July 19, 2024 By Ionut Ilascu

A faulty component in the latest CrowdStrike Falcon update is crashing Windows systems, impacting various organizations and services across the world, including airports, TV stations, and hospitals.
The glitch is affecting Windows workstations and servers, with users reporting massive outages that took offline entire companies and fleets of hundreds of thousands of computers.
According to some reports, emergency services in the U.S. and Canada have also been impacted.
Workaround for CrowdStrike glitched update
For the past few hours, users have been complaining about Windows hosts being stuck in a boot loop or showing the Blue Screen of Death (BSOD) after installing the latest update for CrowdStrike Falcon Sensor.
The security vendor acknowledged the issue and published a technical alert explaining that its engineers “identified a content deployment related to this issue and reverted those changes.”
“Symptoms include hosts experiencing a bugcheck\blue screen error related to the Falcon Sensor,” CrowdStrike says in the tech alert.
The company revealed that the culprit is a Channel File, which contains data for the sensor (e.g. Instructions). Since it is just a component of the update for the sensor, this type of file can be addressed individually without removing the Falcon Sensor update.
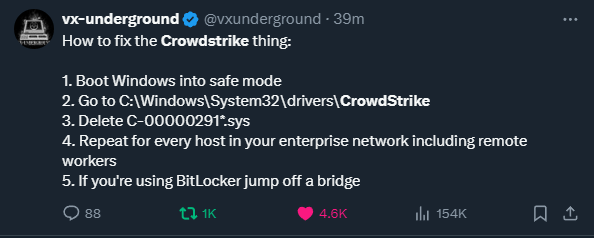
For those already affected, CrowdStrike provides the following workaround steps:
- Boot Windows into Safe Mode or the Windows Recovery Environment
- Navigate to the C:\Windows\System32\drivers\CrowdStrike directory
- Locate the file matching “C-00000291*.sys”, and delete it.
- Boot the host normally.