Business email compromise (BEC) attacks are still a top priority for threat actors. These attacks employ a variety of themes but one staple social engineering tactic we capture directly targets the relationships between title companies and the law firms with which they work closely. This is an attractive target because they are frequently transferring large sums of money for real estate transactions such as deposits, closings, final settlements, etc. Therefore, the spring season is an attractive time for these BEC threat actors to re-double their efforts in preparation with the usual spring surge in real estate purchase activity.
During these attacks and after phishing user credentials, the threat actors remain dormant within the compromised accounts awaiting the opportune moment to insert their own wire transfer or ACH details into an expected PDF file or directly into the email body. They do this to divert the money to their own accounts without anyone catching on until after the funds have been moved away.
One recent BEC example was sent from SendGrid servers and purported to originate from American Title. However, it contained a link to txlav[.]com where the phony closing disclosures documents were located.
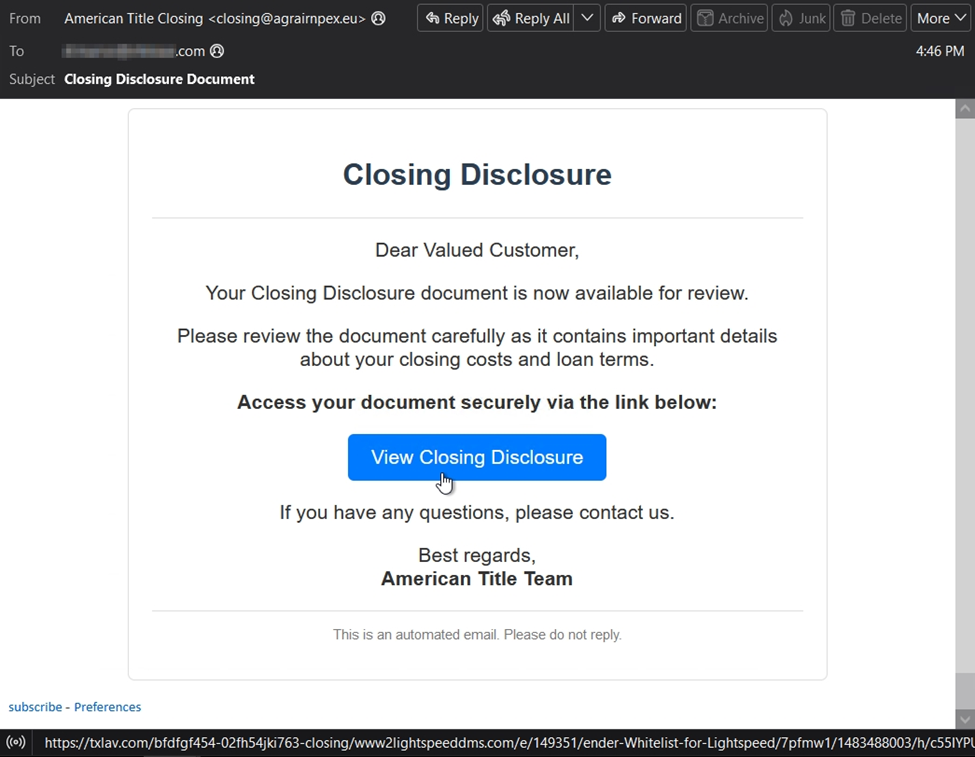
If the recipient clicks on the link, they are directed to the phishing site that prefills their email address using a customized URL within each message and solicits their email password.
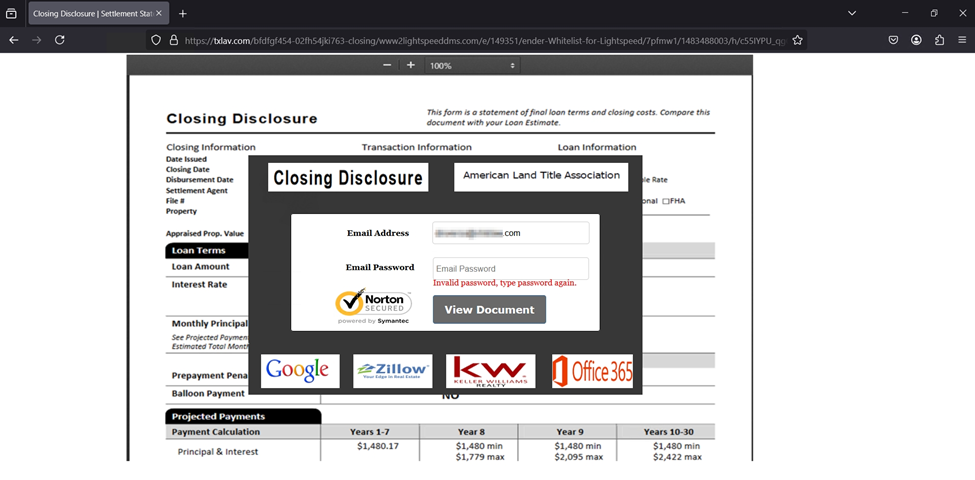
Another closing documents themed BEC attack we captured originated from OVH virtual private servers. It spoofed United Wholesale Mortgage and stated the recipient has received their final closing package that would need to be returned within 24 hours. The link was wrapped by Barracuda’s Link Protect service with the destination directing to the Beehiiv (Newsletter) platform, which is commonly abused to obfuscate phishing content. The obfuscated Beehiiv link both redirects the user post-click while simultaneously offering click-tracking metrics to the threat actors allowing them added telemetry into their attacks after they have been launched.
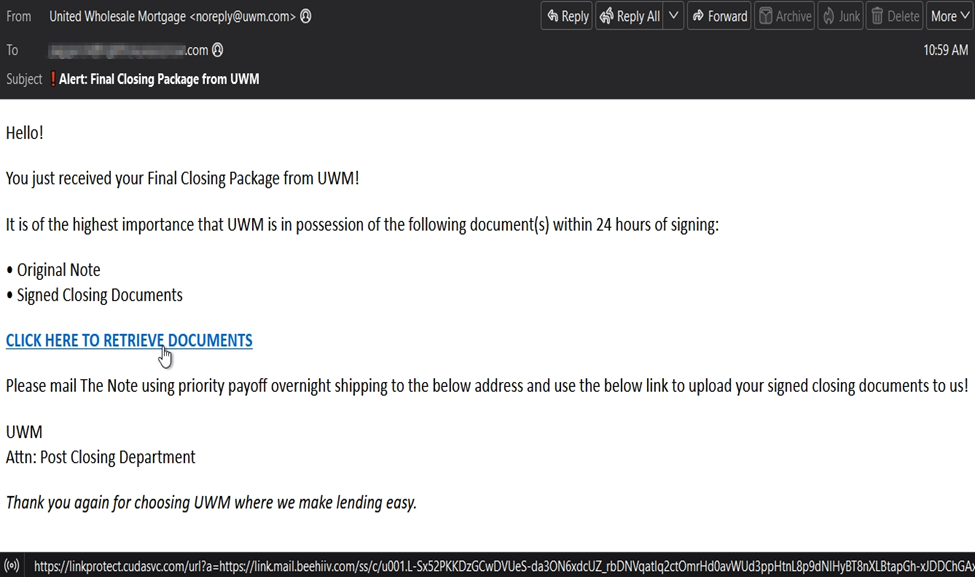
While most phishing sites soliciting user credentials and stealing session tokens are most commonly behind Cloudflare human verification measures, this attack used another solution, this unique hCaptcha.
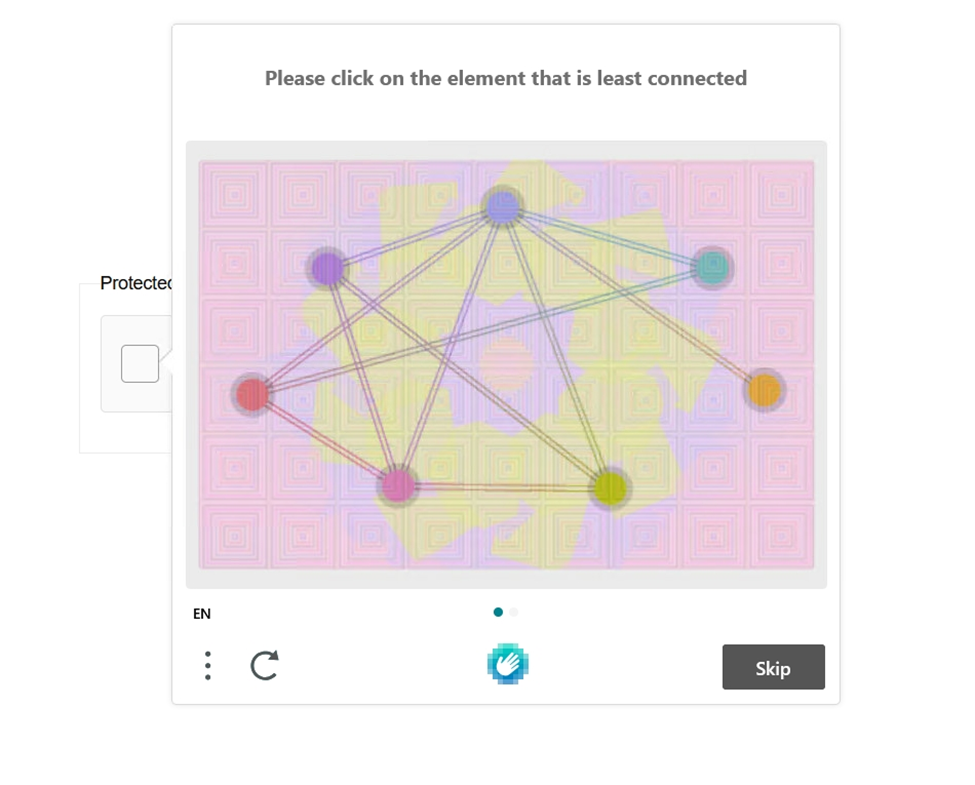
Upon verification, this attack led to a cloned Outlook Web Access sign in portal located at ocsubank[.]com, a look-a-like domain which they may be reusing from a prior or separate ongoing attack. It first attempts to automatically sign in the user by proxying and stealing any active 365 sessions but will then ask for a password if there is not an active session available.
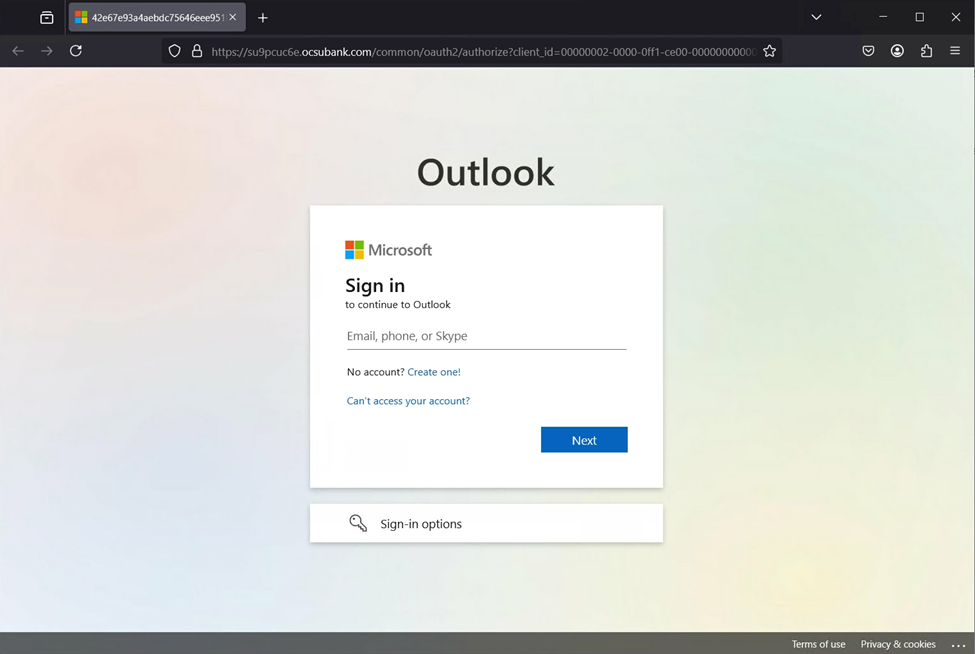
Spring is a busy time of year for threat actors as they look to step-up their compromise of all parties involved in real estate transactions. It is critical that you ensure that you do not click links in unsolicited email but also make sure you are utilizing two factor authentication. And in the case of large payments/wires it never hurts to pick up the phone confirm the payment details directly with the parties involved.




