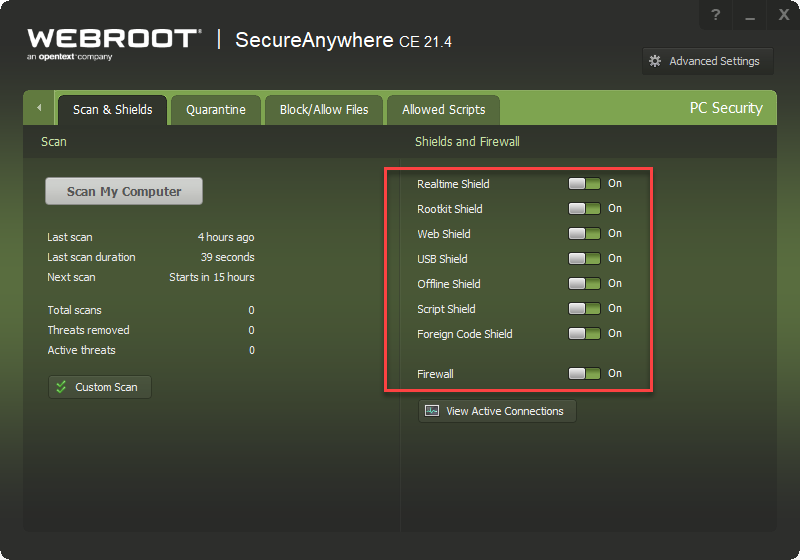
I recently switched over to Webroot for my personal machines, and joined this community. While I am a software developer of many years, there's a lot I don't understand about cyber security in general. Here’s something specific…
If you already have a rootkit unknowingly installed on your Windows machine, and the rootkit is smart enough to expect and trick Webroot, then the only way Webroot can defeat it, is to boot itself from independent start-up media (USB flash drive), then scan & quarantine/disable the rootkit before your OS can start from the Windows boot drive.
But all I was required to do after purchasing, is download and install. It started up, scanned, and detected no issues. But how could Webroot be so sure it's not being tricked or defeated in some way? I could find no "boot-from-start-up-media-and-scan" options for this product.
Thanks for your patience.
Scott.