We recently discovered a highly targeted malware attack only sent to only a handful of customers who possibly have personal connections to Ukraine. The attacks focused on select users at three separate organizations, an election company that serves both businesses and governments along with two other organizations dealing with influential public advertising and marketing. Over the course of three days, we saw the same threat actor attempting to infect the same specific users using separate and distinct malware families.
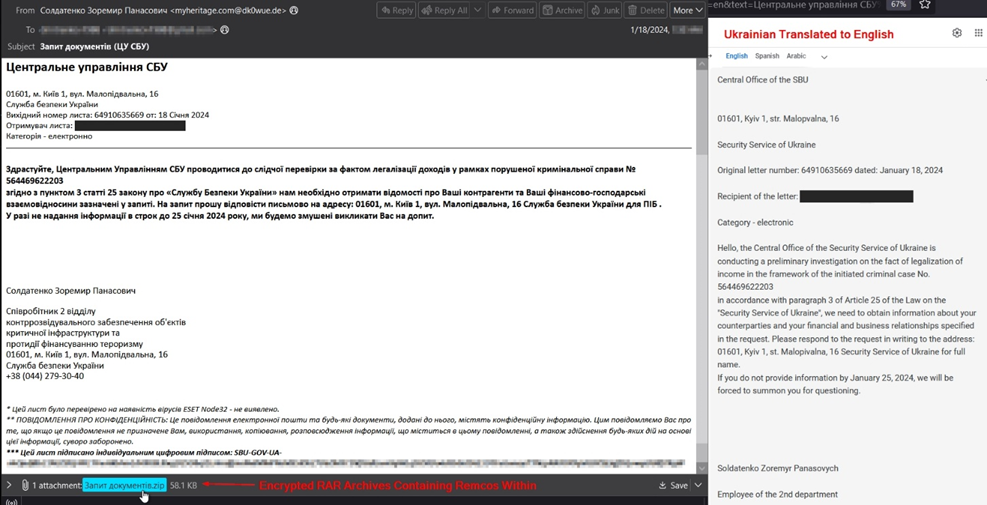
The first attack purports to be from the Central Office of the Security Service (SBU) of Ukraine. The theme was around an investigation into the legalization of income and soliciting information from the recipient contained within the [.]ZIP attachment. In both attacks, they utilized bitbucket as its command and control (C2) communication to deploy payloads. It also utilizes the same C2 IP (185[.]70[.] 104[.]90) which resolves to hostkey[.]ru in Moscow.
If the [.]ZIP is extracted, it contains two encrypted [.]RAR archives and a text file. The text file contains the password which is required to extract the first [.]RAR archive & once extracted, an executable is visible within. If this first executable is launched it reaches out to bitbucket for the means to decrypt the second [.]RAR archive and launch the second executable. This executable, in turn, infects the system with the Remcos remote access trojan.
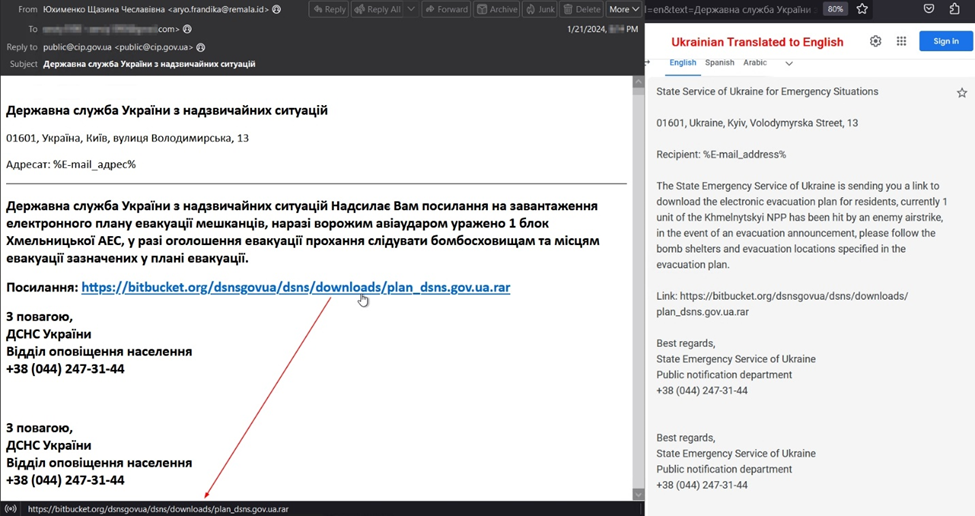
Only three days later, we observed a second attack targeting the same users. The message was again in Ukrainian and purported to originate from the “State Service of Ukraine for Emergency Situations.” The message contained a link to a download a [.]RAR (archive) file hosted on bitbucket[.]org and had an evacuation plan for residents seeking refuge within bomb shelters due to enemy airstrikes.
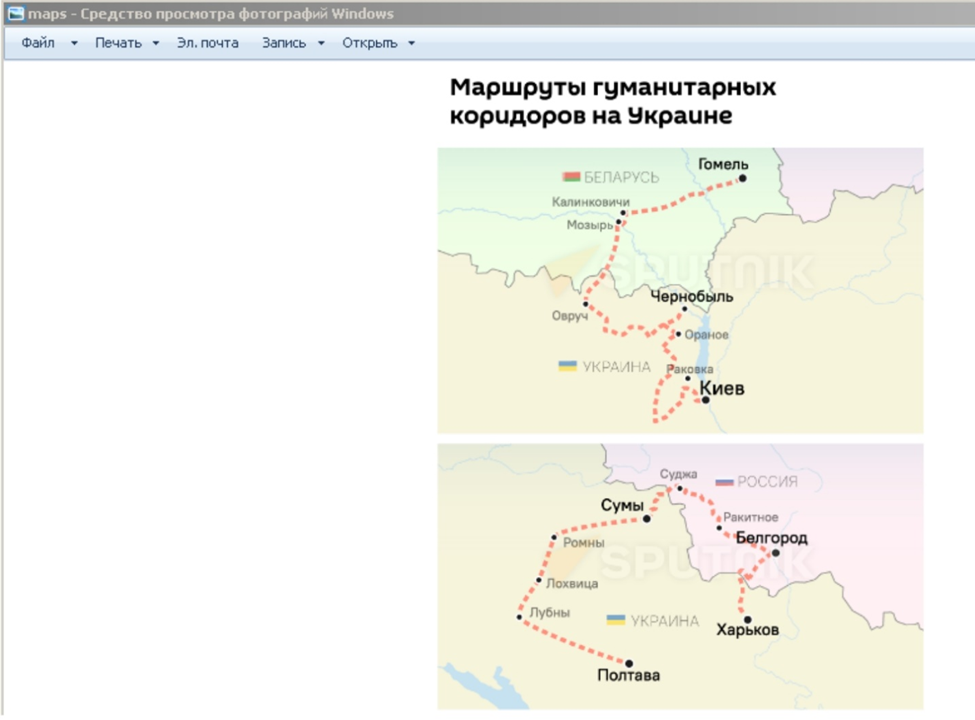
If the archive is downloaded, there were several maps within which showed evacuation routes relevant to the initial lure, but it also contained a secondary [.]ZIP (archive) as well. When extracted and executed it loads RuRAT. RuRAT is a Rust programing language remote access tool available on Github and via Remote Utilities LLC (for legitimate administrators) which allows victim file operations, persistence, reverse shell, and remote code execution capabilities. This tool has also been documented for the past couple years in email-borne attacks with the most notable attacking media organizations within the United States.