A (Not Really) Brief History of Bitcoin and Monero
Note: this is the first installment in a 3-part post.
Bitcoin turned 10 years old this year and it’s only getting more and more exposure. Having invented the revolutionary internet technology known as “Blockchain”, Bitcoin has only been gaining hype ever since the first genesis block was mined into existence. At first, it started out is just a joke of an idea and websites would give bitcoins away for free just for visiting. This was back when the currency itself was worth next to nothing.
That all changed with the advent of Silk Road, an underground market on the encrypted dark web for buying and selling goods otherwise illegal or extremely difficult to purchase in most countries. The site’s buyers and sellers remained effectively anonymous to one another and were almost impossible to track. It’s usually criminals and hackers that test and prove the utility of new technologies before widespread adoption. Suddenly, people saw the real utility and application of a currency that could not be seized nor stopped in transaction. Bitcoins use began to flourish, and that continued even after the FBI shut down Silk Road in 2013.

A lot of people thought the Silk Road shutdown might be the end for Bitcoin, and its value tanked immediately afterward. But it quickly bounced back to surpass its greatest value so far.
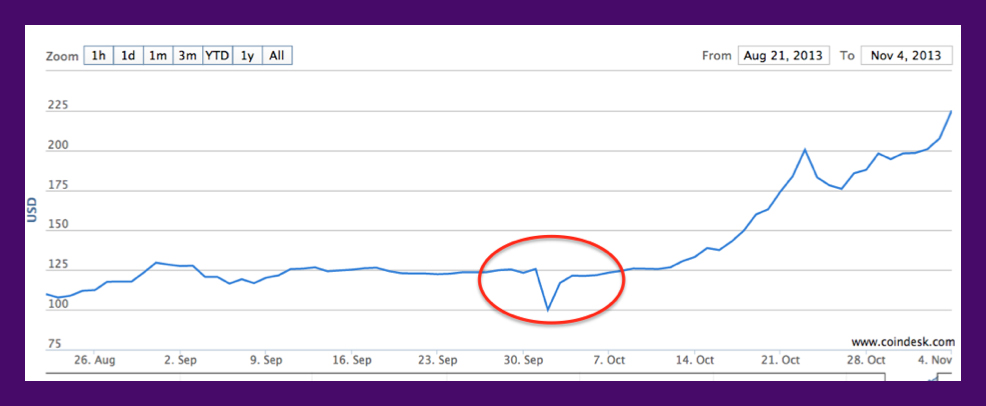
The cause of the Bitcoin resurgence: the original Cryptolocker. The first variants of Cryptolocker ransomware were seen in late September 2013. In terms of criminal business models, it was an instant success. Soon, many variants were infecting users around the world. With ransomware rapidly rising to the top of the threat landscape, Bitcoin saw corresponding growth as fiat currencies were exchanged so ransoms could be paid. That was when Bitcoin really gained traction beyond criminals and blockchain enthusiasts. It’s unfortunate, but part of Bitcoin’s increase in exposure was due to so many people being introduced to Bitcoin by being victims of ransomware infections themselves. Essentially, this forced adoption and enabled Bitcoin to flourish. Ransom demands, which typically scaled with the price, increased to over $1000 over the next few years, though the increase was hardly stead.

The volatility of Bitcoin probably wasn’t realized by most until 2017, which was when the infamous pump to almost $20,000 occurred. That was the turning point in exposure when pretty much everyone, even your grandparents, had heard of Bitcoin. The blockchain technology has also spawned many other cryptocurrencies, some of which have actual utility and some that were just exit scams. One of the most important to discuss is Monero.
Wherefore art thou, Monero?
Since all Bitcoin transactions are recorded on a public ledger, they are available for anyone to download and analyze. Each time a victim pays a ransom, they’re given a Bitcoin address to which to send payment. All transactions to and from this address are visible, which, incidentally, is how the success of many ransomware campaigns is measured. When a criminal wants to cash out their Bitcoin, they typically need to complete an exchange that involves personally identifiable information. So, if a criminal isn’t careful, their victim’s Bitcoin wallet address could be tracked all the way to the criminal’s exchange wallet address. Law enforcement could then subpoena the exchange to identify the criminal.
Criminals are often able to prevent getting caught in this situation by using tactics that prevent their “cash out” address from being flagged. For a time, Bitcoin “mixers” offered to launder coins that were widely available on the dark web. Their methods involved algorithms that would split up and send dirty coins of varying amounts to different addresses, then back to another address clean, a process not unlike physical currency laundering. But this process wasn’t foolproof and it couldn’t work indefinitely. Once cryptocurrencies had gained significant legitimate adoption, several projects were started to search Bitcoin blockchain transactions for fraudulent activities, such as Chainalysis.
In the spring of 2014, a new cryptocurrency arrived on the scene. Dubbed Monero, it’s basically a clone of Bitcoin, but with a huge difference: no public ledger. Monero quickly became criminals’ most useful payment system to date. It uses an innovative system of ring signatures and decoys to hide the origin of the transactions, ensuring transactions are untraceable. As soon as criminals receive payment to a Monero wallet address, they can send it to an exchange address and cash out clean, without needing to launder their earnings.
Monero is useful to criminals for a variety of reasons. It also has a proof-of-work mining system that maintains an ASIC resistance. Most cryptocurrencies use a proof-of-work mining system, but the algorithm used to mine them can be worked by a specific chip (ASIC) designed to hash that algorithm much more efficiently than the average personal computer. In this sense, Monero has created a niche for itself with a development team that maintains it will continually alter the Monero algorithm to make sure that it stays ASIC-resistant. This means Monero can be mined profitably with consumer-grade CPUs.

Learn more about the path of cryptocurrencies and the rise of cryptomining attacks in part 2 of this post.





