Note: this is the third installment in a 3-part post. If you haven’t already, read part 1 and part 2.
2018 was a brutal year for Bitcoin and subsequently all other altcoins utilizing blockchain technology. The start of 2018 had Bitcoin around $17,000; by the end of 2018 it had dropped to around $3,800. Not only was this devastating for investors, but cybercriminals also took a major financial hit (your heart weeps for them, I know.) What’s interesting is that we also saw major decline with cryptomining attacks as the price decreased, presumably because the attacks were no longer as profitable. In late February ($3700), Coinhive abruptly announced the impending end to its service. The stated reason: it was no longer economically viable to run.
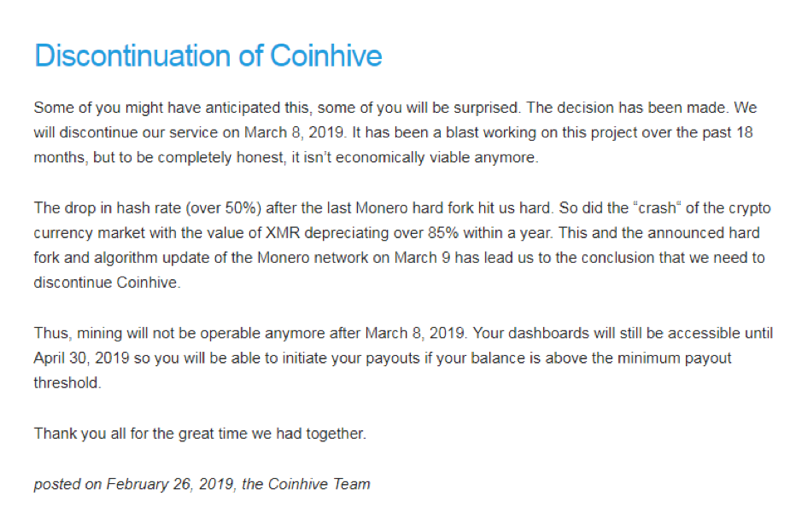
To be honest, I did not see this coming, but I do understand. It’s reasonable to think that Coinhive didn’t intend for their creation to be abused by criminals, but they have still kept 30% of ALL the earnings generated by their script—which was often found running illegally on hijacked sites. Most of that profit came from illicit mining, which (justifiably) earned Coinhive a lot of negative press.
Additionally, 2018 was a terrible year in terms of the US-dollar value of Monero (XMR), which means their service is significantly less profitable relative to what it once was. Combined with the fact that the XMR development team hard-forked the coin and changed the difficulty of the hash rate, this means Coinhive is making very little money from legitimate miners.
Coinhive created this service so legitimate domain owners could host their script and generate enough revenue to replace ads. Ads are annoying and I believe this innovation was a genuine enough attempt to fix that problem by offering an alternative for websites to generate revenue. But the ultimate result was a bunch of criminals breaking into other people’s domains and injecting them with Coinhive scripts to essentially steal from the domain’s visitors. Without users’ consent, millions of victims’ computers were subjected to maximum hardware stress for extended periods of time, all so some criminals could make a few pennies’ worth of cryptocurrency per computer.
Here’s an ethical question for you: if you found out that the money you earned from your startup business was a cut of criminal activity, would you keep it up? Well, maybe you would look the other way if the money was good enough (not judging)… But it’s just not worth it these days. Back in 2017, when the hashing difficulty was easier (you earned more XMR) and XMR was worth 10 times what it’s worth now, it made more sense.
These days, there are of other cryptojacking copycats—Cryptoloot, JSEcoin, Deepminer, and others—so criminals have plenty of similar services to choose from in the aftermath of Coinhive’s closure. But, at the time of its shutdown, Coinhive had about around 60% share of all cryptojacking campaigns. Since the shutdown, cryptojacking services have been dying a very slow death of around 3-5% decline month over month. But what happens if we see another colossal pump like we did in 2017. Will all these attacks come back, will there be new tactics?
Comment back with your thoughts.



