Solved
notepad popup on desktop
A friends computer just started to get a notepad text file, ubxkpwpz.scr, popping up on the desktop on startup. It's linked to WebRoot, because if it doesn't run, webroot won't run. The full path for this is C:programfilesHWXOcFcMUBXkpwPZ.scr. Any one know why this started?
Best answer by Rakanisheu Retired
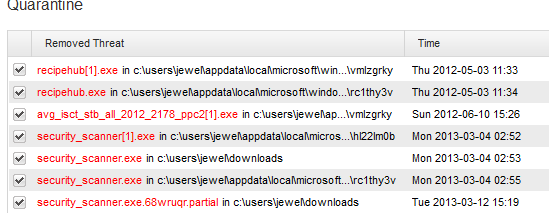
Confirmed its Webroot, thanks for the info. Webroot must have found something in its initial scan and radomised its install name and path.
Sorry to ask you to get the logs I just wanted to be sure.
WRSVC REG_SZ "C:Program FilesHWXOcFcMUBXkpwPZ.scr" -ul
Directory of C:Program FilesHWXOcFcM
12/27/2012 07:52 PM <DIR> .
12/27/2012 07:52 PM <DIR> ..
03/29/2013 02:09 PM 729,528 UBXkpwPZ.scr
File size, service name and time stamp are the correct.
View originalSorry to ask you to get the logs I just wanted to be sure.
WRSVC REG_SZ "C:Program FilesHWXOcFcMUBXkpwPZ.scr" -ul
Directory of C:Program FilesHWXOcFcM
12/27/2012 07:52 PM <DIR> .
12/27/2012 07:52 PM <DIR> ..
03/29/2013 02:09 PM 729,528 UBXkpwPZ.scr
File size, service name and time stamp are the correct.
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.