Updates on threats I’m seeing and other stuff from Webroot’s threat and malware removal teams especially in EMEA. Feel free to distribute or steal. Get to me @threatmurray or kmurray@opentext.com.
For more threat news updates see the weekly Cyber News Rundown from my US team mate, Connor Madsen. or the Webroot community updates from Tyler Moffit.
“Botnet”- 27th August 2021
The greatest malware empire ever[i], the arrival of cryptolocker[ii] and the largest internet outage of all time[iii] have something in common. They were all due to botnets.
A botnet is a collection of compromised machines or systems that all work together somehow. For good reason they have been called zombie machines, but they are often perfectly functioning systems that perform criminal work on the side, unbeknownst to their users. After an initial deployment by its masters, a botnet will infect machines and spread itself around the globe almost entirely automatically through a variety of means. In this way the numbers can grow into hundreds of thousands, and they become a huge, powerful army to whoever controls them.
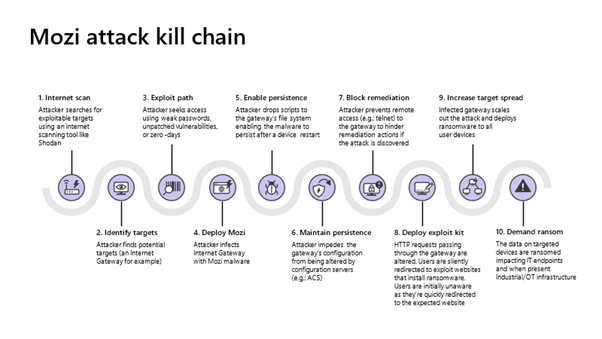
Mozi is the name given to a botnet first discovered in 2019 that targets routers and IoT devices. The criminal network has had a rebirth recently and has been given some impressive technical upgrades. The current version of Mozi spreads to devices through weak telnet passwords but it also uses many other product vulnerabilities to propagate. In this case and many others, Mozi is the name given to the malware that takes over a host but also the name given to the botnet as a whole. A update would prevent you from getting infected but how many people have updated their Netgear router or DVR player recently? This is one of the big problems with smaller devices such as routers and with IoT devices, they are a pain to update as the process often involves technical knowledge that the average user wouldn’t get without much Googling. Some old routers can never be made secure and need to be replaced but are all ISPs are calling door-to-door replacing old stock?
Attack flow for Mozi botnet – Microsoft Blog 19th August 2021
Previous versions of Mozi used its army of machines to carry out DDoS attacks. Distributed Denial of Service attacks work best in this way when launched from many nodes and there has been a long history of criminal botnets being used to take down internet services such as with the Mirai botnet attacks on the Dyn DNS provider in 2016. This attack used over 100,000 infected endpoints to overwhelm the worlds internet, taking out most of the world’s major websites such as Amazon and Twitter [iv]. The current version of Mozi tampers with victims’ traffic and this can be used to misdirect users to malicious network spaces, download ransomware or as a means of spreading.
A world record breaking DDoS attack was launched from a 20,000 device botnet this year according to recently released data from Cloudfare. In less than a minute some 300 million (web) requests were sent to a financial organisation which Cloudfare then managed to mitigate. These attacks can be used to disrupt services and bring down websites but they can also be used to mask hacking activity.
When looking into the history of botnets, Mirai and Emotet are probably the most famous. Both were taken down by law enforcement but since their technology was so successful, they are always going to live on in one form or another. A Mirai-based botnet targeting many Internet-exposed wireless devices, residential gateways, travel routers, IP cameras, and connected toys has been given an upgrade to now exploit devices containing a particular Realtek chip. The size of a botnet depends on its ability to spread and much like the biggest and best botnets, these exploits allow it to infect many different types of devices.
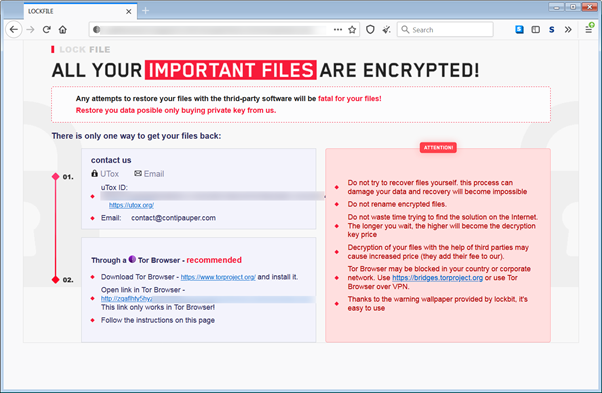
A “ProxyShell” exploit affecting Microsoft Exchange servers is being used to drop LockFile ransomware onto Windows domains. The exploit which allows remote code execution is used in conjunction with another windows vulnerability, PetitPotam in these attacks and Microsoft are issuing a warning to any Windows administrators to patch and update.
nce you see this LockFile ransomnote it will be too late.
Ransomware is the subject of a recent blog and video post from my US colleague, Tyler Moffit. It is the second instalment in the Rise of Ransomware series, and I would recommend anyone who is looking for some context on modern ransomware to check it out.
[i] https://www.brighttalk.com/webcast/8241/434654/webroot-podcasts-emotet-past-present-and-future
[ii] https://www.europol.europa.eu/newsroom/news/international-action-against-gameover-zeus-botnet-and-cryptolocker-ransomware
[iii] https://www.webroot.com/blog/2016/10/21/ddos-attack-dyn-cripples-internet/
[iv] https://www.theguardian.com/technology/2016/oct/21/ddos-attack-dyn-internet-denial-service