Hi
This week I was whitout Internet at home during 4 days.
I would like to know what could have happened if I have inserted a CD or an USB key with a virus or another malware and copied it on my PC' hard disque ?
Solved
What can happen whitout Internet ?
Best answer by MikeR
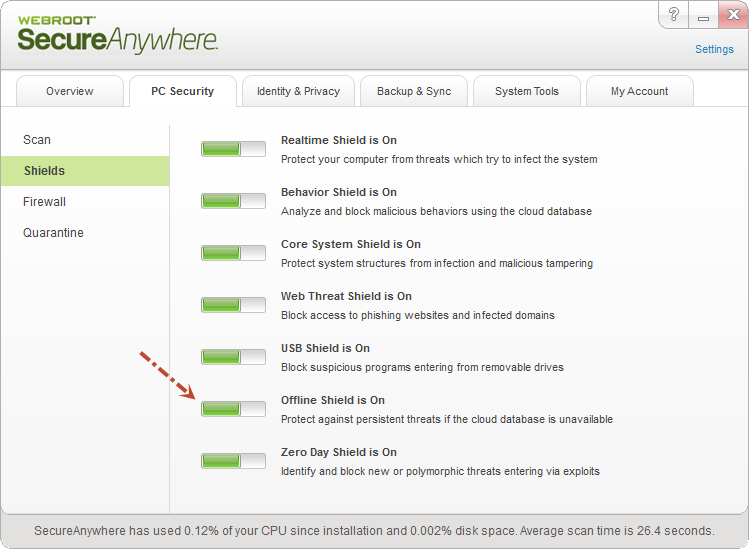
While WSA has the strongest protection when connected to the Internet, it provides significant protection when offline. A few thousand critical signatures are pushed down from the cloud for offlineprotection. The client remembers all of the files it's been told about to provide protection.
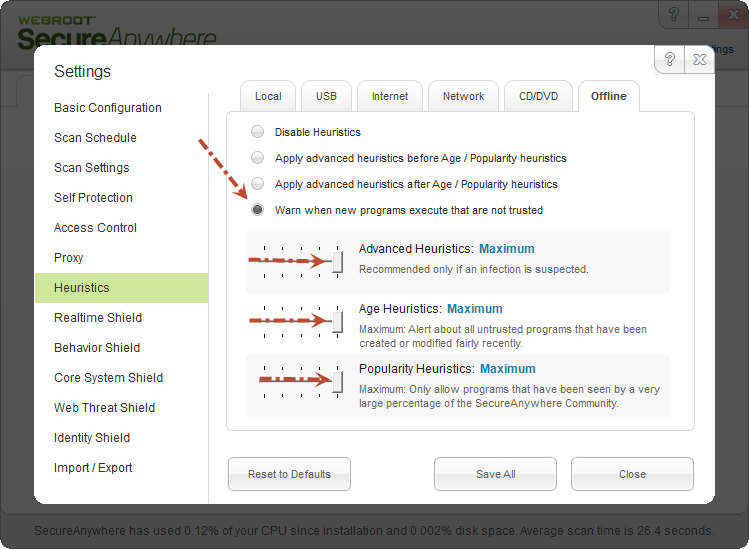
The client further uses behavioral heuristics to block threats when offline and can even turn into a full "whitelist-only" mode. All files are set to monitor when offline - heuristics are applied in real-time and pre-execution. Each system modification is precisely tracked by WSA. Once the client is back online, if a program is eventually found to be malicious, every change that was made can be reverted.
The client further uses behavioral heuristics to block threats when offline and can even turn into a full "whitelist-only" mode. All files are set to monitor when offline - heuristics are applied in real-time and pre-execution. Each system modification is precisely tracked by WSA. Once the client is back online, if a program is eventually found to be malicious, every change that was made can be reverted.
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.