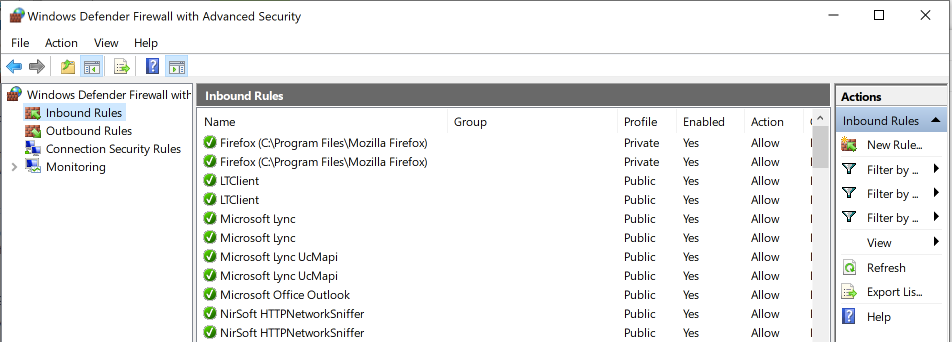
How can I tell if I have an unsecured RDP connection on my Windows 10 desktop computer?
Unsecured RDP connection
Best answer by coscooper
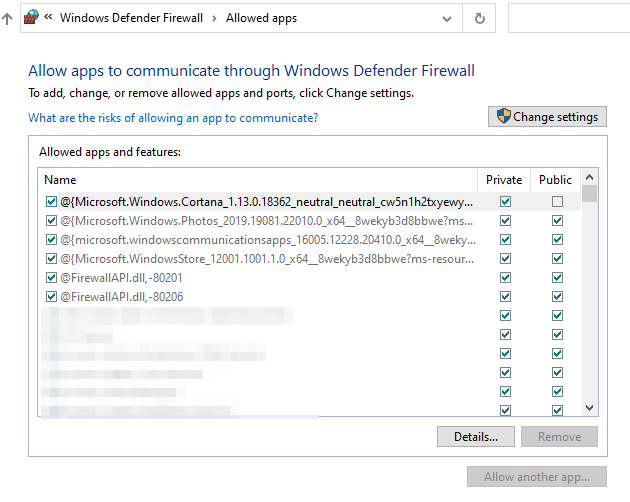
However, the easiest way to confirm that your device isn’t exposed, is to check the Application Allowance section of the local firewall. For Windows10, look for the Remote Desktop line and insure they’re both off for private or public networks. This is more of a check for the remote settings you’ve already disabled.
Windows Defender Firewall → select “Allow and app or feature through Windows Defender Firewall”
Look for Remote Desktop and make sure both are NOT enabled or either network type.
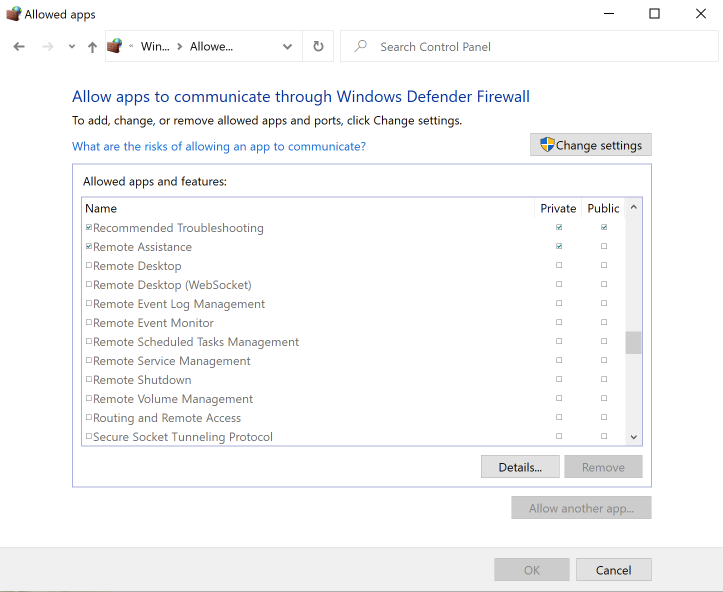
Hope this helps.
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.