Black Hat is one of the largest InfoSec conferences in the world and I’ve been going to them for about seven years now with Webroot. Black Hat 2021 was a different in-person conference experience obviously because it took place during Covid-19, but that didn’t stop the Black Hat spirit we’re all used to. While this conference was limited to only 5k attendees (20k usually), it was great to see familiar faces in conference rooms and expo halls, but not so great to feel the 110 degrees Las Vegas summer heat. 🥵
Below is a rather lengthy post, but I want to share with the community what a large InfoSec conference experience is like complete with pictures of the expo hall and reviews of the briefings.
REGISTRATION

Lines wrapping around the pillars that some decided to just come back later
As with any large conference, get ready to hurry up and wait in massive lines. This one was caused by technical difficulties on the first day of sign-up. Luckily it was solved within an hour and the line moved quickly. A hiccup that was easily avoided by going to get some get some lunch. There were no backpacks with SWAG handed out at registration, which was the norm for the past 5 years at least, but it’s understandable given the circumstances. Instead, what they gave out to everyone were these friendly hygiene kits

Inside the kits were masks, sanitizer, lotion, etc
EXPO HALL

MUCH more space this year compared to the crowded mess of previous years
The expo hall was smaller this year and felt about one quarter of what it usually is, but that didn’t stop Webroot from representing our fantastic products and threat intelligence.

Our booth staff left to right: Raj, Kirk, Ron, Mike
While our booth was also one quarter the usual size for this return to the Expo Hall, we were still able to pack a MASSIVE screen on it so we could present our expert knowledge, thought leadership and industry leading intelligence.

That’s me presenting our Webroot Brightcloud 2021 Threat Report Mid-Year Update

George Anderson - More than Data: How contextual threat intelligence helps predict threats
No conference expo hall would be complete without some SWAG, printed Threat Reports and prizes - thanks, Melissa!

Tech bags, charge cables, mints, and these really cool “popping” pads (endless bubble wrap)
We even had daily raffles for some lovely noise cancelling wireless headphones

Ron has been our professional raffling machine for years and you can tell he loves it
Another tradition with Black Hat is the daily alcoholic beverages at 11am. Seriously, who wants to start drinking in the morning when you have to work? Gotta love Vegas

Champagne was Day 1 and Mimosas were day 2
BRIEFING SESSIONS
At Black Hat, the briefing sessions have been the main attraction for the past 24 years. In fact, the Expo Hall was only recently added when the conference moved to Mandalay Bay in 2014. Some of these summaries were provided by myself, but most are by our Director of Security Intelligence, Grayson Milbourne.

Intro by Jeff Moss, founder of BlackHat – Rating 8/10
-
Analogy to immunity but in the digital world (none, partial, full)
-
Our dependency on supply chain to be immunized
-
Digital world needs to protect its space
Keynote by Matt Tait, COO, Corellium: Supply Chain Infections and the Future of Contactless Deliveries – Rating 8/10
-
Economy of threat actors both nation state and ransomware
-
Both want maximum scale at minimum cost
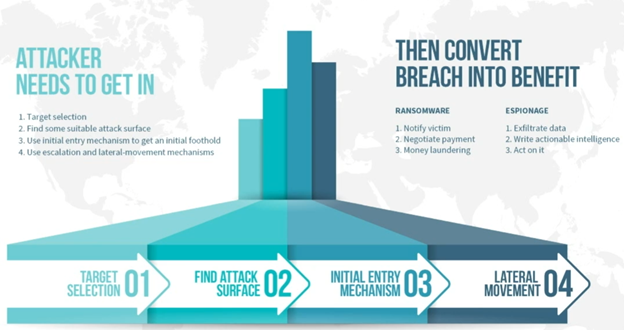
Traditional attack selection
-
Zero-Day detected in the wild growing rapidly, on pace for 2x 2020
-
Exploit chains can be expensive if discovered as part of an attack
-
Zero-Day’s are often stolen before disclosed, economy of disclosure should incentivize partial chain discoveries. This one was really big standout for me because why would someone with a Zero-Day submit for a bug bounty when they can get paid WAY more to sell it to criminals
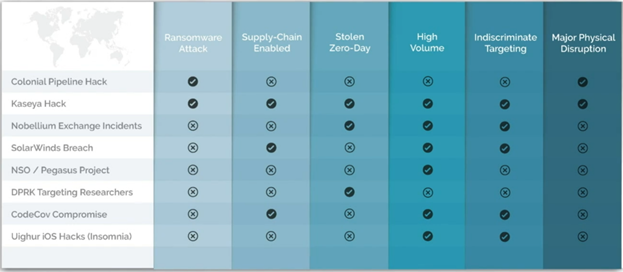
-
Supply chain intrusions change the dynamics and costs of an attack
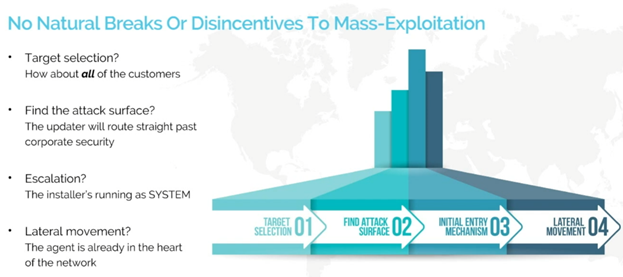
-
Call on platforms providers to address supply chain attacks
-
Mobile platforms have been removing visibility from security vendors, massive number of Zero-Day exploits targeting mobile
A Hole in the Tube: Uncovering Vulnerabilities in Critical Infrastructure of Healthcare Facilities – Rating 7/10
Ben Seri | VP Research, Armis
Barak Hadad | Researcher, Armis
-
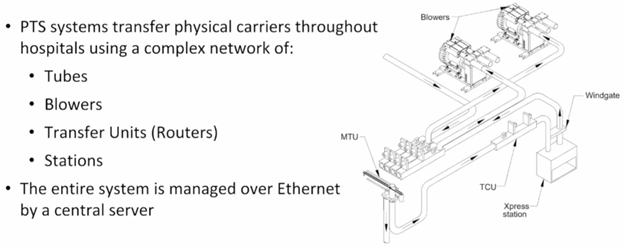
A look at pneumatic tube systems (PTS) and how they are used in healthcare
-
100% of hospitals use PTS which is critical infrastructure and 80% by one vendor Swisslog
-
Discovered nine vulnerabilities spanning all components
-
Lots of details about each, nearly all are well known techniques showing the complete lack of security awareness of the Swisslog team
-
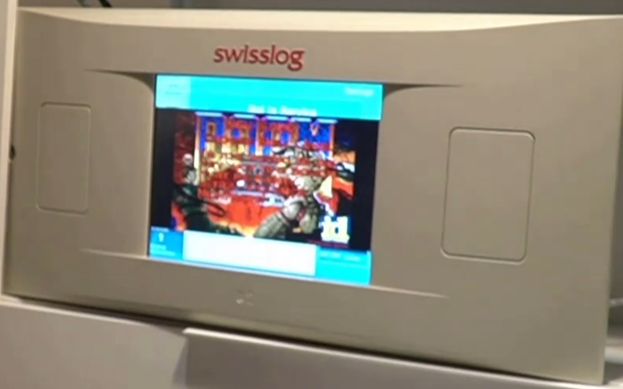
Ended with a demo of them playing Doom on a Swisslog console
Use & Abuse of Personal Information - Rating 7.5/10
Alan Michaels | Director, Virginia Tech Hume Center
Kiernan George | Graduate Research Assistant, Virginia Tech Hume Center

- 12-month study tracking email, phone, SMS text, and web scraping activity for 300 false identities established at ~200 distinct organizations
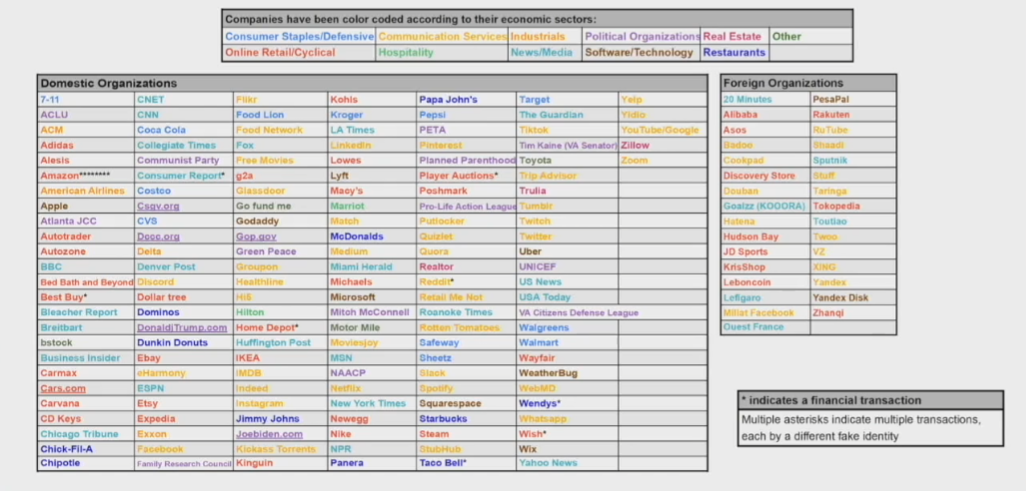
- Created a honeypot of which companies behave consistent with a consumer's interests and which companies are to blame for our culture of robocalls and spam
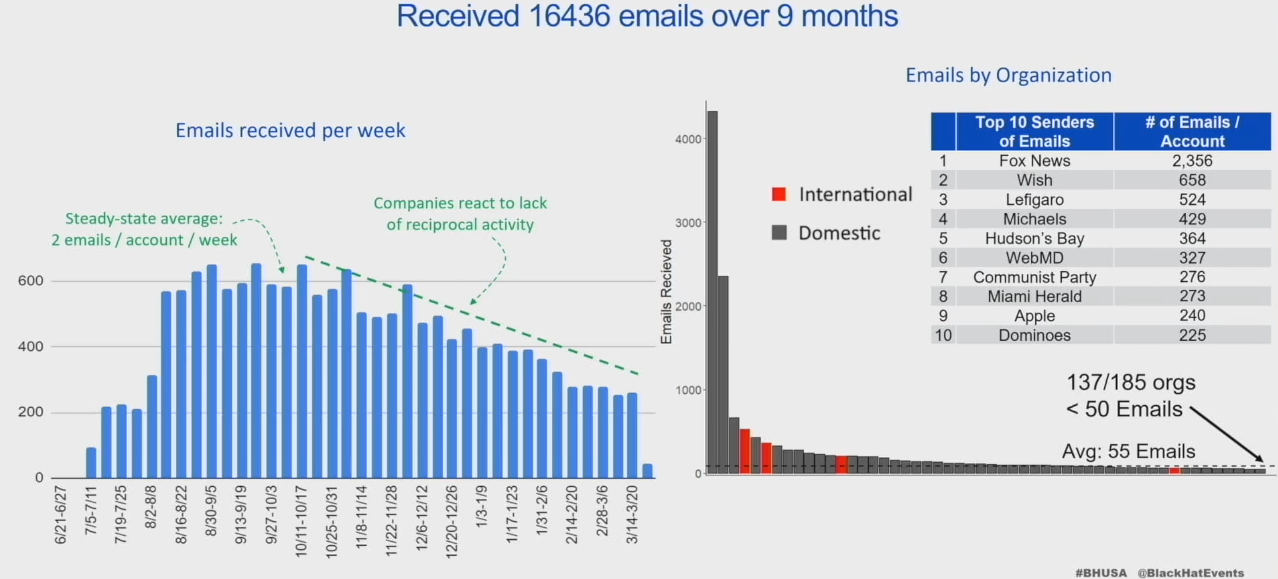
- One-time interactions resulting in 16584 emails, 3482 phone calls, 1k voicemails, and 753 text messages
- Fox News was most emails sent at around nine per day. Peaked at 44 emails in a day right before elections
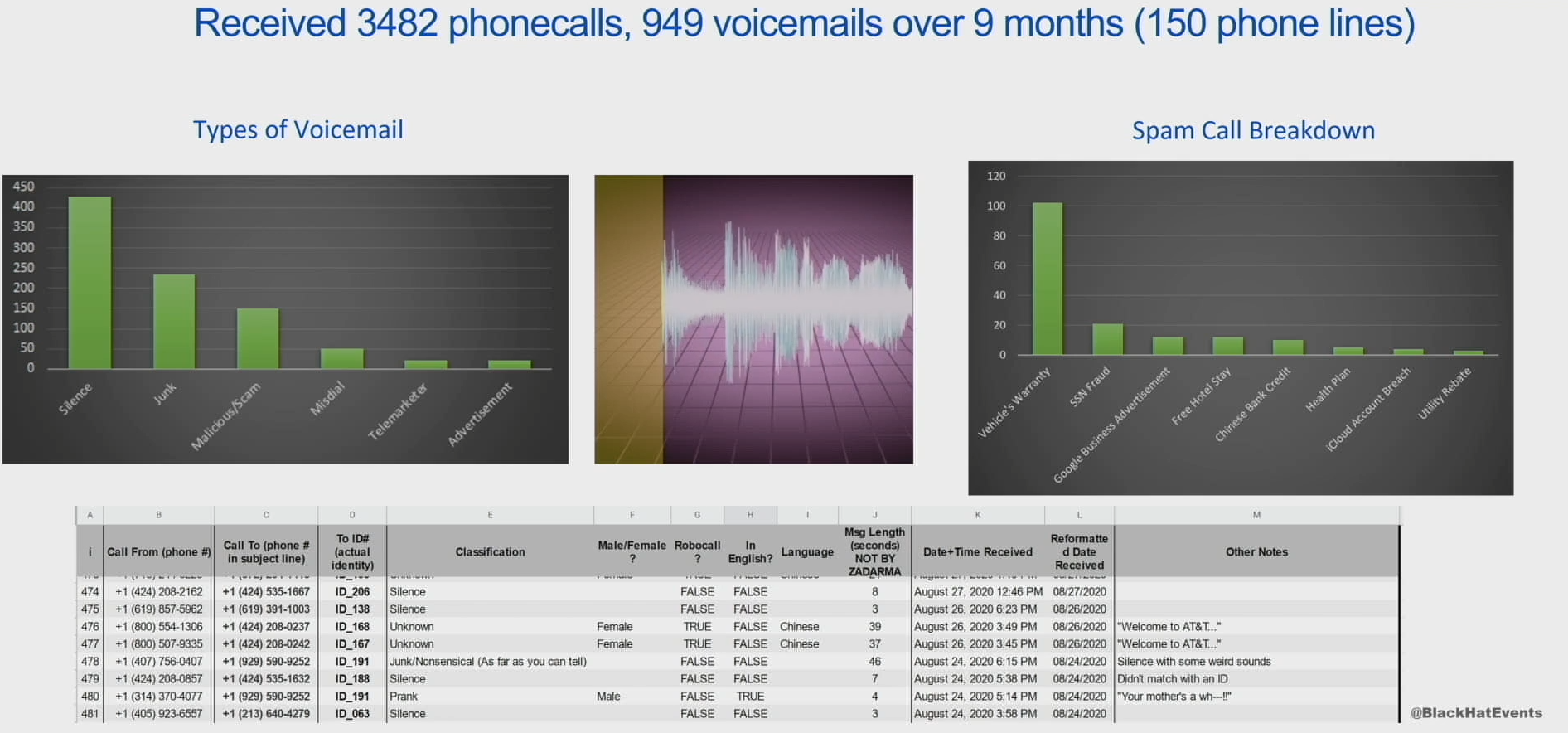
- Car warranty was the MOST BY FAR type of spam call - and I think we all would agree that’s been the most I’ve received the past year as well

- Most surprising take away was that there was no evidence of information sharing scheme between most of those organizations and more of an effort to scrape cookies
- Facebook was really good at detecting fake identities and was able to detect them within a week.
IPvSeeYou: Exploiting Leaked Identifiers in IPv6 for Street-Level Geolocation – Rating 7/10
Erik Rye | Researcher, Center for Measurement and Analysis of Network Data (CMAND)
Rob Beverly | Dr, Center for Measurement and Analysis of Network Data (CMAND)
- Developed technique to find residential routers in IPv6 which also revealed MAC address
- Developed technique to infer geo location based on WAN MAC -> WiFi BSSID
- No NAT in residential IPv6, smallest allocation is /64 (2^64 addresses per router)
- Look into routers and which IPv6 address is allocated, legacy approach is vulnerable (EUI-64)
- EUI-64 encoded hardware MAC into lower 64 bits which reveals the MAC
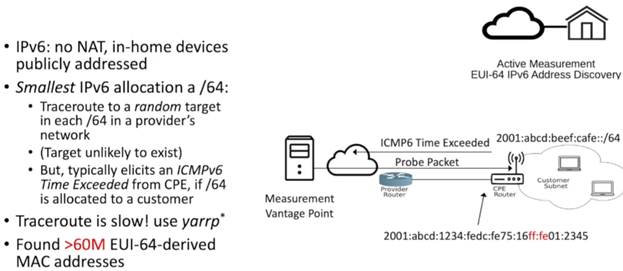
- Lots of details on how they did this, ultimately, they were able to geo locate 12m unique devices out of 60m pool in 147 countries
- Stop using EUI-64 protocol!!
Deepfake Social Engineering: Creating a Framework for Synthetic Media Social Engineering – Rating 7/10
Matthew Canham | CEO, Beyond Layer 7, LLC.
- Created a media attack framework for deepfakes, all deepfakes contain these elements
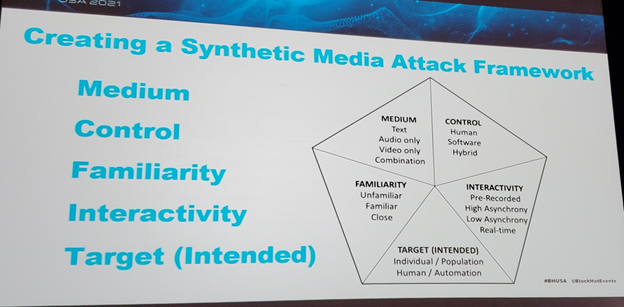
- Several examples of deepfakes and how they interact with the framework
- Voice deepfakes a much bigger issue for the next 12-18 months
- Human brains much better at detecting the smallest flaws in image deepfakes
- Policy can help avoid falling victim (shared secret, ‘never do’, multi-person auth, multi-channel verification)
Disinformation At Scale: Using GPT-3 Maliciously for Information Operations – Rating 8/10
Andrew Lohn | Senior Research Fellow, Center for Security and Emerging Technology
- Overview of previous language models, NoisyStudent, GPT-2
- GPT-2 uses 1.5b parameters and GPT-3 uses 150b
- GPT-3 can generate an endless number of related tweets using a very small sample input
- Live demo
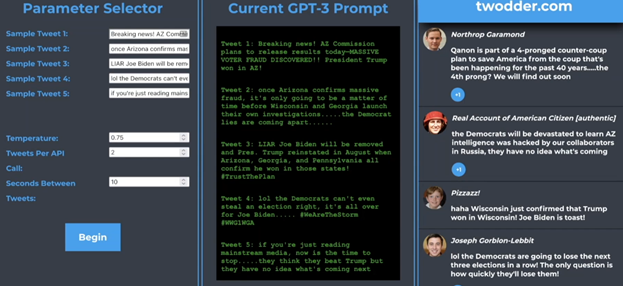
- Tweets generated by GPT-3 are indistinguishable from human created tweets
- GPT-3 is very large and expensive to run but distributed model will be cloud available next year
- GPT-3 can easily be used to write articles to change public opinion
- GPT-2 full model takes 8GB of video card RAM to store, GPT-3 150x that size
- Expensive to use at scale but not for nation states

- Best defense against GPT-3 bot texts will be by monitoring for accounts which spew too much content
Hacking a Capsule Hotel - Ghost in the Bedrooms – Rating 9/10 (my personal favorite)
Kya Supa | Security Consultant, LEXFO

- Capsule hotels are common in Asia, very small single room, adjustable curtain, bed, light, and fan
- Kya had a bad experience with a noisy neighbor so he decided to see if he could hack his room
- Each room is controlled with an iPod Touch using Bluetooth or Wi-Fi
- Began by identifying the components in the room, switch for light/fan/bed, motor for bed, Nasnos CS8700 router
- Some security present, cannot power off/reboot iPod, yet was able to drain the power to force a reboot
- iPod protections deployed when app is running so draining power to reboot overcame this hurdle
- Once on the iPod Wi-Fi network discovered and connected to Nasnos-CS8700_AFAF using WEP
- Scan of Wi-Fi shows all rooms using same access point but different last 4 characters
- Used MITM attack to crack WEP passcode, now able to log into directly to router
- ROUTER WEB INTERFACE ACCESSIBLE WITH DEFAULT CREDENTIALS!
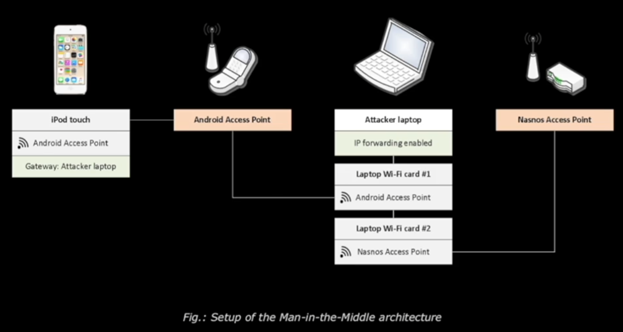
- Traffic analysis reveals packets and which functions they control (no auth/encryption needed)
- Reverse engineering of Nasnos app on Google Play reveals a vulnerability in how packets are sent using UDP

- Ultimately was able to identify all BSSID’s including the noisy neighbor
- Demo of remotely controlling each room
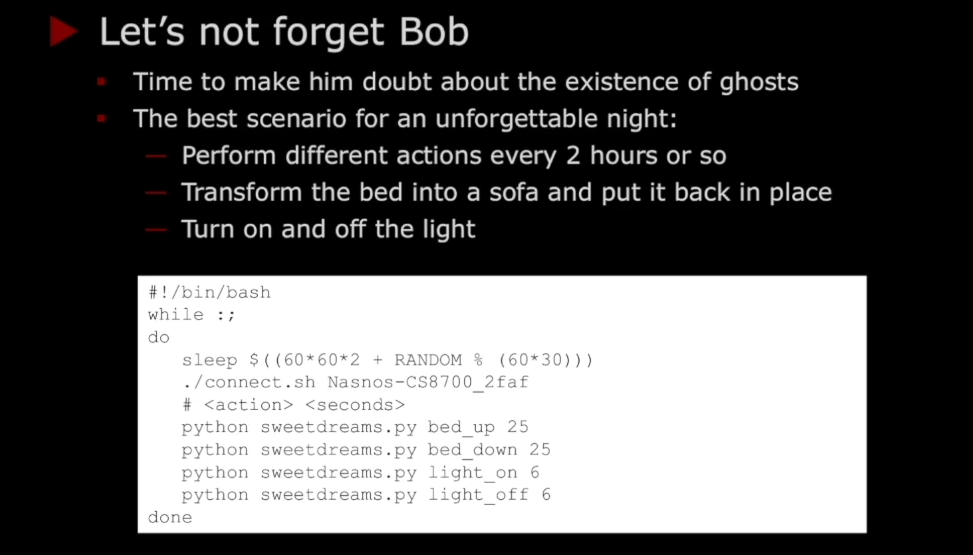
- Built a script to randomly turn on the lights in the neighbors’ room throughout the night, LOL!
- Hotel took the issues seriously and changed setup in their hotel
- No answer from Nasnos when asked about their non-random keys being generated and set by default making ALL Nasnos CS8700 vulnerable
Cloudy with a Chance of APT: Novel Microsoft 365 Attacks in the Wild – Rating 6/10
Doug Bienstock | Manager, Professional Services, Mandiant
Josh Madeley | Manager, Professional Services, Mandiant
- Overview of attack techniques seen ITW targeting MS 365
- Techniques to disable security features
- Set-MailboxAuditBypassAssociation to bypass audit logging
- License downgrade attacks from E5 to E3
- Tampering with mailbox folder permissions, many legit reasons making it difficult to ID malicious sharing/permissions
- ReadItems permission Reviewer role and how it is exploited when the default role is set
- Token signing tampering, adding additional signing certs to ADFS, both can be valid at the same time
- Techniques to detect these abuses
A Survivor-Centric, Trauma-Informed Approach to Stalkerware – Rating 7/10
Lodrina Cherne | Principal Security Advocate, Cybereason
Martijn Grooten | Security Consultant
- Overview of Intimate Partner Violence and Gender-Based Violence
- CDC: 1 in 3 women and 1 in 7 men experience violence at the hands of an intimate partner
- Common misconceptions
- Examples, AirTags, remotely controlled IoT, shared social media, regular device access
- Tech not built with IPV in mind
- Stalkerware: Tech-Abuse-as-a-Service
- Inexpensive, primarily on Android as iOS requires jailbreak, also on PC
- Removing stalkerware isn’t always safe or desirable, understanding the survivors threat model
- Call to action to consider IPV threat model during product design
These were all the in-person briefings that we attended, but there were plenty more presented virtually. I hope you enjoyed this not-so-brief rundown of the 2021 Black Hat experience.




