Announcing the NEW Webroot Community
Hello Webroot Community!
We have some BIG Community news!
We've been working tirelessly for months on bringing you an entirely new online community experience. This means the new Webroot Community will get a brand-new design, site speed upgrades, functionality, and so much more.
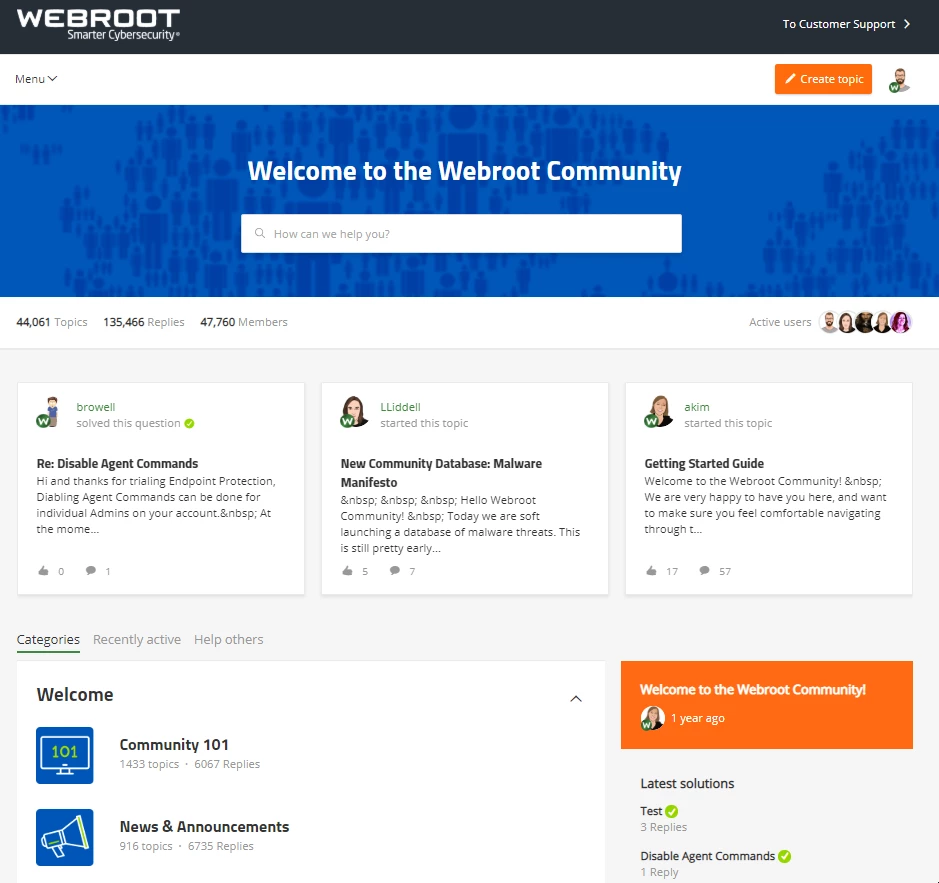
Follow this thread as we’ll update you with more as soon as we can. For now, check out a sneak peek of the new homepage, what do you think?
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.