Microsoft remains the most spoofed brand in phishing attacks in the new year. The number of variations of theme within the Microsoft brand is quite extensive. To put it plainly, if it is a Microsoft business/consumer service, mostly likely we have seen a multitude of phishing attacks invoking it to dupe users into falling victim.
A recent attack added a rare new twist by invoking the Microsoft Bookings (Scheduling tool) to instill a sense of legitimacy in the mind of the recipients. It purported to be an “Encrypted EFT Invoice Payment” with a link to the invoice, which the user would need to click on to retrieve. The link leverages ncv.microsoft[.]com, Microsoft Dynamics customizable survey offering that is abused heavily by threat actors for attacks like these. Through abuse of this Microsoft service the actors obscure the malicious nature of the URL as a Microsoft domain would not arouse suspicion for most everyone taking the time to look. Utilizing Dynamics also servers to keep the branding cohesive within the attack. In other words, it is a Microsoft Bookings message with a Microsoft link so what could possibly go wrong…
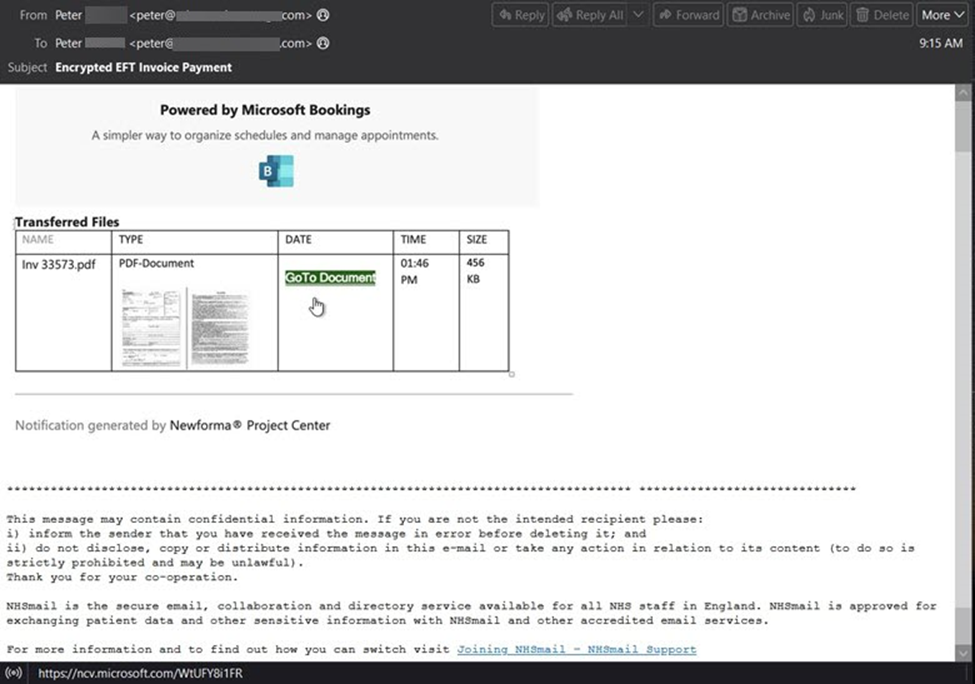
If the user clicks the link, they are directed to a phishing jump page hosted on customervoice.microsoft[.]com. This page urges the user to click again to view the “secured pdf online document.”
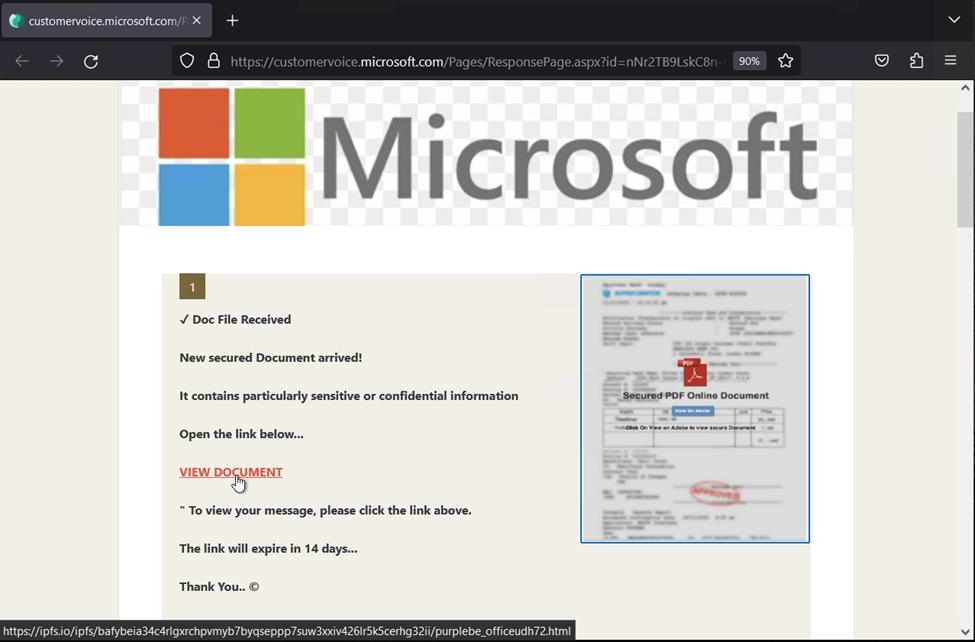
On this page is a secondary link which points to ipfs[.]io, the distributed peer-to-peer file sharing gateway that we have discussed previously here. It is there the attack delivers the true payload – a Microsoft 365 themed credential harvesting portal.
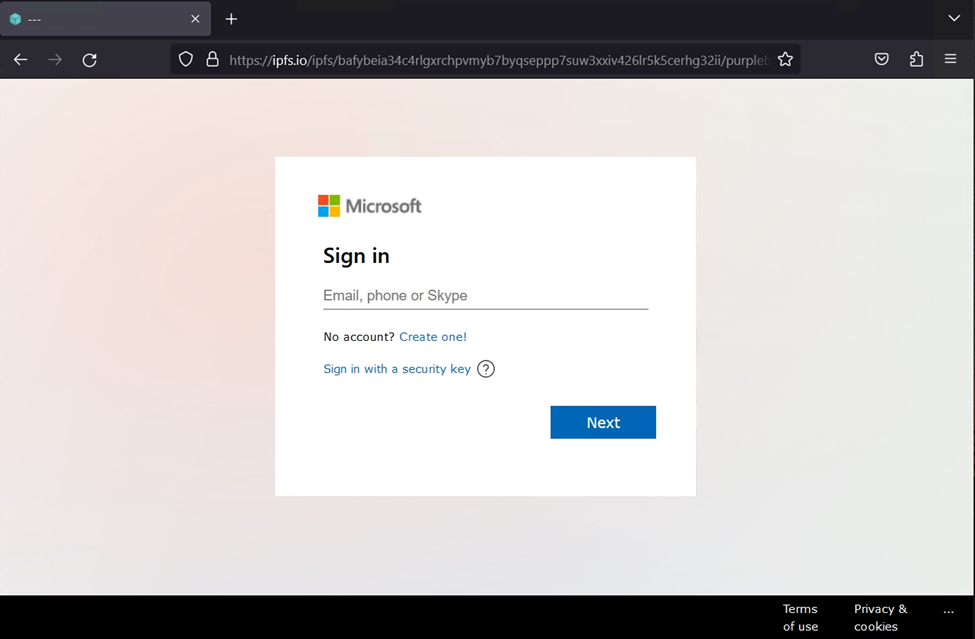
Remember never to place blind trust in a brand name. Just because a remarkably familiar brand may be present, even at the URL level, it does not mean it is safe.


