March 5th, 2018 by Tamara Chuang of the Denver Post
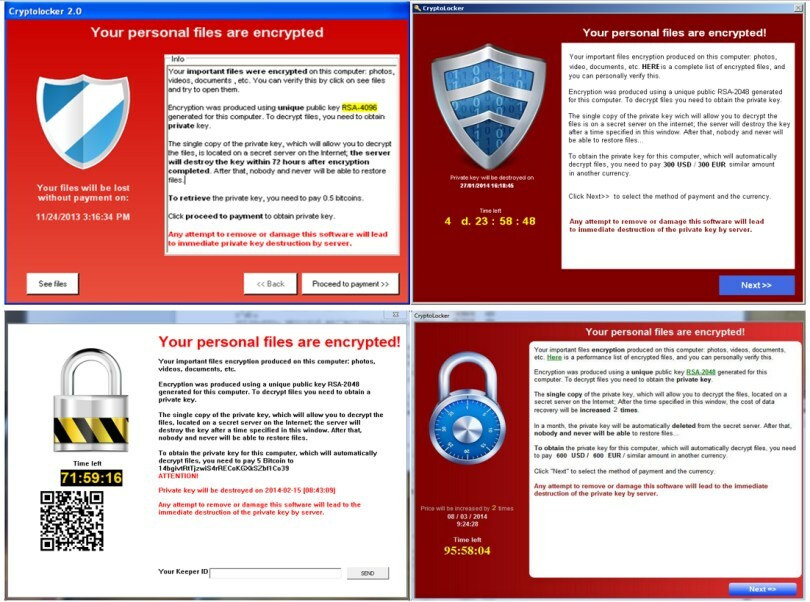
Last month, employees at the Colorado Department of Transportation were greeted by a message on their computer screens similar to this:
“All your files are encrypted with RSA-2048 encryption. … It’s not possible to recover your files without private key. … You must send us 0.7 BitCoin for each affected PC or 3 BitCoins to receive ALL Private Keys for ALL affected PC’s.”
CDOT isn’t paying, but others have. In fact, so-called ransomware has become one of the most lucrative criminal enterprises in the U.S. and internationally, with the FBI estimating total payments are nearing $1 billion. Hackers use ransomware to encrypt computer files, making them unreadable without a secret key, and then demand digital currency like bitcoin if victims want the files back — and many victims are falling for that promise.
To better understand how ransomware works and how it has spread so effectively, The Denver Post talked with Broomfield anti-malware company Webroot, which got its start in the late 1990s cleansing computer viruses from personal computers.
“The end goal is just to put ransomware on the computer because right now the most successful way for cybercriminals to make money is with ransoming your files,” said
Read the rest of the article on the Denver Post.
What would you do? Would you pay to get your files back? What are the steps you take to keep yourself safe?
Let us know in the comments below!