March 18, 2024 By Bill Toulas

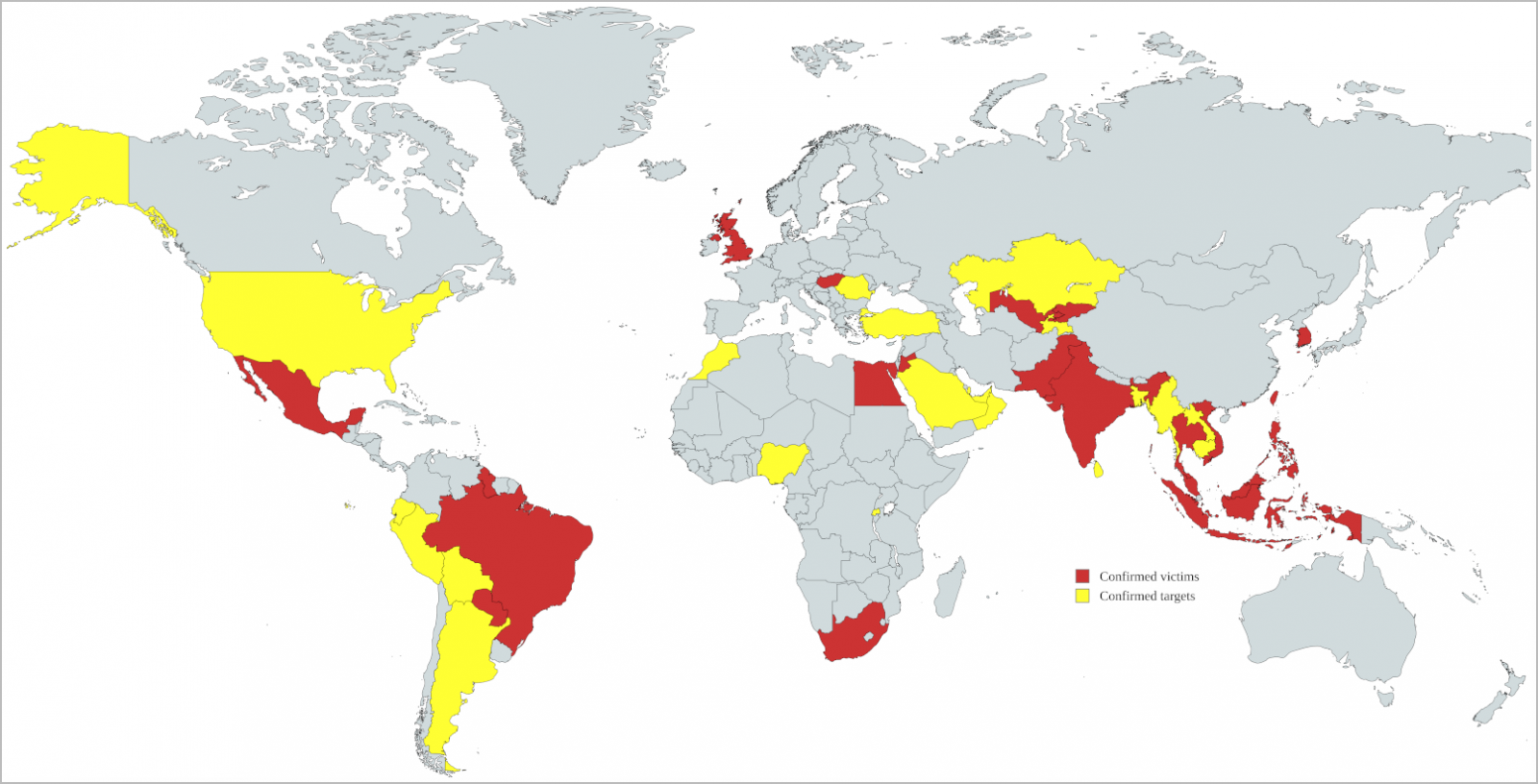
A sophisticated hacking campaign attributed to a Chinese Advanced Persistent Threat (APT) group known as 'Earth Krahang' has breached 70 organizations and targeted at least 116 across 45 countries.
According to Trend Micro researchers monitoring the activity, the campaign has been underway since early 2022 and focuses primarily on government organizations.
Specifically, the hackers have compromised 48 government organizations, 10 of which are Foreign Affairs ministries, and targeted another 49 government agencies.
The attackers exploit vulnerable internet-facing servers and use spear-phishing emails to deploy custom backdoors for cyberespionage.
Earth Krahang abuses its presence on breached government infrastructure to attack other governments, builds VPN servers on compromised systems, and performs brute-forcing to crack passwords for valuable email accounts.


