September 14, 2023

Image: Midjourney
Microsoft says an Iranian-backed threat group has targeted thousands of organizations in the U.S. and worldwide in password spray attacks since February 2023.
The state hackers also stole sensitive information from a limited number of victims in the defense, satellite, and pharmaceutical sectors.
Tracked as APT33 (aka Peach Sandstorm, HOLMIUM, or Refined Kitten), the cyber-espionage group has been active since at least 2013, attacking entities from various industry verticals (including government, defense, research, finance, and engineering) in the United States, Saudi Arabia, and South Korea.
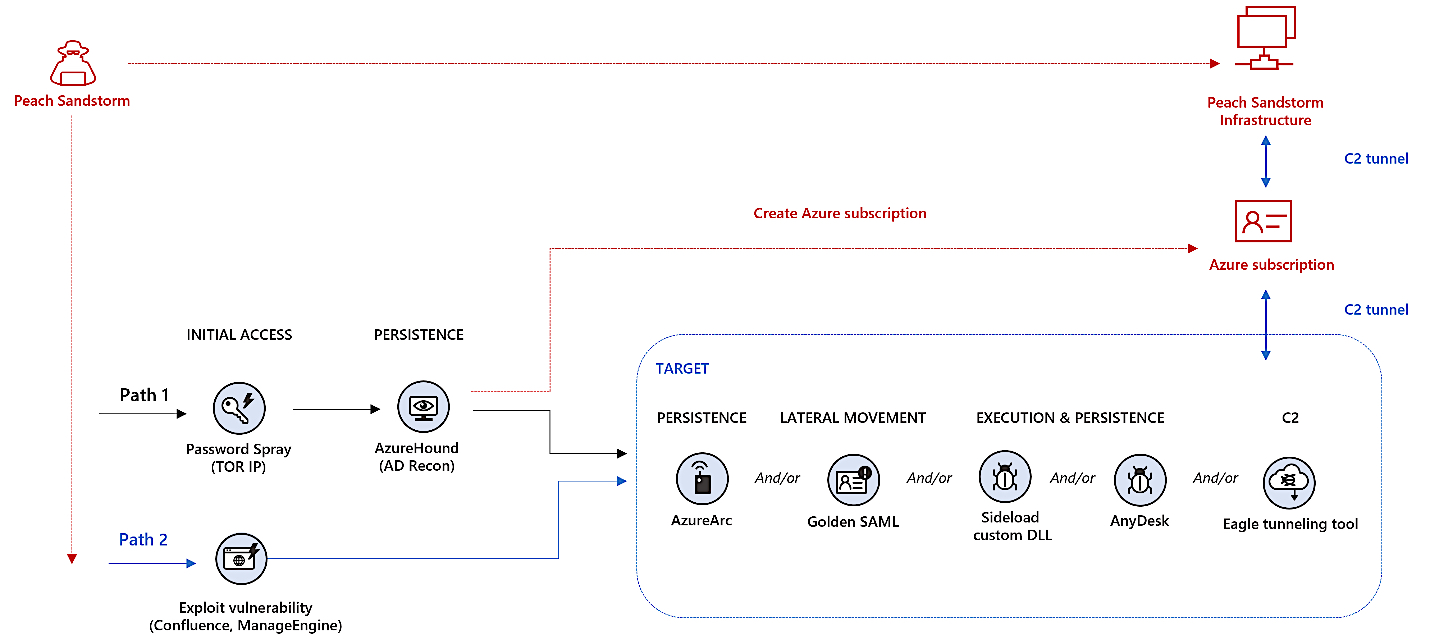
"Between February and July 2023, Peach Sandstorm carried out a wave of password spray attacks attempting to authenticate to thousands of environments," the Microsoft Threat Intelligence team said.
"Throughout 2023, Peach Sandstorm has consistently demonstrated interest in US and other country's organizations in the satellite, defense, and to a lesser extent, pharmaceutical sectors," Microsoft's Sherrod DeGrippo Threat Intelligence Strategy Director told BleepingComputer.
In password spray attacks, threat actors try to log in to many accounts using a single password or a list of commonly employed passwords.
This tactic differs from brute force attacks, where a single account is targeted with a long list of passwords. Password spraying enables attackers to significantly increase their chances of success while reducing the risk of triggering automatic account lockouts.
In contrast to noisy password spraying, the attackers also used exploits targeting unpatched Confluence and ManageEngine appliances exposed online to breach the targets’ networks.
Following successful attempts, the APT33 hackers used the AzureHound or Roadtools open-source security frameworks for reconnaissance across the victims' Azure Active Directory and to harvest data from their cloud environments.
They also used compromised Azure credentials, created new Azure subscriptions on the victims' tenants, or abused Azure Arc for persistence purposes to control on-premises devices within the victims' network.
The APT33 actors were also observed using Golden SAML attack techniques for lateral movement, deploying AnyDesk for persistence, sideloading custom malicious DLLs to execute malicious payloads, and employing a tunneling tool known as EagleRelay to tunnel malicious traffic to their command-and-control (C2) infrastructure.