It is not yet clear what the attackers plan to do with their network of hijacked routers
A world-spanning network of hijacked home routers has been uncovered by security researchers.
The network involves more than 300,000 routers in homes and small businesses that have been taken over through loopholes in their core software.
Discovered by researchers at Team Cymru, the network is thought to be one of the biggest involving such devices.
It is not yet clear what the people behind the attack intend to do with the collection of compromised routers.
In a research paper describing its findings, Team Cymru said it had first seen routers from several different manufacturers being compromised in January 2014.
These first victims had been in Eastern Europe, but now most of the machines were in Vietnam with the rest scattered around Europe as well as a couple of other countries, said Team Cymru.
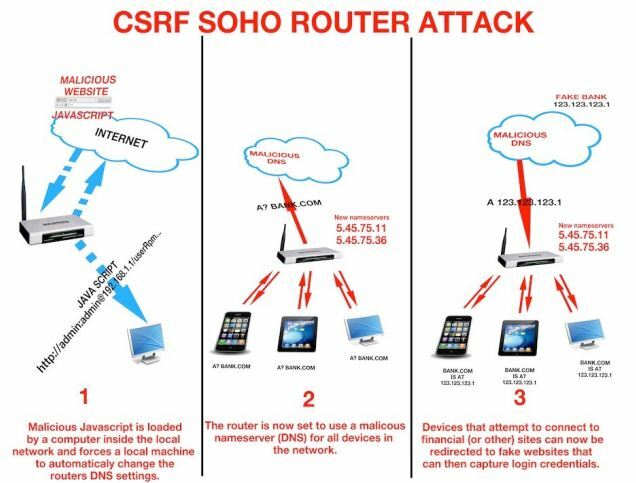
Once routers were taken over, internal instructions were changed so they no longer asked servers at their owner's ISP for help looking up the location of websites they regularly visit.
This would mean that the attackers could re-direct people to anywhere they wanted, inject their own adverts into web pages people visit or poison the search results they get.
Instead, these queries were routed through two IP addresses overseen by a hosting company in south London. That company has yet to respond to a request for comment.
Team Cymru researcher Steve Santorelli said the reason for creating the network of hijacked routers was still "mysterious" as the attackers did not seem to have abused their control for malicious ends.
The attack had some similarities with an incident seen in Poland, which involved hijacked home routers being re-directed to malicious websites controlled by hi-tech thieves keen to grab online bank login credentials, said Mr Santorelli.
"It's a definite evolution in technology - going after the internet gateway, not the end machine," Mr Santorelli told the BBC in an email. "We see these leaps in concepts every few years in cybercrime."
Team Cymru had contacted law enforcement about the attack and informed ISPs with a lot of compromised customers, he said.
Source
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.