Hello,
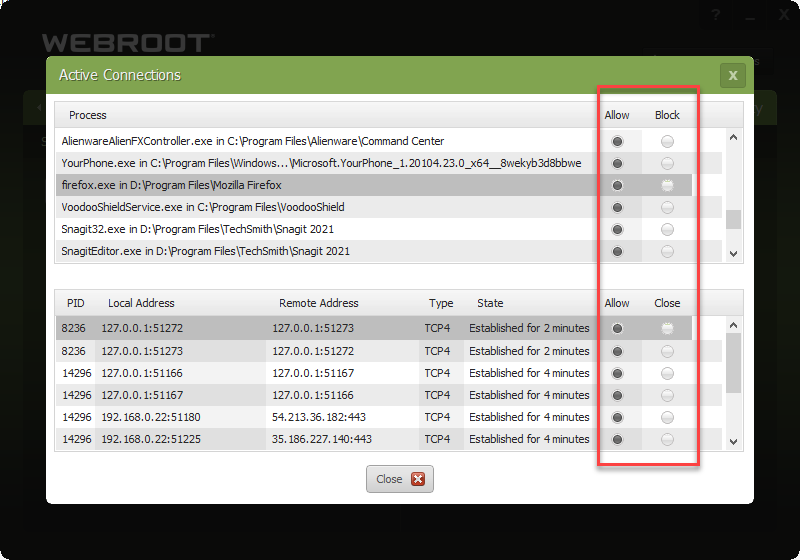
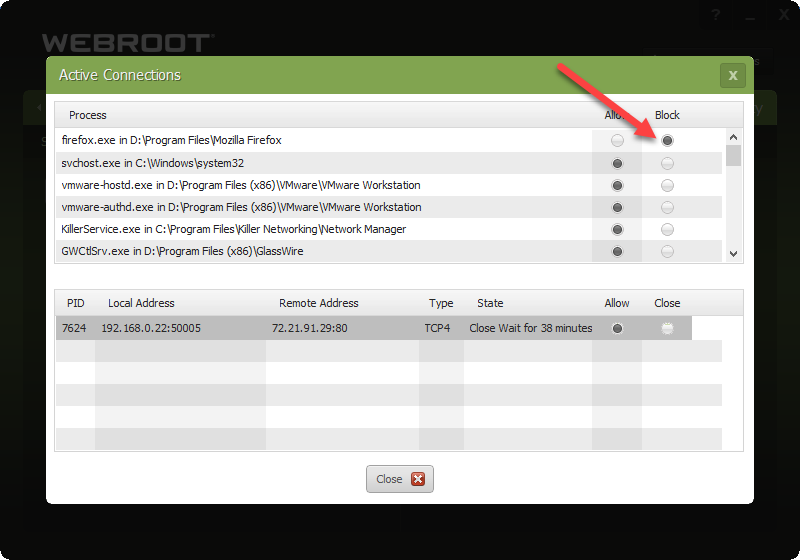
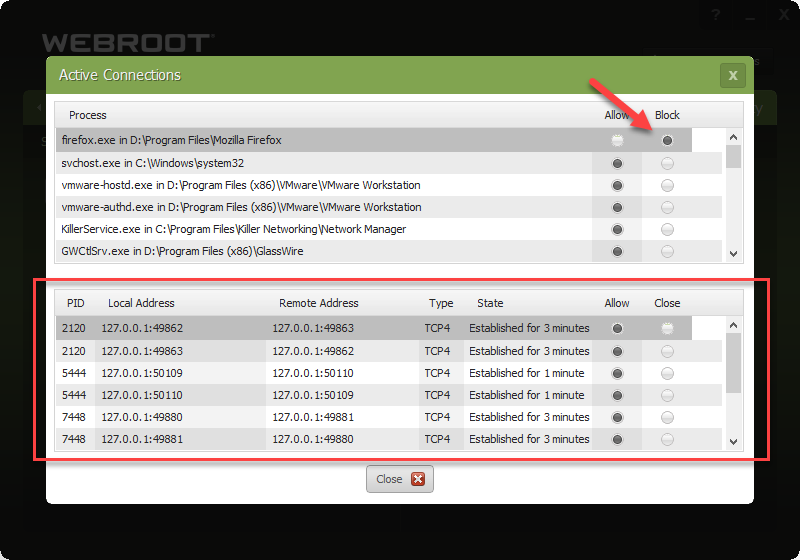
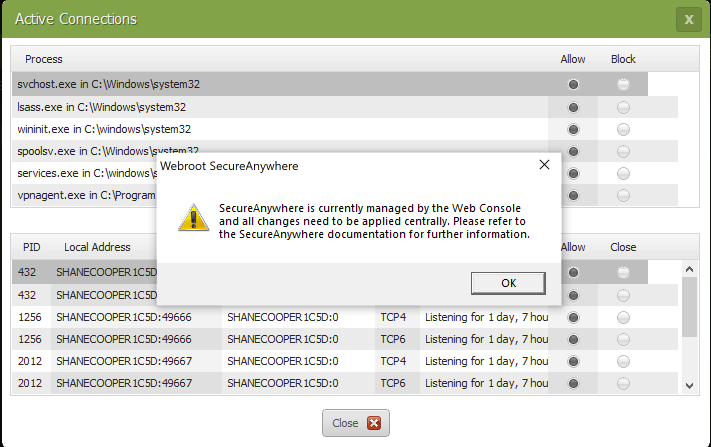
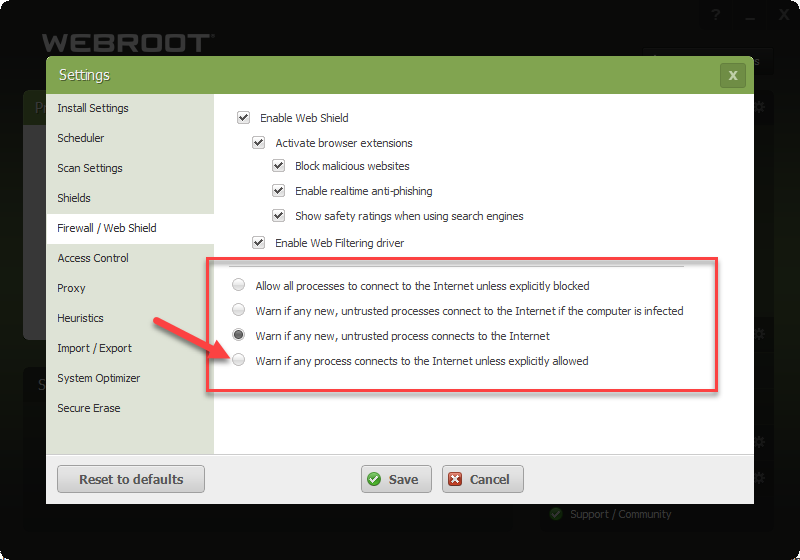
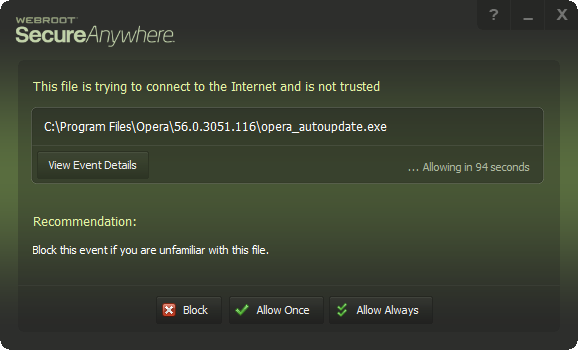
Discovered today that the latest build of Webroot on windows 10 computers don’t block any outgoing traffic, no matter what the settings are (allow or block). Also, the advanced settings the of firewall to block programs has no effect as well (I usually have it set to block all traffic unless explicitly allowed). Feel free to test yourself. Would love to know I’m not the only one (tested and broken on three different win 10 machines, works fine on two win 7 machines).
You been warned...