Image-based phishing has been prevalent for years, but it has exploded in recent months, especially with the advent of Quishing (the unattractive term recently coined for QR code phishing). In these attacks the entire email body text is contained within the image itself, while the image also serves as a link to a malicious/phishing website. It also follows another popular trend we have recently observed in that it abuses Cloudflare’s CAPTCHA service to deter automated analysis.
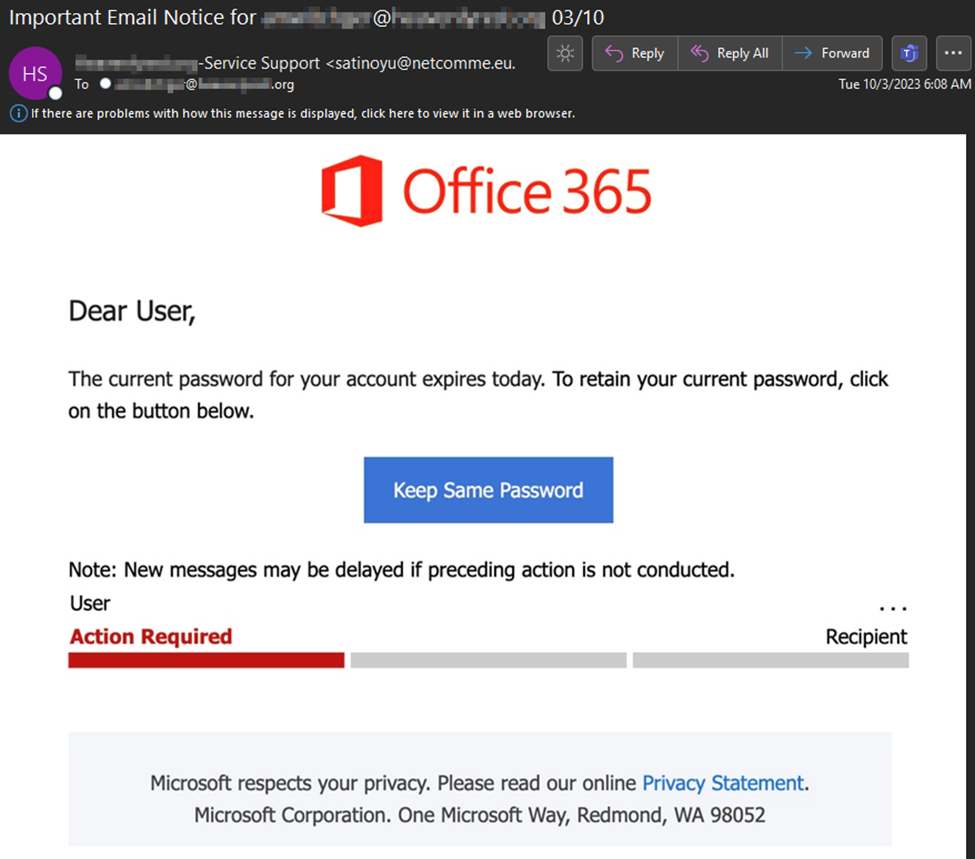
The image used in the following attack borrows some assets from legitimate Microsoft emails and induces a sense of urgency in the user claiming that their password expires today. The image link leverages Baidu[.]com which is often referred to as the “Google of China”. We have noticed a significant increase in phishing attacks leveraging this service for re-directs as it is typically viewed as benign in nature.
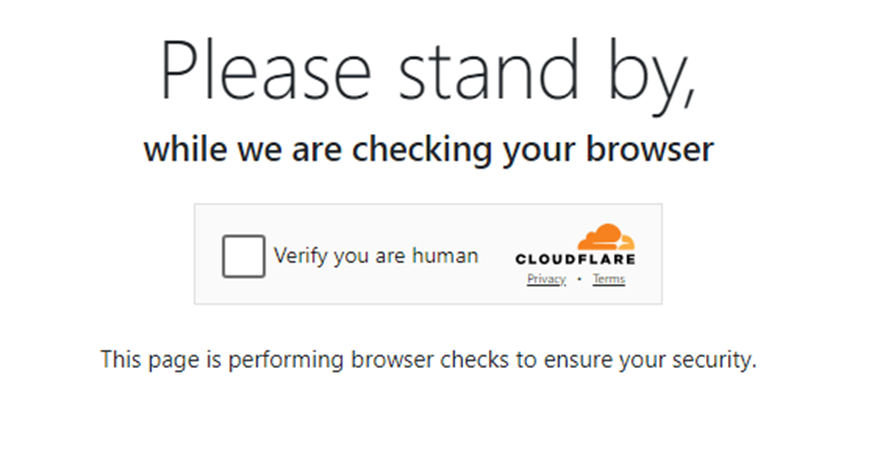
Clicking on the image first directs to this Cloudflare captcha page where the verification box just needs to be clicked.
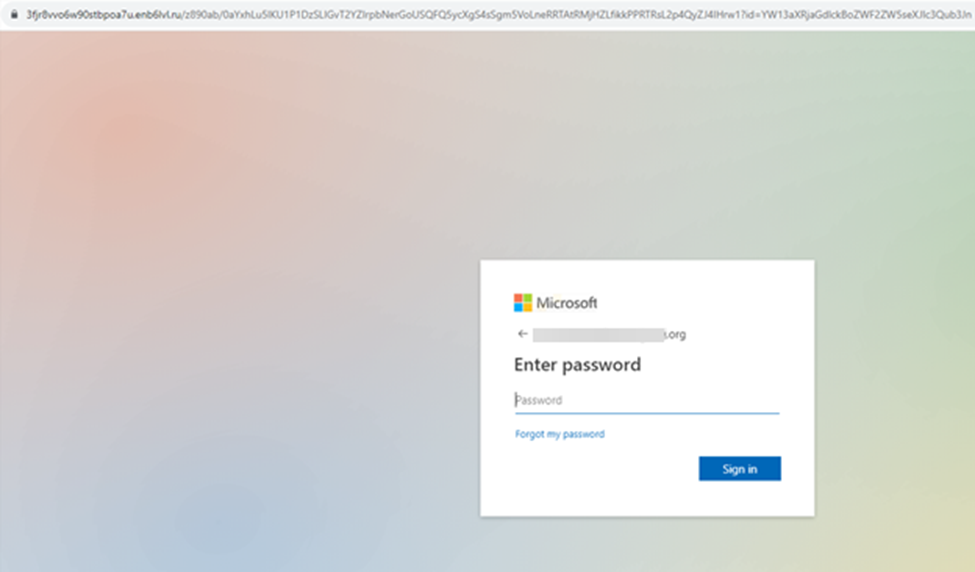
After the user verifies that they are human they are served the following Microsoft-branded credential harvesting page. Here the attacker will collect their credentials for future second-phase attacks.