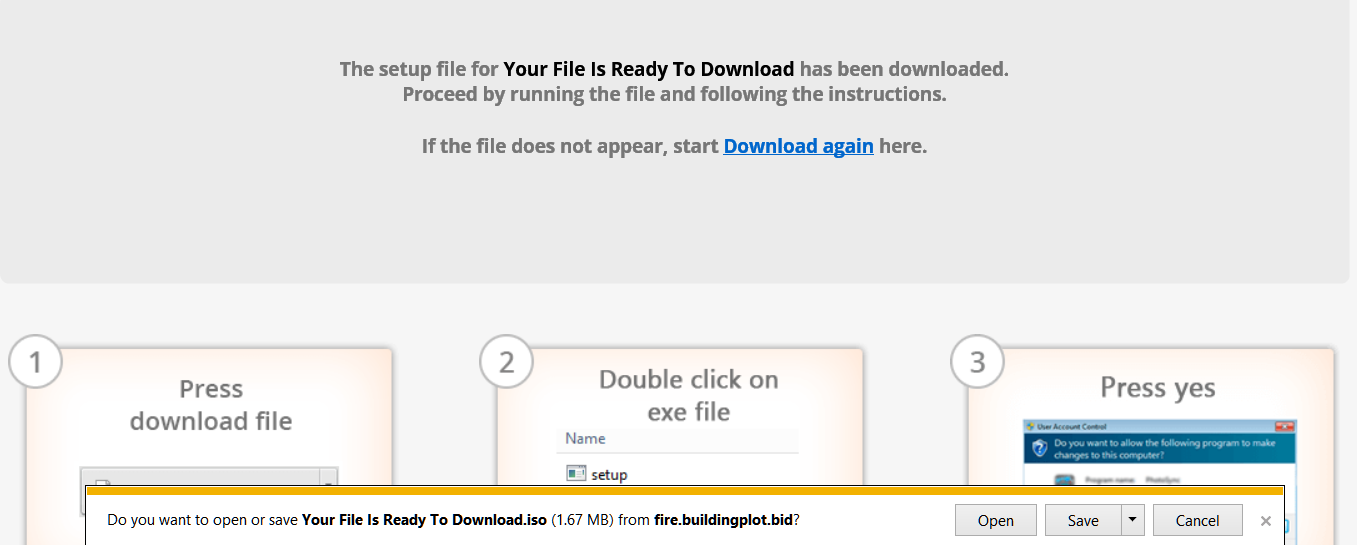
When I tested in IE the popup was blocked by IE's popup blocker, not ABP. I allowed it and the popup itself wasn't malicious either. It did prompt me to download a file, which I didn't do, but that was it.
BD
BD
Irrespective of whether the Web Threat Extension provides warning or not (it does nothing much more than provide the warnings) you are still 100% protected by WSA which will detect the malicious payload when it tries to run and will block/quarantine it, as it did when the page was access under Edge...so still really no worries.
Baldrick
Baldrick
Firefox and Chrome = page block@ wrote:
malicious attacked not got caught by webrrot in ie latest version...
i visit
https://www.300mbmoviess.com
you have too much malicious attack but this is isn't getting blocked
//
same is blocked in chrome
steps to produce
1. open ie with webroot extensions enabled....
2.go here
https://www.300mbmoviess.com
3.click anywhere in page
4.you will get malicious popup which is not getting blocked in ie but in chrome same is blocked
In ie webroot is unable to catch this....
can we have idea@webroot threat research team
Internet Explorer = no page block
I repeat...in the context of the OP's subject for the thread "webroot protection insufficient for internet explorer"...irrespective of whether the Web Threat Extension provides warning or not (it does nothing much more than provide the warnings) you are still 100% protected by WSA which will detect the malicious payload when it tries to run and will block/quarantine it.Therefore, IMHO, WSA provides more than sufficient protection for users who may be using IE...even for those that do not seem to have a working Web Filtering extension. Baldrick
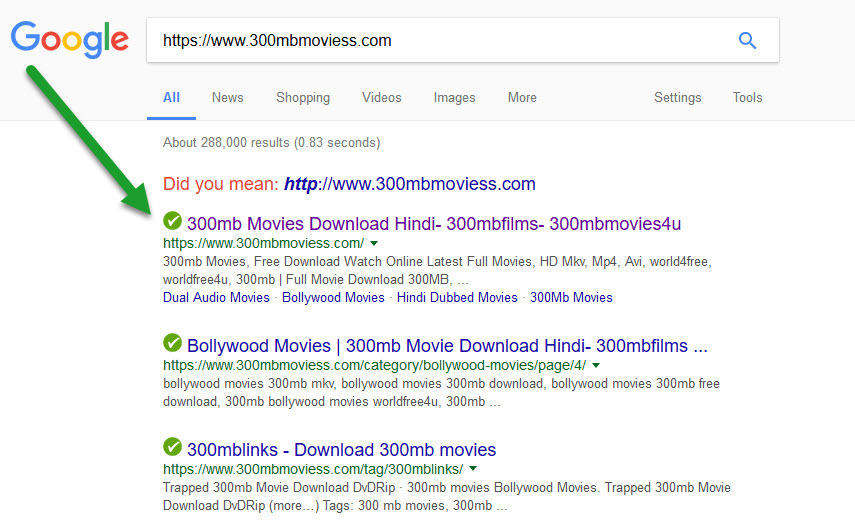
That's odd. I don't get a page block from Webroot at all in Firefox, either. It goes straight to the site. Here's the site in my Google search returns.
I don't know. There are obviously differences based on user's individual setups. But as Baldrick has stated. You're still protected from any malicious payload should anything try to execute. Personally, I would just use a different site as that one appears very problematic. I avoid any site that forces popups, popunders, etc. But that's just me. Everyone has there own preference and opinion. ;)
BD
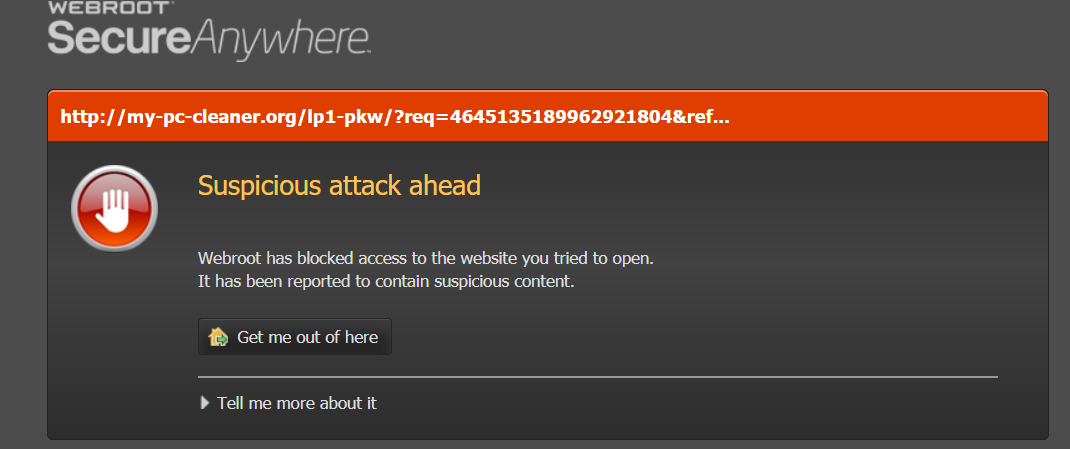
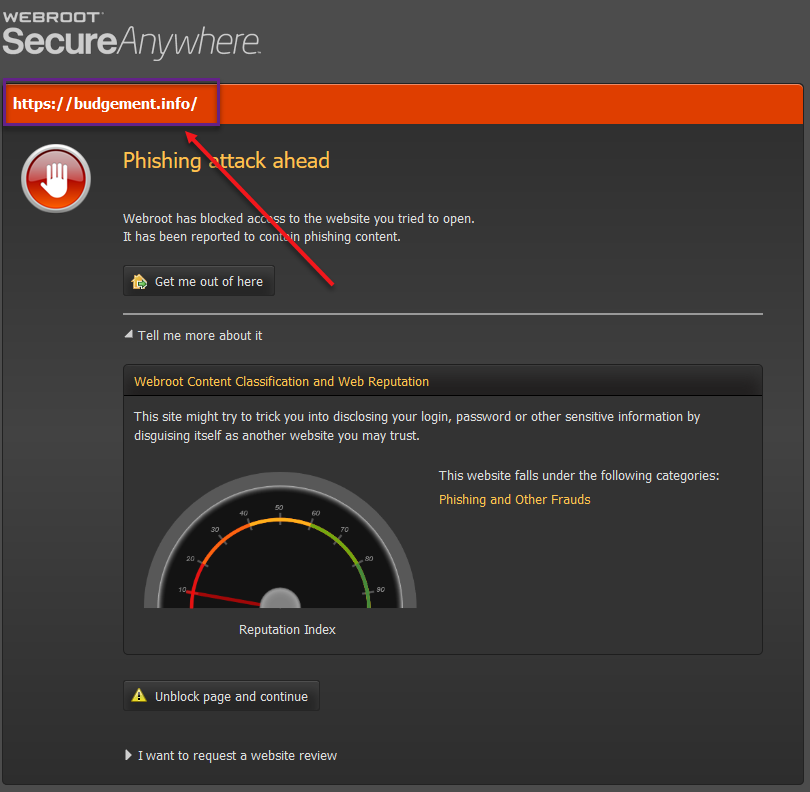
Someone please post the correct URL to the Blocked site! This is not the correct URL showing in the Blocked pages posted: https://www.300mbmoviess.com
@
03/29 21:37:40:693 2716 Info: UrlCat Ticks=157 Br= [{"URL":","BCRI":80,"ALCAT":0,"RTAP":0,"BLK":0,"REF":1]https://www.300mbmoviess.com/","CAT.CONF":["30.90","78.90"],"BCRI":80,"ALCAT":0,"RTAP":0,"BLK":0,"REF":1}]
03/29 21:37:42:087 2716 Info: OPERATION_PHRESHFISH Handle=00000C74 RESET
03/29 21:37:42:324 2716 Info: OPERATION_GETCONFIG Br=
03/29 21:37:42:324 2716 Info: Browser: Firefox
03/29 21:37:42:362 2716 Info: UrlCat Ticks=0 Br= [{"URL":","BCRI":80,"ALCAT":0,"RTAP":0,"CACHED":1,"BLK":0,"REF":1]https://www.300mbmoviess.com/","CAT.CONF":["30.90","78.90"],"BCRI":80,"ALCAT":0,"RTAP":0,"CACHED":1,"BLK":0,"REF":1}]
03/29 21:37:42:491 2716 Verbose: PhreshPhish to server request
03/29 21:37:42:753 2716 Info: PhreshPhish Score=1 Ticks=344 Phish=0 White=0 Url=https://www.300mbmoviess.com/
03/29 21:37:42:753 2716 Info: PHISH Br= [{"ISPHIS":0,"ISWHT":0,"SCORE":1}]
03/29 21:45:16:819 2716 Info: Browser: Firefox
03/29 21:45:17:877 2716 Info: OPERATION_PHRESHFISH Handle=00000C74 RESET
03/29 21:45:21:097 2716 Info: UrlCat Ticks=94 Br= [{"URL":","BCRI":10,"ALCAT":1,"RTAP":0,"BLK":1,"BLKREASON":57,"EXTRA":"","REF":1]https://budgement.info/","CAT.CONF":["57.70"],"BCRI":10,"ALCAT":1,"RTAP":0,"BLK":1,"BLKREASON":57,"EXTRA":"","REF":1}]
03/29 21:45:21:423 2716 Info: OPERATION_PHRESHFISH Handle=00000C74 RESET
03/29 21:37:40:693 2716 Info: UrlCat Ticks=157 Br= [{"URL":","BCRI":80,"ALCAT":0,"RTAP":0,"BLK":0,"REF":1]https://www.300mbmoviess.com/","CAT.CONF":["30.90","78.90"],"BCRI":80,"ALCAT":0,"RTAP":0,"BLK":0,"REF":1}]
03/29 21:37:42:087 2716 Info: OPERATION_PHRESHFISH Handle=00000C74 RESET
03/29 21:37:42:324 2716 Info: OPERATION_GETCONFIG Br=
03/29 21:37:42:324 2716 Info: Browser: Firefox
03/29 21:37:42:362 2716 Info: UrlCat Ticks=0 Br= [{"URL":","BCRI":80,"ALCAT":0,"RTAP":0,"CACHED":1,"BLK":0,"REF":1]https://www.300mbmoviess.com/","CAT.CONF":["30.90","78.90"],"BCRI":80,"ALCAT":0,"RTAP":0,"CACHED":1,"BLK":0,"REF":1}]
03/29 21:37:42:491 2716 Verbose: PhreshPhish to server request
03/29 21:37:42:753 2716 Info: PhreshPhish Score=1 Ticks=344 Phish=0 White=0 Url=https://www.300mbmoviess.com/
03/29 21:37:42:753 2716 Info: PHISH Br= [{"ISPHIS":0,"ISWHT":0,"SCORE":1}]
03/29 21:45:16:819 2716 Info: Browser: Firefox
03/29 21:45:17:877 2716 Info: OPERATION_PHRESHFISH Handle=00000C74 RESET
03/29 21:45:21:097 2716 Info: UrlCat Ticks=94 Br= [{"URL":","BCRI":10,"ALCAT":1,"RTAP":0,"BLK":1,"BLKREASON":57,"EXTRA":"","REF":1]https://budgement.info/","CAT.CONF":["57.70"],"BCRI":10,"ALCAT":1,"RTAP":0,"BLK":1,"BLKREASON":57,"EXTRA":"","REF":1}]
03/29 21:45:21:423 2716 Info: OPERATION_PHRESHFISH Handle=00000C74 RESET
Well spotted eagle eyes! 😃
Hello again -
We have reviewed 300mbmoviess.com/ and have updated the site to a reputation score of 21 per your suggestion. This change is now published in the BrightCloud Service and is available in Database version 5.144.
Thanks again for your suggestion!
- Webroot BrightCloud Threat Intelligence Support
We have reviewed 300mbmoviess.com/ and have updated the site to a reputation score of 21 per your suggestion. This change is now published in the BrightCloud Service and is available in Database version 5.144.
Thanks again for your suggestion!
- Webroot BrightCloud Threat Intelligence Support
from opening post@ wrote:
That's odd. I don't get a page block from Webroot at all in Firefox, either. It goes straight to the site. Here's the site in my Google search returns.
I don't know. There are obviously differences based on user's individual setups. But as Baldrick has stated. You're still protected from any malicious payload should anything try to execute. Personally, I would just use a different site as that one appears very problematic. I avoid any site that forces popups, popunders, etc. But that's just me. Everyone has there own preference and opinion. ;)
BD
-----------------------------------------------------------
quote
steps to produce
1. open ie with webroot extensions enabled....
2.go here
https://www.300mbmoviess.com
3.click anywhere in page
4.you will get malicious popup which is not getting blocked in ie but in chrome same is blocked
--------------------------------
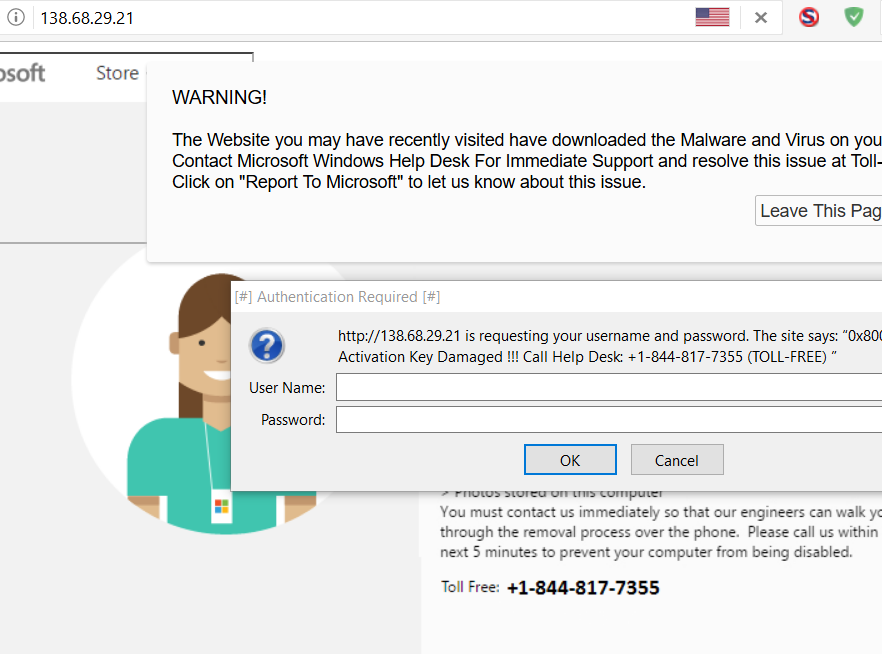
FWIW ~ I reproduced redirect and subsequent page block w Firefox and Chrome (yesterday) by clicking on open area in 300mbmovies page header.
(sorry about edits.....impaired vision)
myself want to clarify that malicious popup/phishing should be blocked by webroot in internet explorer as this was blocked in chrome/firefox
Please Submit a Support Ticket so they can get the said Website from you and they will look after it for you and see if there is an issue as to why it's not blocked in IE! Can you post the link so we can check it?@ wrote:
myself want to clarify that malicious popup/phishing should be blocked by webroot in internet explorer as this was blocked in chrome/firefox
Thanks,
Daniel 😉
We have tested the URL https://www.300mbmoviess.com/ on our VMs, the popup URLs change not only from browser to browser, but also each time you access the website again.
We are evaluating the risks of the popups not currently being under blocked categories, however we confirm that there is no discrepancy in behavior between browsers, the different behavior depends on the URL contained in the popup.
-Dan
We are evaluating the risks of the popups not currently being under blocked categories, however we confirm that there is no discrepancy in behavior between browsers, the different behavior depends on the URL contained in the popup.
-Dan
Thanks Dan!@ wrote:
We have tested the URL https://www.300mbmoviess.com/ on our VMs, the popup URLs change not only from browser to browser, but also each time you access the website again.
We are evaluating the risks of the popups not currently being under blocked categories, however we confirm that there is no discrepancy in behavior between browsers, the different behavior depends on the URL contained in the popup.
-Dan
Daniel 😉
webroot can have lookup here to update brightcloud...they have ransomware domain list too and update it according to virustotal
<url snipped as inappropriate>
<url snipped as inappropriate>
WSA has much more senors:@ wrote:
webroot can have lookup here to update brightcloud...they have ransomware domain list too and update it according to virustotal
<url snipped as inappropriate>
What is the point your trying to make? You just post pictures???? If your Malware testing we ask you not to posts topics on such things so please read this:@ wrote:
"From the Community Guidelines: https://community.webroot.com/t5/Announcements/Webroot-Community-Guidelines/td-p/2
No Private Testing Discussions.
"We do not condone private malware testing by end-users. This is never a good idea, and in some areas it's actually illegal. The whole point of antivirus software is to not get infected, and unfortunately when somebody sets a bad example, there will always be others who are influenced into following the same path. It's not something we want to allow to be encouraged."
The reality is that it requires a very talented professional to so this safely, otherwise there exists huge risks of damage not only to your own computer but also a risk of releasing the malware to others. The average user is simply not safe in attempting this, yet discussion regarding it would encourage others to try it, with potential disasterous results.
Think of it like a beginner PC tech working from home with no real training or experience. How often have we heard stories of a PC being brought to the 'kid next door' to be worked on with disastrous results? Plenty!
We always advise that general users never attempt hardware repair on their own due to the risks, and the same holds true here.
This Forum, provided by Webroot, is designed with the average user in mind, to help them with day to day problems using the software, just as many PC troubleshooting forums sponsored by the PC manufacturers do not go into the technical areas of hardware repair.
We therefore are asking you to remove any references regarding the testing of malware and refrain from doing so in the future. But we are also happy to answer any questions, that conform to these guidelines. If you have some specific details of malware tests that you wish to present and/or query with Webroot then this is best done directly rather than here, and can be accomplished by Opening a Support Ticket, which will most probably be passed to one of Webroot's professional Threat Researchers for review & progressing.
Thank you for your understanding and co-operation in this matter."
If you run into malicious URLs that are not blocked, you can submit a URL Categorization Change Request to have it classified as a Malware Site.
-Dan
-Dan
posted screenshots are redirects from https://www.300mbmoviess.com/@ wrote:
If you run into malicious URLs that are not blocked, you can submit a URL Categorization Change Request to have it classified as a Malware Site.
-Dan
since Dan posted
quote:
We are evaluating the risks of the popups not currently being under blocked categories, however we confirm that there is no discrepancy in behavior between browsers, the different behavior depends on the URL contained in the popup. end quote
I've added relevant content (redirects) to this topic.
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.