Cyber Threats in the Time of COVID-19
In the past 3 months, we’ve seen a staggering amount of change worldwide, not least of which involves the majority of global business offices switching to WFH. With so many employees suddenly working from their home devices and networks, this massive shift has brought numerous challenges for employees and employers alike.
One of the main challenges is that many employees were not set up for successful, secure remote work. While they might’ve had antivirus, DNS protection, VPNs, group policies, and other cybersecurity measures on corporate devices, not all employees could take these computers home with them. That means they had to start using personal devices for work, which begs the question: how many of those devices had robust cybersecurity measures (if any) in place? Probably not many at all.
So now the problem becomes clearer; valuable company data is being sent via unsecured or inadequately secured devices, across unsecured or inadequately secured networks, all far away from the watchful eyes of IT teams.
Cybercriminals have been taking advantage of these shifts with some tried and true methods, including two big ones that we’ll focus on today: phishing and Remote Desktop Protocol (RDP). I’ll cover some details on these malicious campaigns, as well as tips to help you stay safe.
Phishing
At this point, it’s pretty unlikely that you’ve never heard of phishing. It’s one of the most widely used and effective methods of stealing user credentials and sensitive or personally identifiable information, such as credit card numbers, social security numbers, usernames, passwords, etc. Phishing attacks are often carried out in the form of scam emails, spoofed social media messages, fake texts, etc. They may contain a link to a website that’s full of malicious code and other threats, hoping you’ll click the link and download malware or enter personal information for criminals to steal.
We posed some questions regarding cybersecurity in the age of COVID-19 to our Webroot advocates (Luminaries) and they had some very informative responses. Check out some of these conversation points:
What other threats have you or your clients seen re-emerge since COVID-19?
“Many virus' and dodgy links going around claiming to be important company news about Covid-19 or breakthrough news about Covid-19.”
“Phishing is by far, without a doubt, the main threat that has made its comeback.”
Have you taken extra measures to protect your clients from phishing attacks since COVID-19?
“We run regular simulations for our clients and advise them to check any suspicious emails with us before opening.”
“We intensified our security awareness training with specific focus on such scams.”
Many new phishing campaigns are using COVID-19 to get people to click malicious links or download malicious files. Here’s a screenshot of a fake White House website:
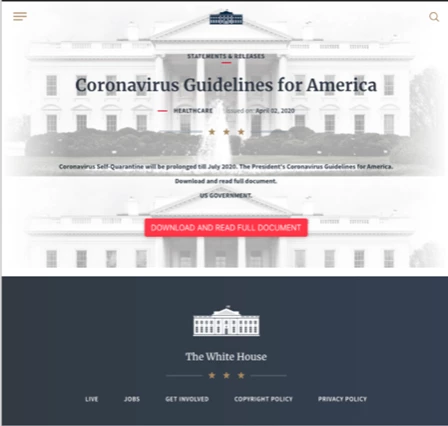
Notice the “Download and read full document” button. Clicking that button would download a Microsoft Word document that is injected with a macro-enabled script. If you tried to open it, it would ask permission to “enable content,” which is the real trick that allows the malware to infect your computer (likely with ransomware).
Word document that is injected with a macro-enabled script. If you tried to open it, it would ask permission to “enable content,” which is the real trick that allows the malware to infect your computer (likely with ransomware).
Here’s an email that impersonates Donald Trump to prompt recipients to click on the phony link.
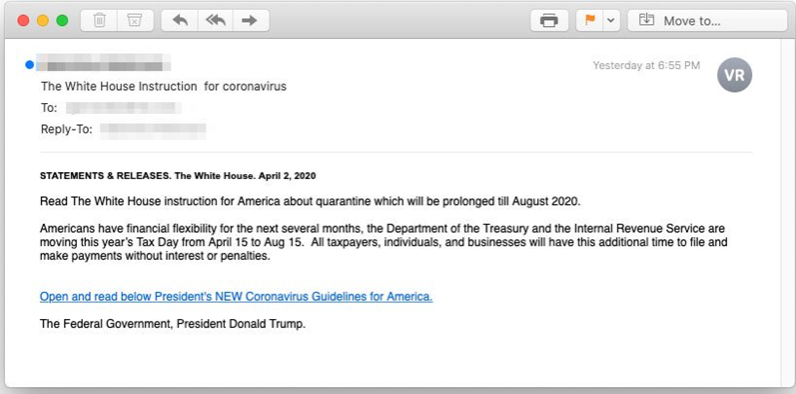
The goal here is to take advantage of the fear and desire for information many of us share. Fear or panic-inducing language causes us to use less caution when clicking things that promise guidance or solutions. This is actually the foundation of most phishing campaigns—criminals use social engineering tactics to create situations in which we’re more likely to click without thinking. (See the fake email above or imagine, say, a fake email from your boss or CEO that demands quick action. Hello, Business Email Compromise…)
We all make mistakes—especially if we’re scared, worried, in a rush, or otherwise not thinking clearly—and that’s what the bad guys are counting on. It makes total sense that they’d take advantage of a global pandemic.
In addition to the rise in these types of emails and fake websites, we’ve also noticed a major uptick in the number of website domains that use words like coronavirus, COVID, health, masks, and corona. Sure, plenty of these websites are legitimate, or, at least, aren’t riddled with malware. But Webroot has found that 2% of these new domains are indeed malicious. Check out these stats in the screenshot below.
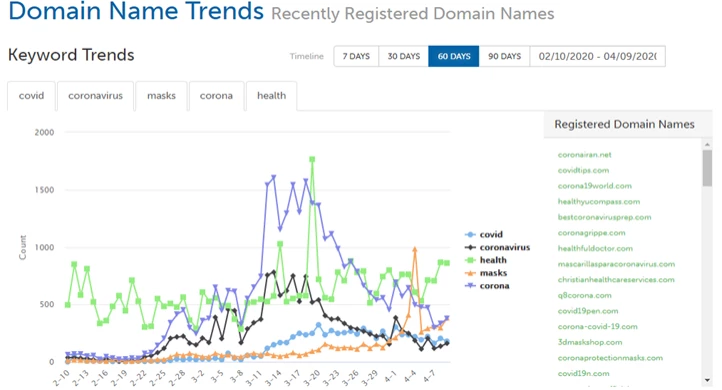
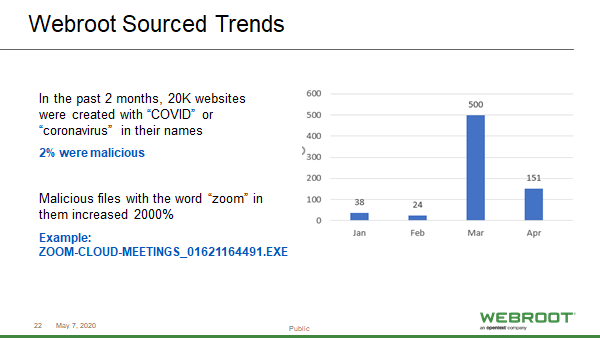
Out of the 20,000 new websites created with “COVID” or “coronavirus” in their names, 2% were malicious! That’s 400 brand new malicious websites created solely to take advantage of pandemic-related fear and curiosity.
If you didn’t believe us before, believe us now: it’s crucial to double-check links and avoid clicking links or downloading files from emails unless you’re quite sure it’s safe. If you want to stay apprised of the COVID-19 situation, seek out legitimate sources like the CDC’s website (www.cdc.gov). And, as always, stay vigilant!
Remote Desktop Protocol (RDP)
The second huge security flaw being taken advantage of in higher numbers since the COVID-19 outbreak is RDP. RDP is built into the Microsoft Windows
Windows operating system. It’s designed to enable someone, such as a tech support rep, IT person, or employer, to access and control a given computer remotely. To do this, RDP must be enabled on the system and the person attempting to access it must have the correct access credentials.
operating system. It’s designed to enable someone, such as a tech support rep, IT person, or employer, to access and control a given computer remotely. To do this, RDP must be enabled on the system and the person attempting to access it must have the correct access credentials.
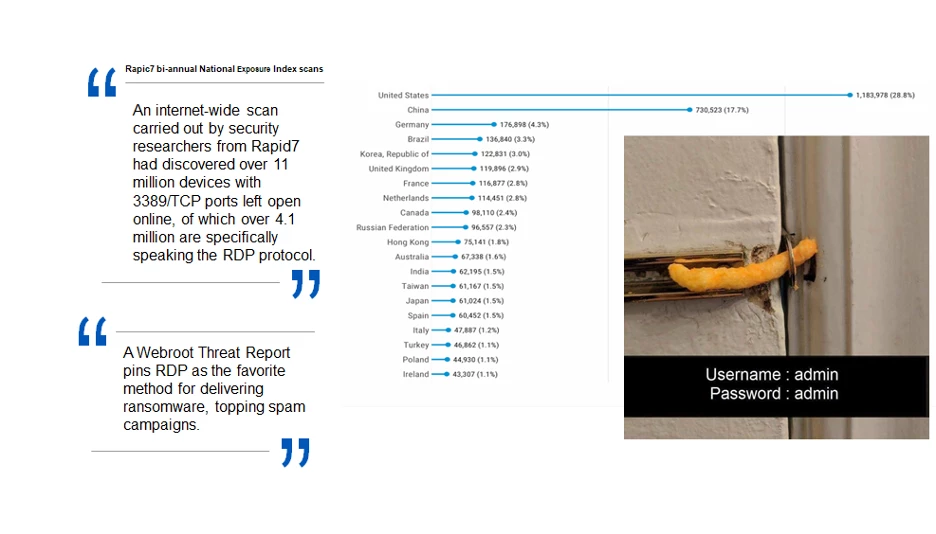
Since so many people are working from home right now, this utility is seeing a lot more use as employees access in-office machines from remote locations. Unfortunately, the default RDP methodology is pretty lacking in security features. When you enable this feature on a Windows machine, that system will automatically accept incoming RDP requests on TCP ports. The default port is 3389, but changing it doesn’t add any security. Computers using any TCP ports can easily be found using a free tool called Shodan, which can scan for internet-connected devices across the globe.
Once a criminal has scanned for your RDP-enabled computer, they can request a connection to it and the computer will accept and then ask for login credentials. This is where we’ll see another default RDP issue: UNLIMITED number of login attempts. Yes, you read that correctly. They get unlimited tries, no lockouts ever, and no alerts to any IT admins. This means criminals can just use brute force tools, like DuBrute, to break right in, no matter how good your credentials might be. (FYI: password cracking rigs can crack 15 characters in under 15 hours.)
Enabling RDP with default settings is akin to leaving the door to your computer and all of your data wide open. Once a criminal gains access to a machine, it’s Game Over from a security standpoint, since they can just disable/remove security and backup solutions to any malicious payloads they drop will have maximum damage. See below for stats on how widely used RDP has become.
Additionally, check out the growth of RDP use since the outbreak.
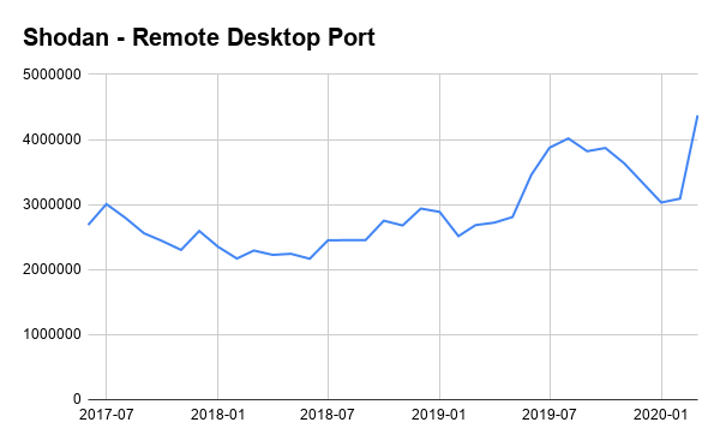
Long story short: the default method of enabling RDP is not secure. The mass migration to remote work has caused a dramatic increase in the use of this tool. Business and personal computers that have these TCP ports open are at a much higher risk of getting infected with ransomware or other malware.
What You Can Do
Remember, even with a powerful antivirus solution like Webroot, you should still maintain good security practices. No amount of security can protect you if you unwittingly open the door to cybercriminals.
1. Install reputable cybersecurity/antivirus on all your devices.
2. Always use caution when opening emails from unknown senders.
3. Be suspicious of messages that ask you to click a link, enter information, or download a file (when in doubt, just don’t do it!)
4. If a message uses fear tactics or tries to create a sense of urgency, watch out. This goes double for anything that mentions COVID-19.
5. If you’re not using it, make sure RDP is turned off. Not sure how to check? Contact your nearest IT person.
Stay safe, stay vigilant, use caution, and remind your colleagues and employers to do the same. That’s how we’ll get through this together.


