Web Shield Upgrade - December 2016
Chrome Browser Behaviors at Installation Overview:
On November 28, 2016, we released a no-cost upgrade to the Web Threat Shield that integrates the BrightCloud® Threat Intelligence Services used by over 40 other network and security vendors. The upgrades include real-time web categorization and web reputation filtering, real-time anti-phishing, improved web search ratings and website blocking notifications. These upgrades significantly improve secure web usage for all Webroot SecureAnywhere Business Endpoint Protection users and are part of our commitment to continuously enhancing the overall efficacy and functionality of our solutions to mitigate multiple threat vectors.
- NEW: Integrates Webroot BrightCloud® Web Classification and Reputation into web browser support.
- NEW: Integrates Webroot BrightCloud® Real-Time Anti-Phishing Service.
- NEW: Search result annotations for Google, Bing, and Yahoo search engines.
- NEW: Enhanced Block Page informs with policy controlled options for users.
Webroot has ensured that the Web Threat Shield upgrade is as silent as possible. However, Internet browsers can operate very differently from each other and offer different experiences when managing third party installations. Therefore customers operating particular browsers may see requests to accept a new Webroot extension. This document describes the expected behaviors when installing the Web Threat Shield Chrome browser extension.
Forced Installation of the Chrome extension for the Enhanced Web Threat Shield
Webroot follows Google and the Chromium Projects best practice concerning Browser Extension deployment. Webroot therefore cannot deploy Browser Extensions ‘silently’ or without notification to an end user. Customers or Partners wishing to install Chrome browser extensions ‘silently’ in managed environments may do so using the following method(s) for enforced installation.
Enforced installation of the Chrome extension for Enhanced Web Threat Shield (EWTS) for Webroot SecureAnywere in managed environments can be achieved easily. Enforced installation will not prompt the user to activate or accept the extension, and also prevents the user from disabling it.
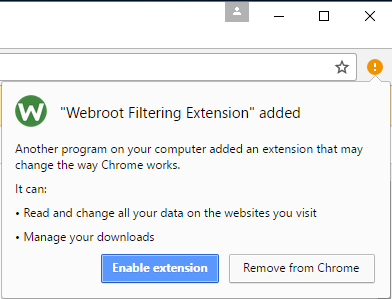
In a non-enforced environment, the user will be prompted to enable the extension for Chrome as depicted in Figure 1 below.
Figure 1: Notification after regular installation.
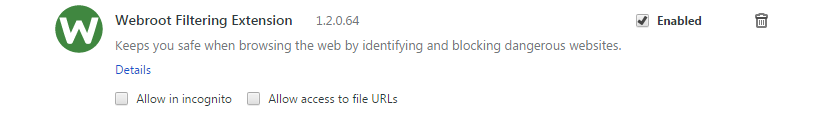
A non-enforced extension can, by design, be enabled, disabled or removed by the user via chrome://extensions/ as shown in Figure 2.
Figure 2: Regular installed extension.
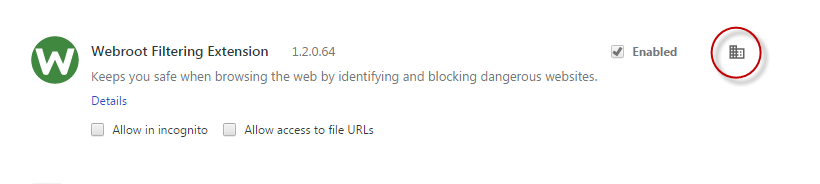
Chrome extensions, which are deployed silently in managed environments, are marked as shown in Figure 3. The user in this scenario cannot disable or remove the extension himself, this is controlled by the administrator. Note that there will not be any user prompts for enabling the extension.
Figure 3: Enforced installed extension (without notification to the user).
Option 1: Using Active Directory Group Policies
Google provides administrative templates for Windows Server 2003 (ADM template) and Windows Server 2008+ (ADMX template) which, once imported, will provide Chrome specific policies for Group Policies.- Required administrative templates can be downloaded from Google via below link:Zip file of Google Chrome templates and documentation
- Open the Group Policy Management console.
- Right click your domain and select Create and Link a GPO here. [img]https://sw.nohold.net/Webroot/Images/webshieldupgradedec2016_img4.png[/img] Figure 4: Group Policy Management console.
- Name your new GPO (in this example it is called Chrome Enforced Policy).
- Right click your new GPO and select Edit. You should get a new window as shown below. [img]https://sw.nohold.net/Webroot/Images/webshieldupgradedec2016_img5.png[/img] Figure 5: Select Policy for editing.
- Expand the Computer Configuration.
- Right-click Administrative Templates.
- Click on Add/Remove Templates. [img]https://sw.nohold.net/Webroot/Images/webshieldupgradedec2016_img6.png[/img] Figure 6: Add a template.
- Click Add.
- Point to the ADM or ADMX file from the Google Chrome templates archive you downloaded in Step 0. [img]https://sw.nohold.net/Webroot/Images/webshieldupgradedec2016_img7.png[/img] Figure 7: Downloaded ADM file.
- Click Open and then click Close.
- You should now see Google as an additional folder inside the Administrative Templates.
- Inside the Administrative Templates please expand Google > Google Chrome > Extensions. [img]https://sw.nohold.net/Webroot/Images/webshieldupgradedec2016_img8.png[/img] Figure 8: Expanded view of Google > Google Chrome > Extensions.
- Click on Configure the list of force-installed extensions.
- 14. Click Enable.
- 15. Click Show.
- 16. Add the line of text below to the list of Extension/App IDs and update URLs to be silently installed. kjeghcllfecehndceplomkocgfbklffd;https://clients2.google.com/service/update2/crx [img]https://sw.nohold.net/Webroot/Images/webshieldupgradedec2016_img9.png[/img] Figure 9: Dialog to add the extension for enforced installation
- Confirm all dialogs/buttons.
Option 2: Using Google Suite to Force Install a Single Custom App
Enforced installation of the Chrome extension for EWTS is supported on Google Suite managed environments. General directions for installing extensions and applications can be found in Google Help.To install the Chrome extension for the EWTS you will need to add a Custom App using the following steps:
- Sign in to the Google Admin console.
- From the Admin console dashboard, click Device management.
- On the left, click Chrome management.
- Click App management.
- On the right click the three dots to bring up the overflow menu. [img]https://sw.nohold.net/Webroot/Images/webshieldupgradedec2016_img10.png[/img] Figure 10: Overflow menu.
- Select Add custom app.
- In the custom app dialog enter the ID kjeghcllfecehndceplomkocgfbklffd and URL https://clients2.google.com/service/update2/crx for Webroot Filtering Extension and click ADD. [img]https://sw.nohold.net/Webroot/Images/webshieldupgradedec2016_img11.png[/img] Figure 11: Add custom app details.
- From the App Management screen select the newly added extension identified by the ID. [img]https://sw.nohold.net/Webroot/Images/webshieldupgradedec2016_img12.png[/img] Figure 12: App Management.
- From the app options select User Settings. [img]https://sw.nohold.net/Webroot/Images/webshieldupgradedec2016_img13.png[/img] Figure 13: App Settings.
- Select the relevant Org you wish to install the Chrome extension for EWTS into and turn Allow installation and Force installation ON. [img]https://sw.nohold.net/Webroot/Images/webshieldupgradedec2016_img14.png[/img] Figure 14: User Settings for Org.
- Click SAVE.
Please note: At this time we do not support Webroot SecureAnywhere on Chromebooks. In order to avoid a poor experience for users running on these devices you will need to utilize policy control within G Suite, please refer to the G Suite help documentation for more information.
Option 3: Using Registry
If deployment options 1 or 2 are not suitable, using the Windows Registry might be an alternative to silently install the Chrome extension for the EWTS. Note that this option requires the computers to be part of a Microsoft Windows Domain.Warning: Using this method might conflict with Active Directory Group Policies or G Suite managed environments.
Details about available policy settings for Chrome can be found at:
http://dev.chromium.org/administrators/policy-list-3#ExtensionInstallForcelist
Use the Windows Registry Editor (regedit.exe) to:
- Check whether the Registry key listed below exists. [HKEY_LOCAL_MACHINESOFTWAREPoliciesGoogleChromeExtensionInstallForcelist] Existence of this key may indicate that other management applications are enforcing Chrome policies, specifically forced installation of extensions, which can cause conflicts if below steps are continued.
- Add the following Registry value: Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINESOFTWAREPoliciesGoogleChromeExtensionInstallForcelist] "1"="kjeghcllfecehndceplomkocgfbklffd;https://clients2.google.com/service/update2/crx" In case you wish to register additional extensions, please ensure continuous numbering.