Is this process safe? I’m running Windows 10. I’m having no issues but I’ve seen posts that this could be malicious, and I’ve seen posts that it is perfectly safe. Does this process indicate an infection or that Widows Defender is shut down?
Solved
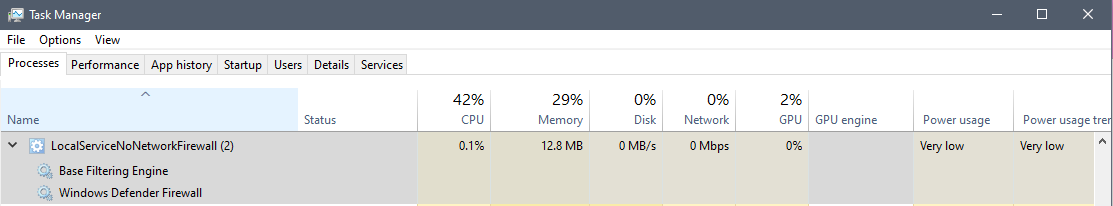
localservicenonetworkfirewall
 +1
+1Best answer by TripleHelix
Hello
I have it listed in Task Manager and I see no issues with it.
Click on picture to see full size:
If you want a free security check contact Webroot Support!
Webroot Support:
Call 1-866-612-4227
Note: When submitting a Support Ticket, Please wait for a response from Support. Putting in another Support Ticket on this problem before Support responses will put your first Support Ticket at the end of the queue.
Thanks,
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.





