Hi,
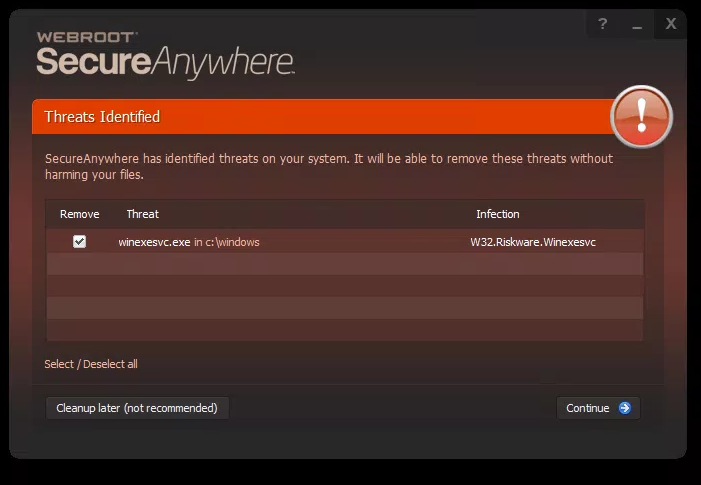
I'm seeing quite a few alerts detecting winexesvc.exe as w32.hack.tool.winexe this morning.
Is this a false positive - popped up on an otherwise not active PC after overnight's Windows updates?
Anyone else seeing this?
Edwin
Solved
winexecsvc.exe - false positive?
Best answer by JesseBropez
Hello 10d,
This file "winexesvc.exe" is related to the Windows Subsystem for Linux feature and allows remote commands to be sent to all systems in a network. Because of the enormous potential to be used maliciously, Webroot has classified this file malicious as it is potentially un-safe. If this program is needed in your environment, you may create an override and restore it from Webroot's quarantine via the Webroot Console.
For steps to override this file, please visit the link below.
http://live.webrootanywhere.com/content/1384/Creating-Whitelist-Overrides
Please let us know if we can explain anything in further detail.
Regards,
Jesse L.
Webroot Advanced Malware Removal Team
This file "winexesvc.exe" is related to the Windows Subsystem for Linux feature and allows remote commands to be sent to all systems in a network. Because of the enormous potential to be used maliciously, Webroot has classified this file malicious as it is potentially un-safe. If this program is needed in your environment, you may create an override and restore it from Webroot's quarantine via the Webroot Console.
For steps to override this file, please visit the link below.
http://live.webrootanywhere.com/content/1384/Creating-Whitelist-Overrides
Please let us know if we can explain anything in further detail.
Regards,
Jesse L.
Webroot Advanced Malware Removal Team
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.